그림자 추적은 이제 그만: 일루미오 인사이트를 통한 더 스마트한 위협 헌팅
오늘날 공격자들은 빠르게 움직입니다. 그리고 AI의 도움으로 그 어느 때보다 더 은밀하게 활동할 수 있습니다.
기존의 탐지 도구는 종종 분석가에게 알림을 넘치게 합니다. 올바른 맥락이 없으면 그림자를 쫓는 것과 같습니다.
위협 헌팅은 공격자가 환경 전체로 확산되기 전에 침해 징후를 선제적으로 검색하는 기능입니다.
일루미오 인사이트는 여기서 한 걸음 더 나아갑니다. 워크로드 간 및 워크로드 간 인터넷 트래픽에 대한 심층적인 가시성을 제공함으로써 방어자는 다른 도구가 놓치는 부분을 파악할 수 있습니다.
인사이트는 위협 헌터가 오탐을 쫓는 대신 실제 공격 경로를 신속하게 찾아내어 중요 리소스로 확산되기 전에 침해를 차단할 수 있도록 지원합니다.
최신 위협 헌팅의 과제
공격자는 점점 더 정교해지는 반면, 방어자는 여전히 경계 가시성이 충분하다는 생각과 같은 낡은 가정에 의존하고 있습니다.
하이브리드 인프라와 끊임없이 확장되는 클라우드 워크로드의 세계에서 기존의 접근 방식으로는 한계가 있습니다.
그렇다면 무엇이 방해가 될까요? 이러한 일반적인 문제점은 효과적인 위협 헌팅을 어렵게 만듭니다:
- 동서 사각지대: 대부분의 도구는 남북 경계 트래픽에 초점을 맞추기 때문에 측면 이동은 보이지 않습니다.
- 하이브리드, 멀티 클라우드의 복잡성: AWS(Amazon Web Services), Microsoft Azure, GCP(Google Cloud Platform), OCI(Oracle Cloud Infrastructure) 및 온프레미스 워크로드가 혼합되어 있으면 상호 연관성을 파악하기 어려울 수 있습니다.
- 알림 피로: 우선순위가 충분하지 않은 신호가 너무 많으면 팀은 알림에 시달리게 됩니다.
- 느린 조사: 데이터 사일로는 도구 간에 끝없는 피벗을 강요하여 응답 속도를 늦춥니다.
이러한 문제는 단순히 조사 속도를 늦추는 데 그치지 않습니다. 이는 공격자가 악용할 수 있는 위험한 사각지대를 만들어냅니다.
최신 위협에 대응하기 위해 보안팀은 더 스마트한 가시성, 더 긴밀한 통합, 측면 이동을 찾아내고 억제하는 더 빠른 방법이 필요합니다.
일루미오 인사이트가 위협 헌팅을 간소화하는 방법
일루미오 인사이트는 AWS, Azure, GCP, OCI, 온프레미스 환경, 방화벽, VPN 등으로부터 플로우 로그를 수집합니다. AI 보안 그래프를 사용하여 모든 연결(허용 또는 거부)을 한 곳에서 매핑합니다.
위협 헌터로서 인사이트 허브를 사용하면 네트워크의 모든 리소스와 통신하는 악성 IP, 외부 데이터 전송, 환경 내 고위험 서비스 등 환경에 대한 모든 위협을 확인할 수 있습니다.
다음은 한 가지 예입니다:
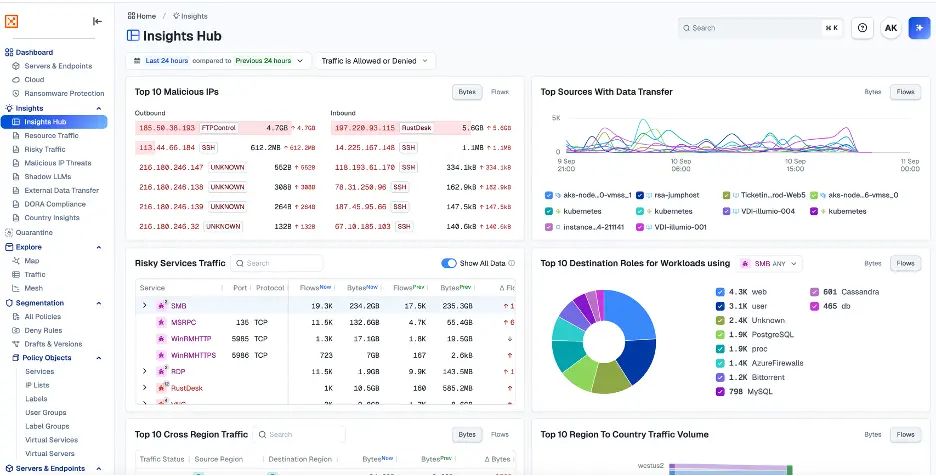
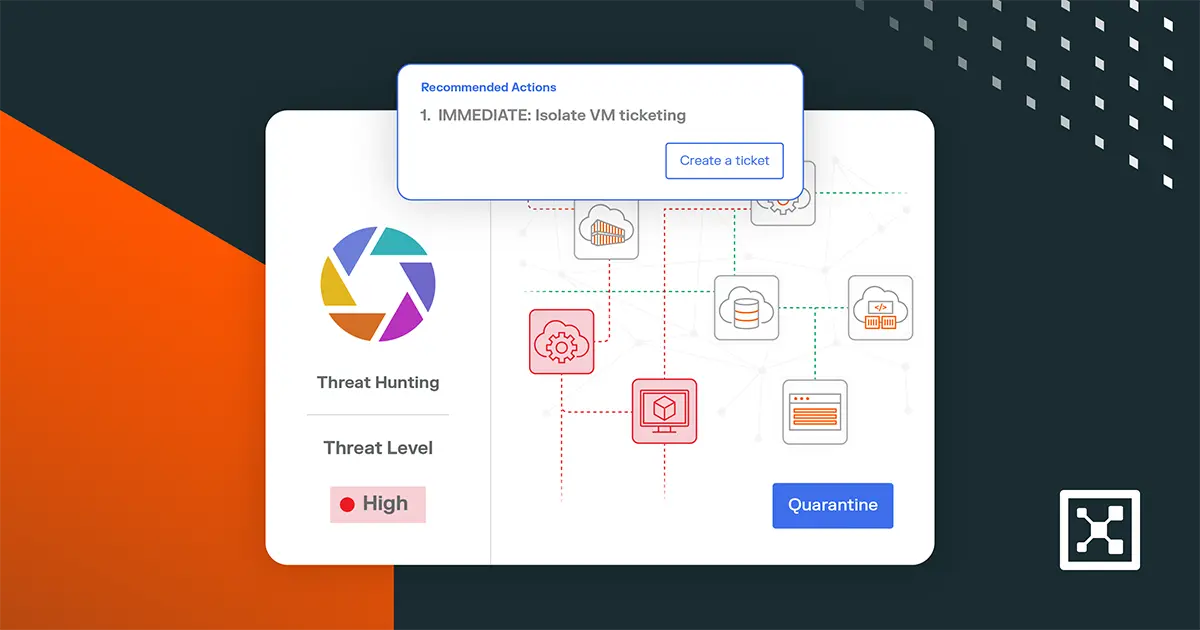
대시보드에서 헌터들은 이상 징후를 빠르게 발견할 수 있습니다. 예를 들어, 악성 IP로부터의 러스트데스크 트래픽이 갑자기 급증하는 것이 눈에 띕니다.
연결 세부 정보를 살펴보면 악성 IP와 내부 가상 머신(VM) 간에 지속적인 러스트데스크 트래픽이 발생하는 것을 확인할 수 있습니다.
이 패턴은 단순한 일회성 프로브가 아닙니다. 공격자가 환경 내에서 활성 원격 세션을 설정했음을 나타냅니다.
.webp)
러스트데스크 자체는 본질적으로 나쁘지 않지만, 알려진 악성 IP가 이를 통해 연결되면 경보음이 울립니다. 위협 헌터는 몇 번의 클릭만으로 공격자의 경로를 추적할 수 있습니다:
- 공격자는 먼저 환경을 매핑하고 광범위한 리소스를 발견할 때까지 스캔하고 조사합니다. 여기에는 많은 조직에서 매일 사용하는 중요한 PaaS 서비스가 포함됩니다.
- 이 탐사 과정에서 그들은 환경의 가장 소중한 자산을 보호하는 중요한 자격 증명과 비밀을 저장하는 주요 금고를 발견하고 액세스 권한을 얻습니다.
- 이렇게 탈취한 키로 무장한 공격자는 고객 기록으로 가득 찬 데이터베이스, 고가의 스토리지 계정, 핵심 애플리케이션을 지원하는 캐싱 계층 등 미션 크리티컬 시스템을 체계적으로 공격합니다.
- 공격자는 이러한 자산을 제어하여 민감한 데이터를 외부로 유출할 수 있는 경로를 설정합니다. 그들은 감시망을 피하기 위해 자신의 통제하에 있는 외부 저장소 계정으로 데이터를 전송합니다.
.webp)
이 시점에서 헌터는 공격을 확인하는 데 그치지 않고 Illumio Insights의 원클릭 격리를 통해 공격을 차단할 수 있습니다. 이 기능을 사용하면 위협 헌터가 손상된 워크로드를 즉시 격리하여 나머지 환경 또는 외부 대상과 통신하지 못하도록 차단할 수 있습니다.
이 기능을 강력하게 만드는 것은 속도입니다. 별도의 방화벽 콘솔로 이동하거나 수동으로 변경할 때까지 기다릴 필요가 없습니다. 즉시 격리됩니다.
또한 Illumio는 격리된 시스템에 대한 제어된 액세스를 제공하기 때문에 관리자와 보안 운영 센터(SOC) 팀은 추가 확산의 위험 없이 로그인하여 조사, 포렌식 수집, 문제 해결을 계속할 수 있습니다.
즉, 위협 헌터는 공격 경로를 시각화하여 실시간으로 차단할 수 있습니다.

포렌식은 격리에서 끝나지 않습니다. 과거 흐름 데이터를 통해 헌터에게 물어볼 수 있습니다:
- 이 워크로드가 악성 IP와 처음 통신한 시점은 언제인가요?
- 얼마나 많은 데이터가 전송되었나요?
- 다른 워크로드에서도 동일한 의심스러운 동작이 발생하나요?
이러한 컨텍스트는 조사 속도를 높이고 우선순위를 명확히 하며 대응을 강화합니다.
일루미오 인사이트: 사후 대응에서 사전 예방적 방어로의 전환
위협 헌팅은 단순히 악의적인 행위자를 잡는 것만이 아닙니다. 또한 위험을 줄이고 확산되기 전에 측면 이동을 막는 것이기도 합니다.
일루미오 인사이트를 통해 보안팀은 사일로화된 알림에서 상황별 공격 경로 가시성으로 전환할 수 있습니다. 즉,
- 모든 데이터를 한곳에 모아 더욱 빠르게 조사하세요.
- 실제 공격 경로를 기반으로 더욱 스마트하게 우선순위를 지정합니다.
- 통합 격리를 통한 강력한 대응.
- 하이브리드 및 멀티 클라우드 환경 전반의 확장성.
방어자는 노이즈에 휩쓸리는 대신 실행 가능한 인텔리전스를 확보하고 공격자보다 한 발 앞서 대응할 수 있습니다.
시도 일루미오 인사이트 14일 무료 체험판 오늘.