Qu'est-ce que la sécurité de la couche transport ?
Qu'est-ce que le TLS ?
Transport Layer Security (TLS) est un protocole cryptographique qui permet de sécuriser les communications sur un réseau informatique, le plus souvent l'internet. TLS crypte les données échangées entre les systèmes client et serveur - tels qu'un navigateur web et un site web - garantissant que les données restent privées et inaltérées pendant le transit.
TLS est le successeur de SSL (Secure Sockets Layer) et est largement utilisé pour sécuriser des applications telles que les sites web HTTPS, le courrier électronique, la messagerie instantanée et les services VoIP.
TSL vs. SSL
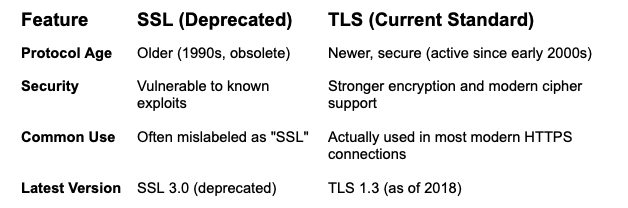
Bien que le site "SSL" soit encore couramment cité, la quasi-totalité des communications sécurisées sur l'internet utilisent aujourd'hui TLS, et non SSL.
L'importance de TLS
- Protection de la vie privée: TLS crypte les données pour empêcher tout accès non autorisé ou toute surveillance.
- Authentifie les identités: Assure que le serveur (et parfois le client) est bien celui qu'il prétend être par le biais de certificats.
- Préserve l'intégrité des données: Empêche la falsification ou l'altération des données pendant la transmission.
- Renforce la confiance des utilisateurs: Active le protocole HTTPS, qui affiche un cadenas dans les navigateurs pour signaler les connexions sécurisées.
- Favorise la conformité: TLS est une exigence de normes telles que PCI-DSS, HIPAA et GDPR.
Le protocole TLS est essentiel pour protéger les données sensibles sur les réseaux publics et privés.
Fonctionnement de TLS
- Phase de poignée de main
- Le client et le serveur s'accordent sur les méthodes de chiffrement (suites de chiffrement).
- Le serveur présente son certificat TLS, qui est vérifié par le client.
- Une clé de session est échangée en toute sécurité à l'aide de la cryptographie asymétrique.
- Phase de cryptage des données
- Une fois la poignée de main terminée, le chiffrement symétrique est utilisé pour protéger les données pendant la session.
- Intégrité de la session
- TLS utilise des codes d'authentification des messages (MAC) pour garantir que les données transmises ne sont pas modifiées.
Cas d'utilisation courants de TLS
- Sites web HTTPS: sécuriser les transactions en ligne, les connexions et les données personnelles.
- Serveurs de messagerie (SMTP, IMAP, POP3): Protège le courrier électronique en transit.
- VPN et accès à distance: Sécurise les connexions sur les réseaux publics.
- API et microservices: Assure une communication sécurisée entre les services.
- VoIP et applications de chat: Cryptage des données vocales et de messagerie.
Versions TLS
- TLS 1.0 et 1.1: Déclassé en raison de la faiblesse du chiffrement.
- TLS 1.2: version la plus utilisée aujourd'hui.
- TLS 1.3: plus rapide, plus sûr et supprime les fonctions cryptographiques obsolètes.
Les organisations devraient désactiver les anciennes versions et appliquer TLS 1.2+ pour maintenir des mesures de sécurité solides.
Foire aux questions
1. TLS est-il la même chose que HTTPS ?
Pas exactement. HTTPS est HTTP sur TLS. TLS est la couche de cryptage qui sécurise les connexions HTTP.
2. Quelle est la différence entre TLS et SSL ?
TLS est l'évolution moderne et plus sûre de SSL. SSL est dépassé et ne doit plus être utilisé.
3. Comment puis-je savoir si un site utilise TLS ?
Recherchez "https://" dans l'URL et une icône de cadenas dans la barre d'adresse du navigateur.
4. Le protocole TLS peut-il arrêter toutes les attaques ?
Non. TLS chiffre les données en transit mais n'empêche pas les attaques au niveau du point d'extrémité ou de l'application. Il s'agit d'une couche de la stratégie de défense en profondeur.
Comment Illumio prend en charge la sécurité basée sur TLS
Si TLS sécurise les données en transit, il ne permet pas de lutter contre les mouvements latéraux ou les menaces internes au sein du réseau interne d'une organisation. Illumio complète TLS en visualisant et en segmentant le trafic des applications afin d'empêcher tout accès non autorisé, même entre des systèmes de confiance. Avec Illumio, vous pouvez voir et contrôler comment les services communiquent entre les environnements, renforçant ainsi votre défense au-delà du chiffrement du périmètre.
Résumé
La sécurité de la couche transport (TLS) est la base de la communication sécurisée sur l'internet. En chiffrant les données, en authentifiant les serveurs et en vérifiant l'intégrité des messages, TLS protège les utilisateurs et les systèmes contre l'écoute, la falsification et l'usurpation d'identité. Il s'agit d'un élément essentiel de la cybersécurité moderne, mais ce n'est pas le seul.
Les entreprises devraient associer TLS à la protection des points d'extrémité, à la segmentation et aux défenses en couches pour une sécurité de bout en bout. Lisez plus sur la segmentation d'Illumio pour obtenir une sécurité de bout en bout pour votre organisation.
.png)