Visibility across the hybrid attack surface
Map assets and identify potential risks with Illumio to reduce the attack surface

Implementing the right policies is impossible with network blind spots
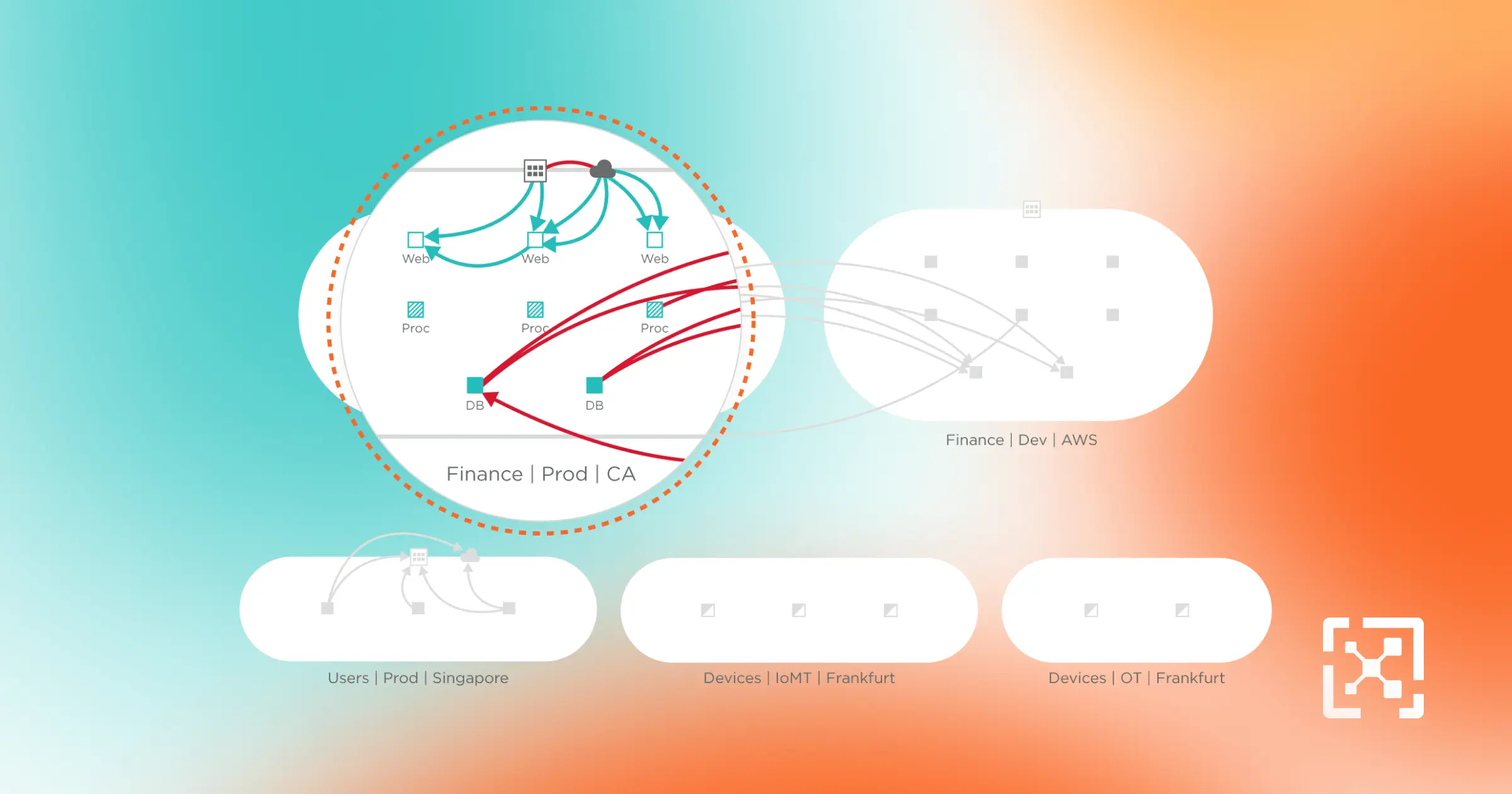
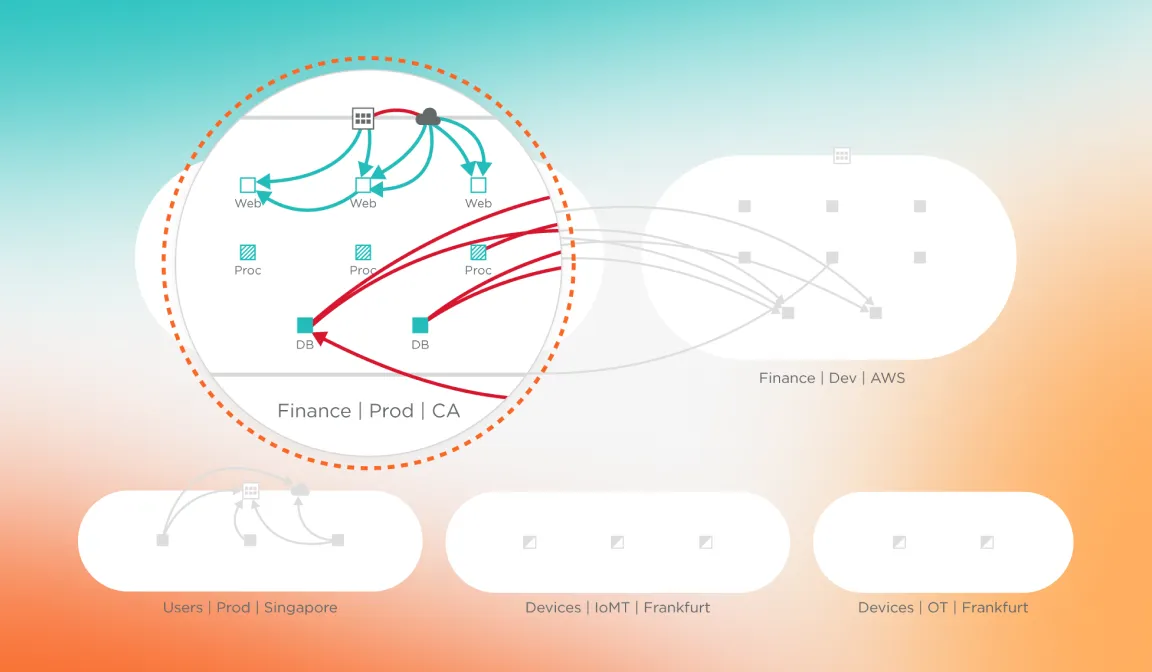
Lack of visibility hides potential risks
Without being able to map communications between assets, it’s impossible to understand all the potential risks.
An incomplete view makes it difficult to respond
Legacy tools don't offer complete visibility or the agility required to react quickly to an attack.
Insight into vulnerabilities helps assess risk
Visibility of how vulnerable systems are connected is key to assessing the risk of an individual resource.
Lack of visibility reduces cyber resilience

AI is accelerating the speed and impact of cyberattacks
Threat actors are using AI-generated attacks to find all vulnerabilities and open paths, making identification critical.

New regulations require increased cyber resilience
Recent industry and regulatory cybersecurity mandates require improved security for IT and OT assets.

Attackers want to disrupt operations
Threat actors are focusing on disruptive attacks that legacy cybersecurity tools can’t prevent.
Identify and reduce risk with Illumio
Map IT and OT dependencies
Simplify security policy design by understanding communication and traffic flows.
Identify risk
Secure against exploits by seeing systems with vulnerabilities and how they connect.
Audit ports and protocols
Restrict the movement of ransomware by identifying and closing high-risk ports.
See and fix vulnerabilities
Protect critical assets by identifying and closing non-essential connections.