Experience the power of the Zero Trust Segmentation Platform
One platform. One console. Any environment.
Protect workloads and devices with the first platform for breach containment

.png)
.png)
.png)
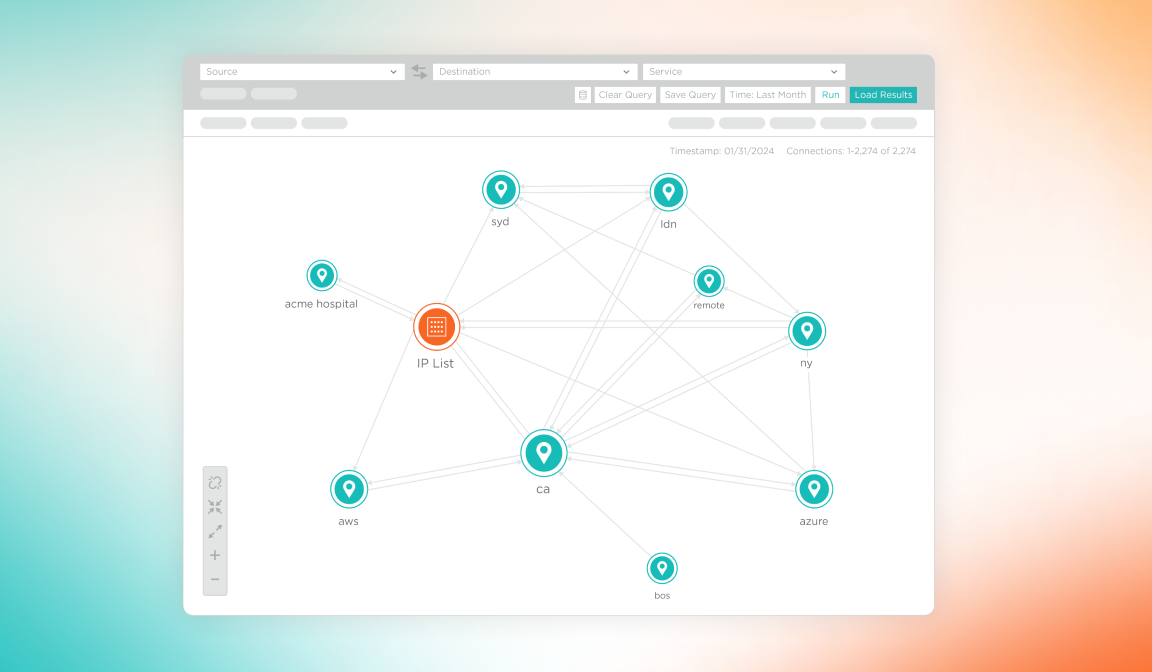
See risk
See risk by visualizing all communication and traffic between workloads and devices across the entire hybrid attack surface.
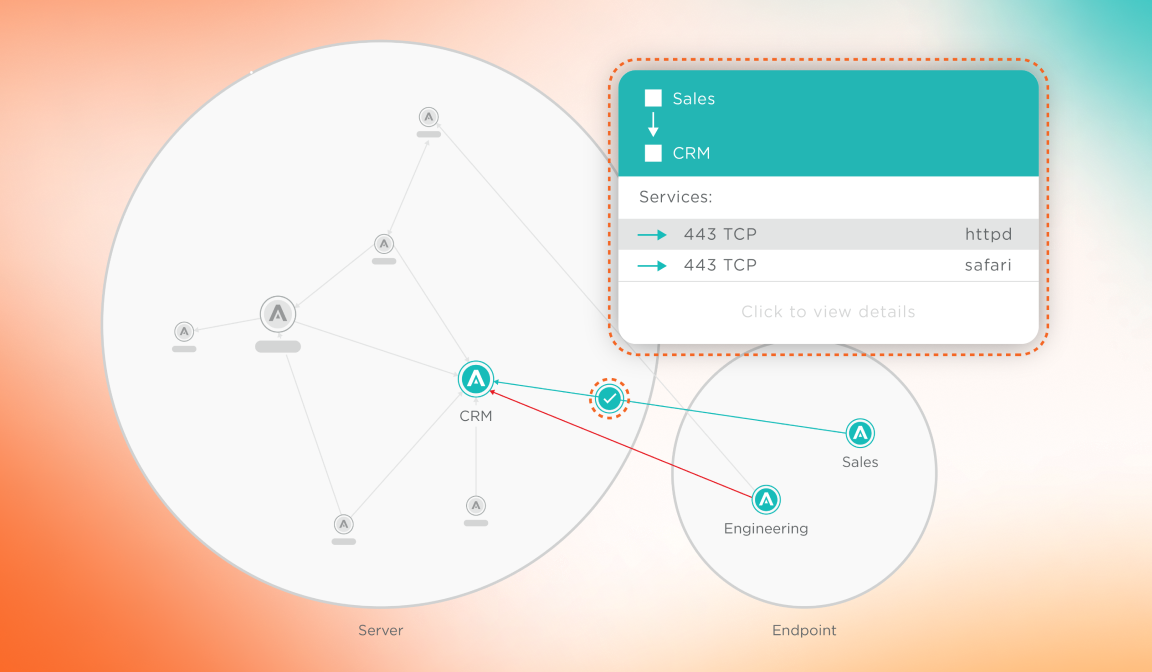
Set policy
With every change, automatically set granular and flexible segmentation policies that control communication between workloads and devices to only allow what is necessary and wanted.
Stop the spread
Proactively isolate high-value assets or reactively isolate compromised systems during an active attack to stop the spread of a breach.
The Illumio ZTS Platform
Aligned with your top cybersecurity initiatives
Enable Zero Trust
- Maintain continuous, risk-based verification
- Enforce least-privilege access
- Gain comprehensive security monitoring
Contain ransomware in minutes
- Stop ransomware from spreading
- Identify areas of high risk
- Build long-term protection
Strengthen cyber resilience
- Quickly quarantine compromised systems
- Implement granular controls to limit scope of attacks
- Speed response with automated alerts
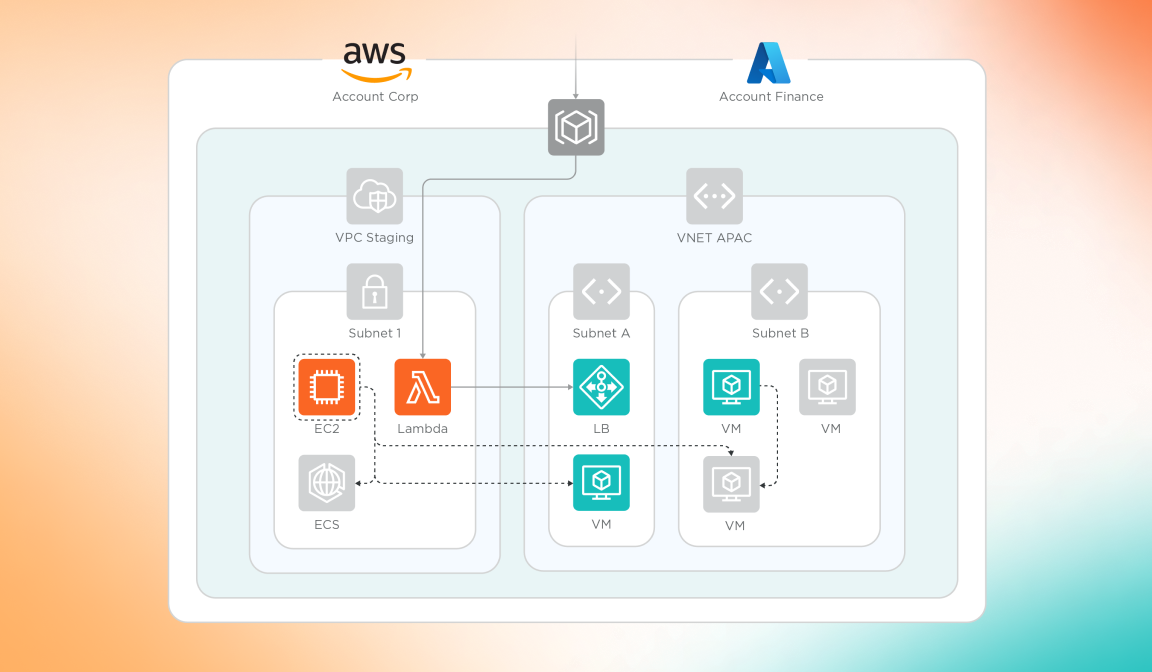
Cloud security made easy
- Identify risk by assessing current traffic patterns
- Tighten security controls with rule recommendations
- Protect data during cloud migration projects