Démystifier les techniques de ransomware à l'aide d'assemblages .Net : 5 techniques principales
Les attaques par ransomware consistent à échapper à la détection et à crypter les données d'un système. Dans l'analyse qui suit une attaque de ransomware, nous lisons souvent que l'attaque a utilisé une combinaison de différents types de fichiers ainsi que diverses techniques.
Qu'est-ce que cela signifie en réalité ? Dans cette série, nous allons tout décomposer en utilisant le cadre logiciel .Net pour montrer comment ces capacités de ransomware sont rendues possibles.
Dans ma précédente série en trois parties sur les charges utiles et les balises des logiciels malveillants, l'accent était mis sur le cadre de test de pénétration Metasploit. Nous avons utilisé sa charge utile de malware meterpreter prête à l'emploi pour montrer différentes techniques d'attaque. Le premier article examinait la manière dont les communications malveillantes démarrent, l'infrastructure de l'attaquant et l'analyse médico-légale d'une attaque. Le deuxième article portait sur les catégories et les types de charges utiles ainsi que sur certaines techniques de manipulation en mémoire. La dernière partie de cette série était consacrée aux techniques d'évasion et d'atténuation.
Dans cette série, nous allons créer nos propres fichiers de charge utile (également connus sous le nom d'assemblages) en nous appuyant sur le cadre logiciel .Net, mais en nous concentrant sur les ransomwares. Nous commencerons par décomposer les capacités des ransomwares et des malwares en exemples de techniques individuelles afin de comprendre comment ils fonctionnent seuls. Certaines de ces techniques individuelles sont finalement combinées en une seule charge utile de ransomware malveillant à l'effet souvent dévastateur.
Technique 1 : téléchargeurs, droppers et loaders
Nous commencerons par examiner comment un ransomware ou un malware peut se connecter à partir d'un réseau infecté. Il s'agit de la capacité à se connecter à un système distant, à télécharger des charges utiles supplémentaires, à les déposer sur le système compromis et à les exécuter (c'est-à-dire à les charger dans la mémoire).
Vous trouverez ci-dessous un exemple d'application de ligne de commande (console ) .Net qui :
- Agit comme un téléchargeur en téléchargeant une autre application exécutable distante(putty.exe). à partir de l'Internet
- Dépose l'application téléchargée dans un dossier temporaire sur le disque de l'ordinateur.
- Renomme l'application en putty_new.exe
- Exécute automatiquement l'application téléchargée sur l'ordinateur pour qu'elle soit chargée dans la mémoire.

Lorsque la charge utile est mise en scène, c'est-à-dire que plusieurs fichiers malveillants font des choses différentes, le Stager (petite charge utile initiale) peut devenir à la fois le téléchargeur et, plus ou moins, le dropper pour le Stage (charge utile principale plus importante). Il peut également s'agir du chargeur de la scène. Les techniques employées dépendront de l'évaluation par l'acteur de la menace du risque de détection, également connu sous le nom de considérations de sécurité opérationnelle.
Un téléchargeur est chargé d'extraire une charge utile d'une source distante telle qu'un serveur web ou un serveur FTP. Cela se fait généralement par l'intermédiaire de l'Internet. Un téléchargeur devra donc tenter d'établir une connexion réseau afin d'atteindre la source distante.
Un dropper, quant à lui, est principalement chargé de livrer ou de déposer une charge utile sur le système d'une victime. Par conséquent, un téléchargeur peut également être un dropper, mais un dropper n'est pas nécessairement un téléchargeur car un dropper peut déjà contenir la charge utile malveillante sous la forme de fichiers exécutables portables (PE) ou de DLL. Ces types de fichiers seront abordés plus loin. Les droppers sont couramment utilisés dans les attaques, les exemples les plus connus étant les attaques de la chaîne d'approvisionnement de Solarwinds et de Kaseya. Dans les deux cas, il s'agissait d'un logiciel d'agent fournisseur compromis, utilisé comme dropper pour des charges utiles malveillantes. Ce dernier est utilisé par le groupe de ransomware REvil.
Un chargeur est chargé de configurer le système victime pour qu'il exécute une autre charge utile malveillante, en particulier dans le cas des charges utiles à mémoire seule. Dans ce cas, le terme "configuration" signifie qu'il faut assurer l'allocation de l'espace mémoire nécessaire, souvent en injectant une DLL dans l'espace mémoire d'un autre processus, puis en mettant en place les bonnes autorisations de mémoire. Le chargeur lance ensuite la charge utile ou exécute les threads nécessaires.
Technique 2 : EXE chargeant un fichier DLL
Les charges utiles des rançongiciels peuvent se présenter sous la forme d'un fichier EXE ou d'un fichier DLL. Nous verrons ensuite comment un fichier exécutable Windows, également connu sous le nom de fichier EXE, peut charger ce que l'on appelle un fichier de bibliothèque de liens dynamiques (DLL) afin d'exploiter le code qu'il contient.

EXE et DLL sont deux types d'assemblages .Net qui contiennent des instructions de code de programmation informatique et des informations associées (métadonnées). Ces instructions et métadonnées sont assemblées en un seul fichier - EXE ou DLL .Net assembly. Ces deux types de fichiers permettent d'exécuter un code de programmation informatique (EXE) sur un système Windows ou de le stocker en tant que fichier de bibliothèque (DLL) qui peut ensuite être "emprunté" et lu par d'autres fichiers. Dans le cas d'une DLL, ce processus s'apparente à la manière dont plusieurs personnes peuvent emprunter le même livre dans une bibliothèque à des moments différents pour en lire le contenu. Dans la deuxième partie de cette série, nous explorerons plus en détail ces deux assemblages en relation avec le logiciel .Net. cadre logiciel.
Pour l'instant, voici un exemple très simple pour démontrer l'utilisation de ces deux types d'assemblages .Net - un exécutable (EXE) qui exécute son propre code, puis charge et lit du code externe à partir d'un fichier DLL. L'exécutable transmet ensuite certaines données au code DLL chargé. Enfin, la DLL utilise les données reçues de l'EXE pour afficher un message à l'intention de l'utilisateur qui a exécuté l'application. Vous trouverez ci-dessous le code en action :
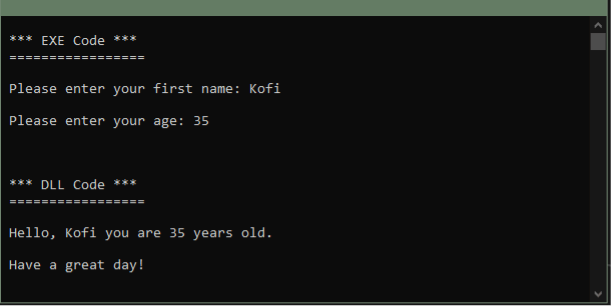
Cette application simple démontre également la relation entre les assemblages EXE et DLL .Net. Ce type de relation est utilisé légitimement par de nombreuses applications et systèmes d'exploitation (bibliothèques partagées), y compris le système d'exploitation Windows lui-même. Windows compile une grande partie de son propre code sous forme de DLL afin qu'il puisse être partagé par différentes applications.
L'image ci-dessous montre le code de programmation de l'EXE et de la DLL de l'exemple précédent. Le code est écrit en utilisant le langage de programmation C# qui est l'un des langages supportés par .Net. Dans l'image, les références au code DLL sont mises en évidence :
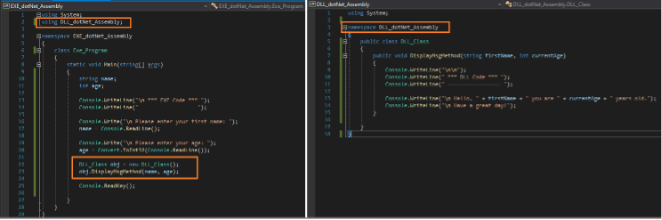
Les DLL sont un moyen efficace d'écrire un morceau de code une seule fois de manière à ce qu'il puisse être utilisé plusieurs fois par différents exécutables en tant que bibliothèque partagée ou dynamique. C'est pourquoi il est également très utilisé par de nombreuses familles de logiciels malveillants et de ransomwares. Des techniques telles que le chargement latéral de DLL et le détournement de DLL sont des techniques malveillantes courantes qui exploitent la relation entre ces assemblages .Net .
Technique 3 : Recon et lancement de binaires vivant de la terre
Nous poursuivons avec une combinaison de techniques importantes : la capacité de recueillir des informations utiles sur un système cible (Discovery) et en même temps de lancer d'autres binaires ou exécutables sur ce système (Spawning). Dans l'image ci-contre, notre exécutable personnalisé initial lance un exécutable ou un binaire natif sur le système Windows cible, ce qui constitue une attaque de type "living off the land" (LotL).

L'exemple montre l'exécution de notre application C# initiale, puis la collecte d'informations utiles sur le système cible, illustrée par le texte vert dans la sortie. Remarquez les informations sur le lecteur qui sont recueillies. Ces informations peuvent être exploitées par un ransomware pour cibler des fichiers sur ces disques, puis être exfiltrés avant d'être chiffrés contre une demande de rançon généralement élevée.
L'application continue en lançant un exécutable système externe - l'invite de commande Windows(cmd.exe). exécutable. L'application personnalisée transmet ensuite certaines commandes Windows au processus Windows cmd.exe pour qu'il affiche (en rouge), dans ce cas, des informations sur la version du système Windows. Pour les besoins de cet article, l'application C# personnalisée affiche les résultats des actions qu'elle effectue ainsi que des informations sur le processus lancé. Cette capacité à lancer d'autres applications externes est également utile pour démarrer les processus de la victime afin d'y injecter du code malveillant.
Technique4 : Encodage des données
L'encodage des données est une autre technique utile. Il s'agit de l'utilisation d'un algorithme pour représenter des données sous une forme différente. Par exemple, un type d'encodage, base64, est légitimement utilisé dans certaines requêtes web pour transmettre des données dans les deux sens, comme l'autorisation HTTP et l'authentification de base dans les appels d'API. Cependant, le même exemple d'encodage base64 peut également aider à cacher certains textes et commandes utilisés par un programme malveillant ou une charge utile. Il peut être utilisé pour obscurcir des parties de code telles que des URL de rappel ou un fichier. Une telle technique est illustrée ci-dessous dans notre programme C# autonome.

Dans cet exemple d'application spécifique, le code prend un texte qui, dans ce cas, est l'URL "https://listener.malware.bad", le convertit en un tableau d'octets informatiques, puis exécute l'algorithme de codage base64 sur les octets pour le convertir en texte ASCII alphanumérique "aHR0cHM6Ly9saXN0ZW5lci5tYWx3YXJlmJhZA==" affiché dans la section du codeur de l'écran de l'application ci-dessus. Ce processus peut être inversé de manière programmatique pour retrouver le texte original, comme le montre la section consacrée au décodeur. Ce faisant, l'URL est cachée à la vue de tous et ne peut pas être immédiatement identifiée pour ce qu'elle est - une URL malveillante.
Technique5 : Chiffrement
Enfin, nous nous penchons sur le cryptage. Le chiffrement des fichiers sur un système compromis est devenu synonyme de ransomware. Il s'agit là encore d'une capacité légitime de sécurisation des données au repos qui, comme la plupart des autres techniques, a été utilisée à des fins malveillantes dans les ransomwares.
Dans l'exemple ci-dessous, nous avons une application de cryptage en C#. Il effectue d'abord une copie du fichier à crypter, puis crypte la copie en laissant l'original intact.

Ici, le contenu original du fichier d'origine, Data1.txt, est copié dans un autre fichier, Data1-Encrypted.txt, et ce nouveau fichier est crypté.

Le chiffrement est l'une des principales techniques utilisées par les ransomwares et constitue la base de l'obtention d'une rançon pour les systèmes compromis. Il peut également être utile pour dissimuler des charges utiles ou des chargeurs de logiciels malveillants en transit ou au repos afin d'échapper à la détection.
Lisez la deuxième partie de la série le 22 mai
Le prochain article explorera le cadre logiciel .Net de Microsoft et le langage de programmation C# associé comme référence pour certaines des tactiques et techniques présentées ici et la manière dont elles sont finalement facilitées.
Apprenez-en plus sur la façon dont la segmentation zéro confiance d'Illumio peut vous aider à contenir les brèches de ransomware.


.webp)


