Illumio Segmentation
Secure critical assets, workloads, and devices across your hybrid, multi-cloud environment. See risk, set policy, and prevent lateral movement with the Zero Trust leader.
Modern segmentation for modern networks
Traditional security tools weren’t built for hybrid, multi-cloud environments. Illumio Segmentation applies the principles of Zero Trust to stop lateral movement and increase cyber resilience.
Segmentation, simplified
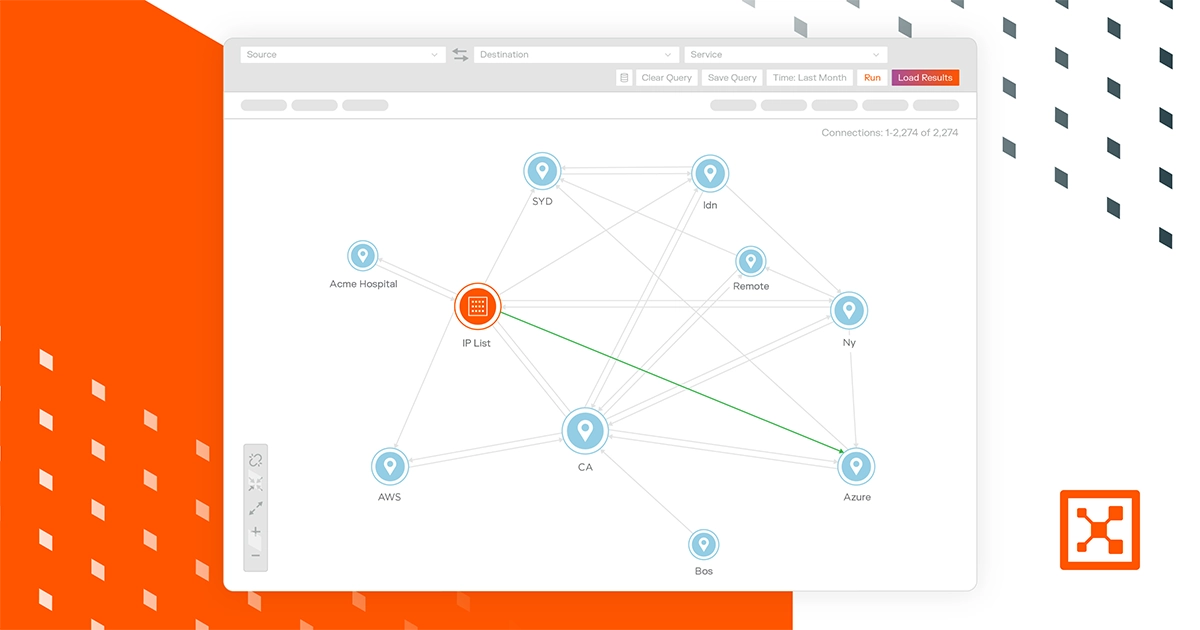
Illumio Segmentation combines real-time telemetry with AI to recommend policies instantly and accelerate security decision-making.

Consistent, automated segmentation for all workloads across clouds, endpoints, and data centers. Segmentation that scales with you.

Segmentation is a pillar of Zero Trust. Enforce least-privilege access and eliminate implicit trust across your hybrid multi-cloud environment.

One solution. Every environment.
Cloud
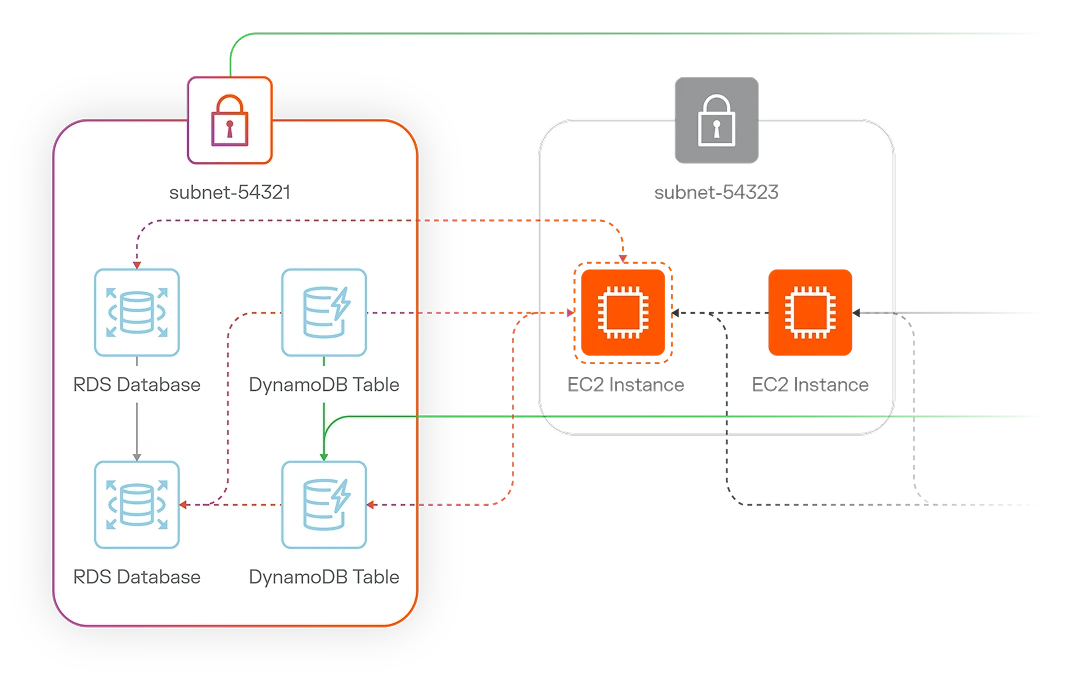
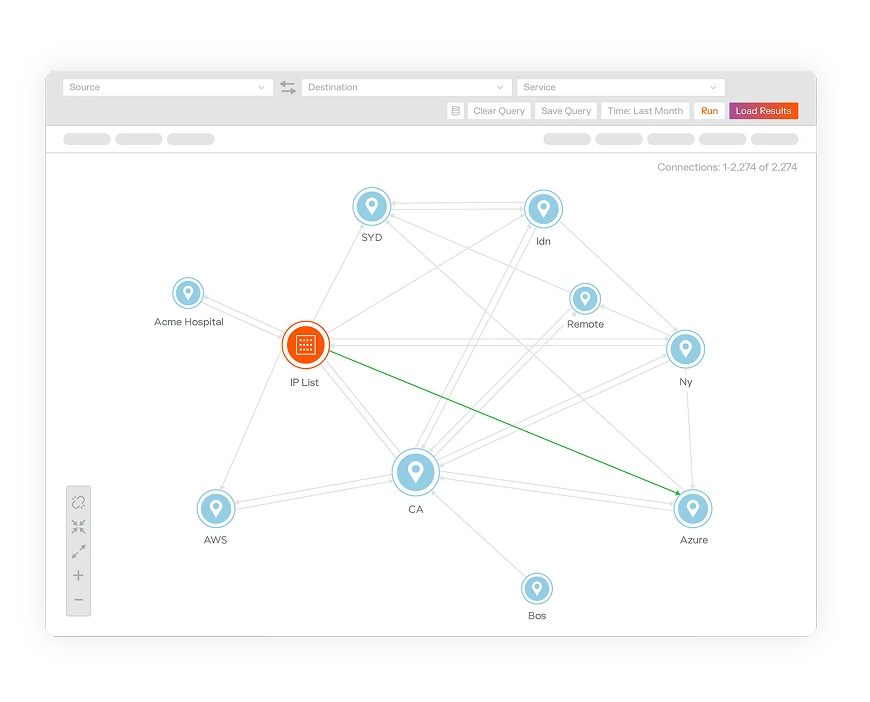
Visualize cloud application deployments, resources, traffic flows, and metadata. Build consistent, dynamic segmentation across hybrid, multi-cloud environments and containers. Contain cloud attacks at their source.
Endpoint
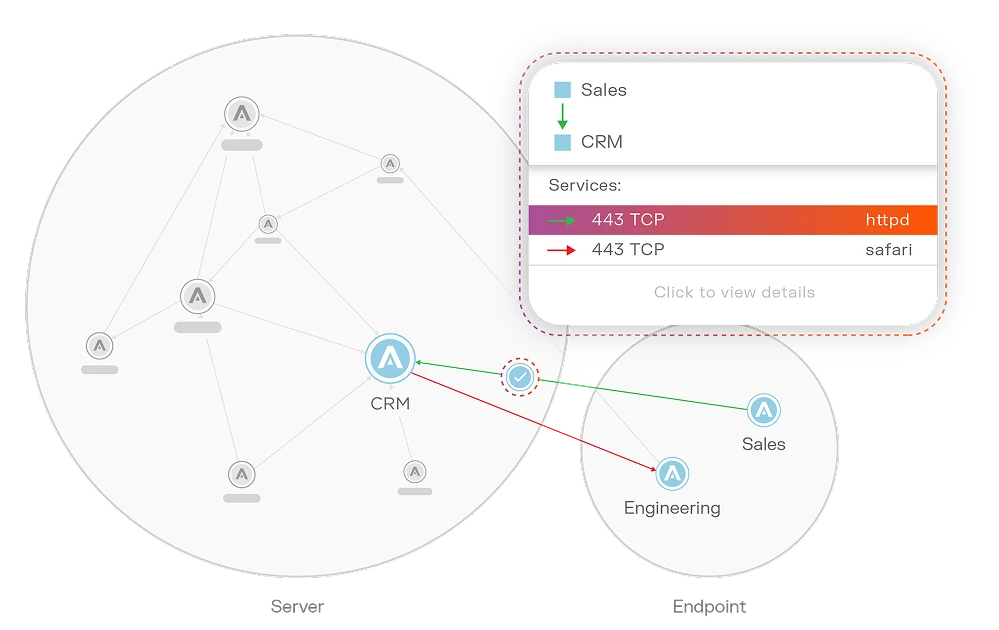
See endpoint traffic everywhere. Control application access. Contain breaches to a single workstation, laptop, or virtual machine — even before it’s detected by other security tools.
Data center
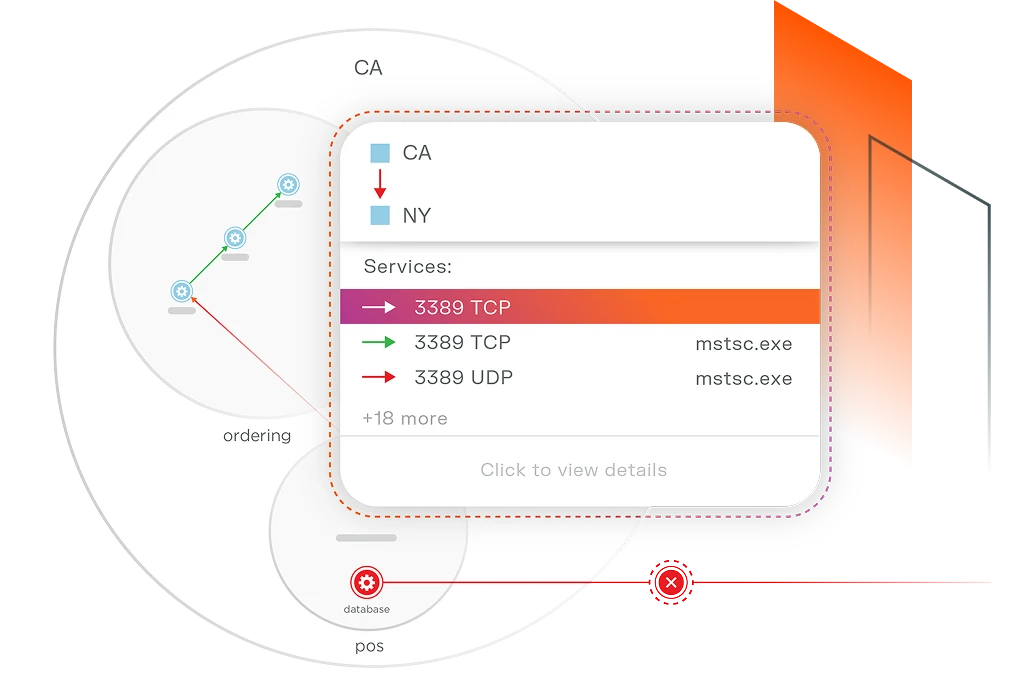
See all traffic across data centers, containers, IT/OT, and virtual machines. Segment workloads without disrupting operations. Contain the breach — regardless of architecture, size, or complexity.
%20(1).webp)


Oracle NetSuite protects flagship business applications with Illumio Segmentation