Cloud Security
.svg)
Related blog posts

100% Cloud? You Still Need Zero Trust Segmentation
Learn why being 100% cloud does not negate the need for breach containment with Zero Trust Segmentation and how Illumio can help.

AWS Marketplace Features Illumio as a Leading Cloud Security Solution
Why AWS Marketplace features Illumio Zero Trust AWS Segmentation as a leading cloud security solution.

5 Practices You Need to Adopt Now for Cloud Security Maturity
Tips for achieving a cloud security maturity model, in order to support and defend a cloud native maturity model.

Refocus on Cloud Security: How Zero Trust Segmentation Secures the Cloud
Learn the 4 main ways that Zero Trust Segmentation secures the cloud from the spread of cyberattacks.

Refocus on Zero Trust Segmentation: Put ZTS First on Your Fiscal Planning Project List
Research by Enterprise Strategy Group (ESG) reveals Zero Trust soars as an increasingly critical component of an overall Zero Trust segmentation strategy.

Illumio at Microsoft Ignite 2022: Simple Breach Containment to Protect Azure Assets
We’re excited to be at the hybrid Microsoft Ignite 2022 conference on October 12-13.

How Illumio Helps Promote Cloud Security Best Practices With the Cloud Security Alliance
Illumio joins the Cloud Security Alliance (CSA) to help define standards, certifications, and cloud security best practices to ensure secure cloud computing.

More Cyberattacks, Zero Trust Analysis Paralysis, and Cloud Security
Illumio CEO and co-founder Andrew Rubin discusses workload paralysis and how traditional security tools lack durability against today's catastrophic attacks

CTO PJ Kirner on Cloud Security and the Groundbreaking Innovations of Illumio CloudSecure
The cloud has become BIG business. Many organizations, once hesitant to embrace the cloud, are now using it to drive revolutionary transformation of their operations by gaining major scale, flexibility and efficiency advantages.

5 Reasons Your Cloud Architect Will Love Microsegmentation
For a cloud architect, going to the cloud is more than just a change in location.

5 Use Cases for Deploying Microsegmentation in Public Cloud Environments
Public clouds have created on-demand, elastic environments that can be easily scaled to meet changing business needs.

Why Hybrid Cloud Should Not Equal Hybrid Security
Just as overlay networks enable one consistent approach to networking in a hybrid cloud, hybrid security should be designed in the same way. Here’s why.
Related resources








Illumio + Netskope: Extend Zero Trust to Remote Access Architecture
Automatically see compromised workloads and update Netskope One remote access permissions with Illumio Zero Trust Segmentation.








Wiz Cloud Security Platform + Illumio CloudSecure
Combine threat detection and Zero Trust Segmentation to automatically close security gaps before attacks exploit them.








How Network Segmentation Helps Deliver Resilience Against NHS Cyber Threats
This report investigates the state of NHS cybersecurity and how healthcare organizations can adopt Zero Trust Segmentation (ZTS) to address current security challenges.








Cloud Workload Migration Explainer Video
Watch the video to learn how Illumio builds cyber resilience and ensures business continuity as your apps are migrated to and transformed in the cloud.








Illumio CloudSecure Explainer Video
Watch the video to learn how Illumio CloudSecure can help you confidently contain attacks in the public cloud.








Cloud Security Index: Key Findings from France
Vanson Bourne summarizes research findings on the state of cloud security in French organizations.








Cloud Security Index: Key Findings from Australia
Vanson Bourne summarizes research findings on the state of cloud security in Australian organizations.








Cloud Security Index: Key Findings from Germany
Vanson Bourne summarizes research findings on the state of cloud security in German organizations.








Cloud Security Index: Key Findings from the United Kingdom
Vanson Bourne summarizes research findings on the state of cloud security in UK organizations.








Cloud Security Index: Key Findings from the Middle East
Vanson Bourne summarizes research findings on the state of cloud security in Middle East organizations.
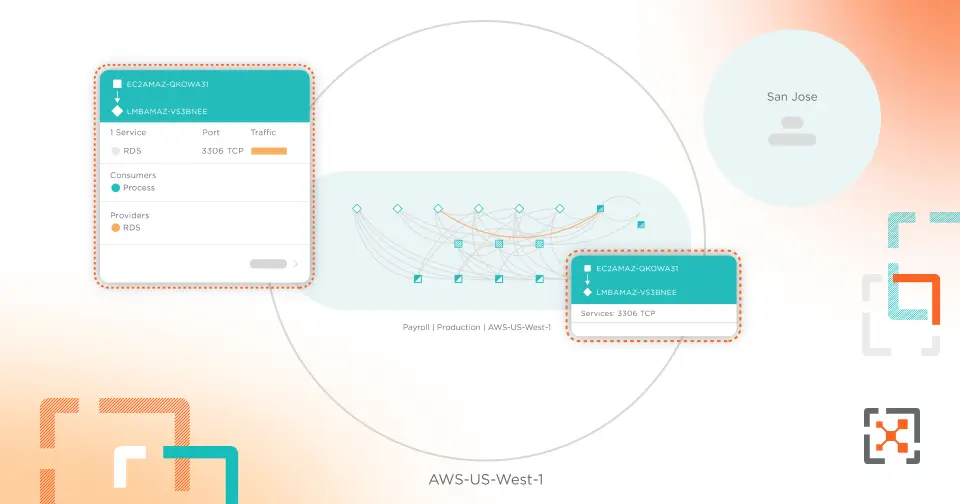







Illumio CloudSecure Demo
Watch how Illumio CloudSecure visualizes cloud workload connectivity, applies proactive segmentation controls, and contains cloud attacks.
Assume Breach.
Minimize Impact.
Increase Resilience.
Ready to learn more about Zero Trust Segmentation?
