Security solutions for every role
Find out how Illumio’s breach containment platform can transform your networking security environment.
Ease complexity, unify protection across environments, and close critical gaps.

Expose real threats, reduce false positives, and show impact with every investigation.

The world’s first breach containment platform
Powered by an AI security graph and made for Zero Trust. Identify and contain threats across hybrid, multi-cloud environments. Stop attacks before they become disasters.



Illumio Named a 2024 Forrester Wave Leader in Microsegmentation
See why segmentation is critical for containing today’s threats.
.png)

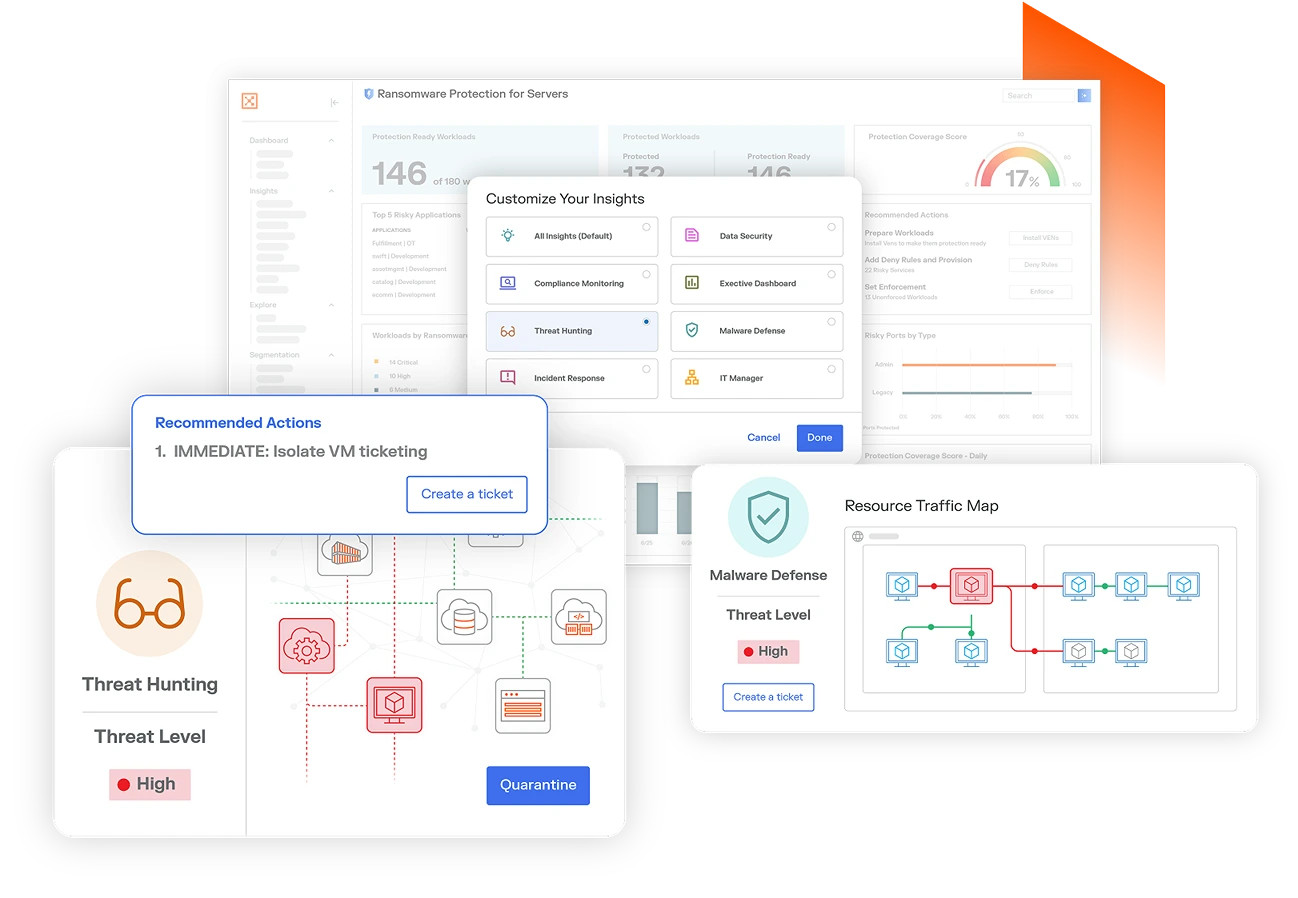
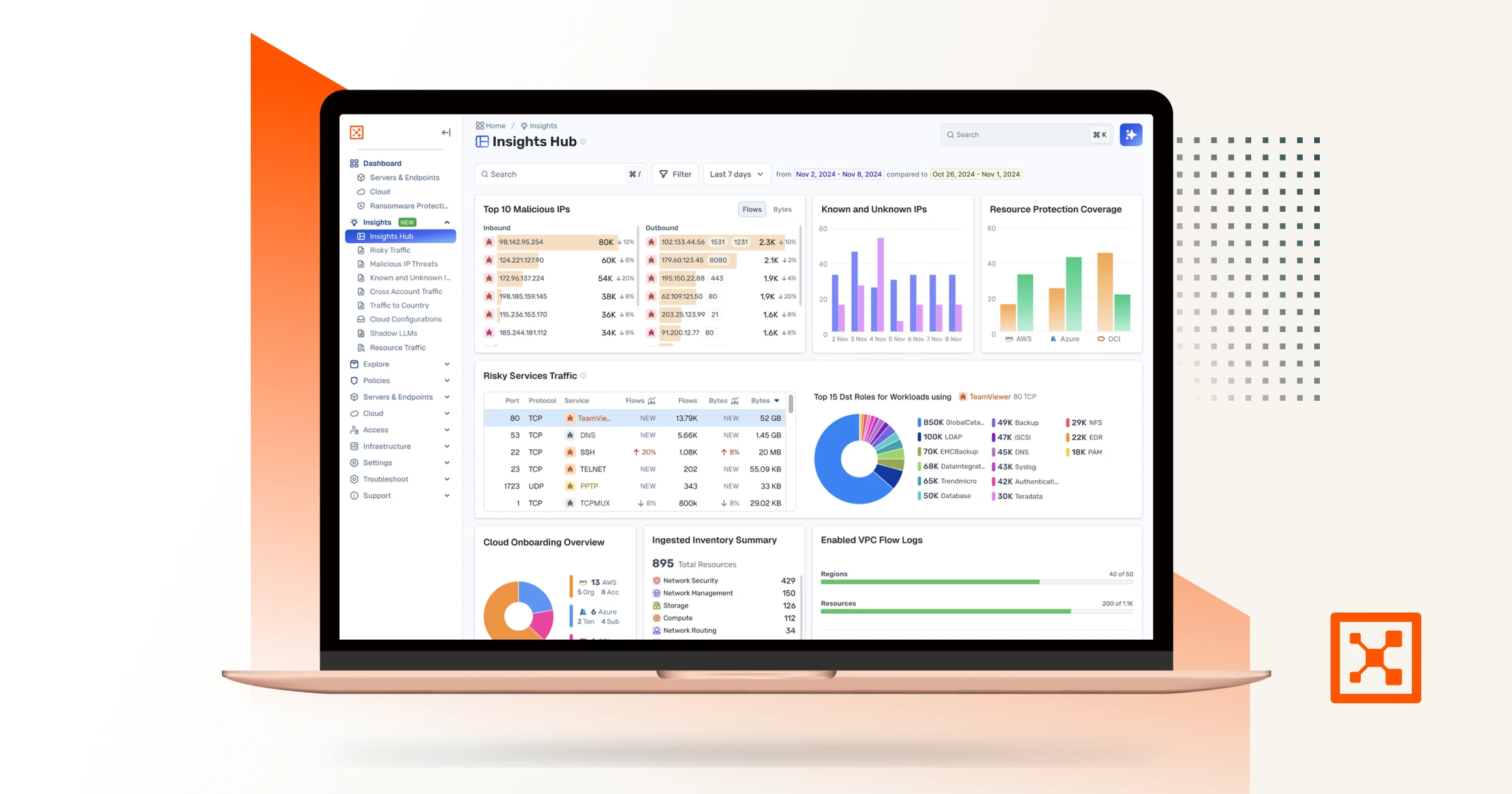
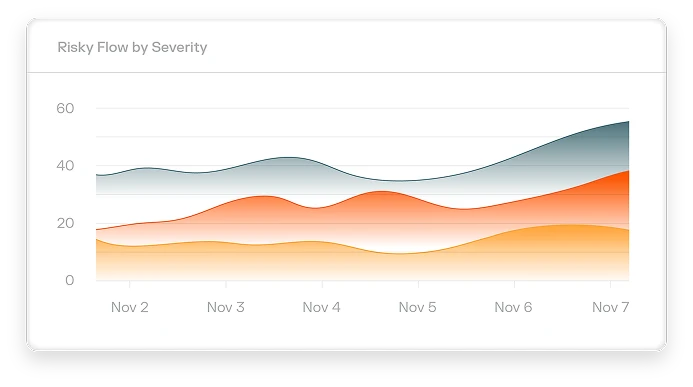
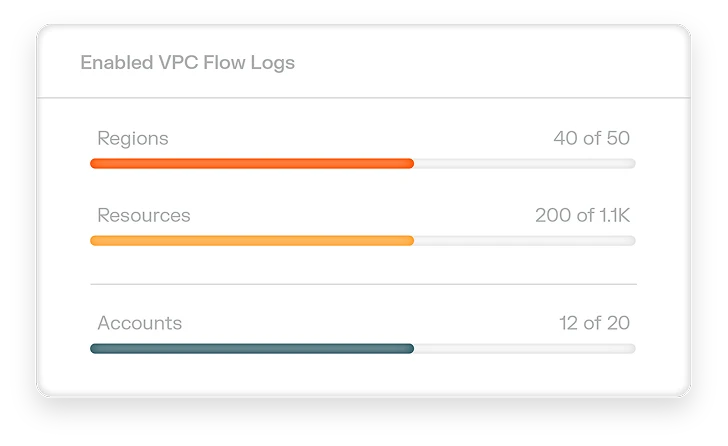
Illumio Insights
Identify lateral movement, detect attacks, and stop breaches instantly at cloud scale. Powered by your AI teammate Insights Agent, prioritize and stop critical threats with context-rich analysis, deep observability, and one-click containment.




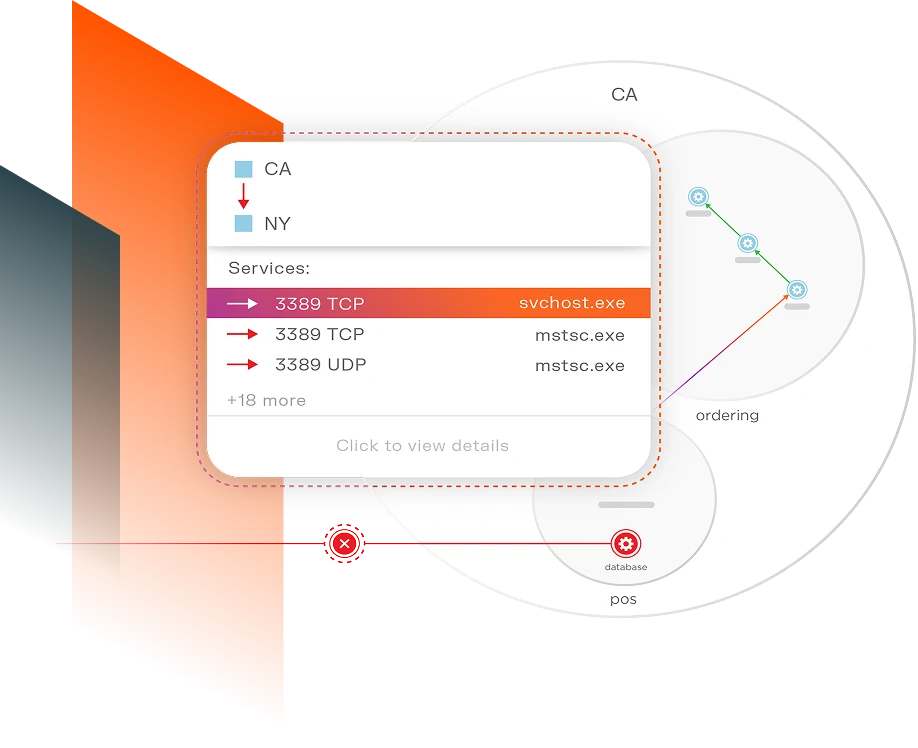
Illumio Segmentation
Secure critical assets, workloads, and devices across your hybrid, multi-cloud environment. See risk, set policy, and prevent lateral movement with the proven leader in microsegmentation.
Illumio is named a Customers’ Choice in the 2026 Gartner® Peer Insights™ VOC Report for Network Security Microsegmentation
Illumio earned a 4.8 out of 5 star overall rating based on 59 reviews as of November 2025.


How Marriott Vacations safeguards its data and global operations with Illumio