Como o Illumio + Armis protege ambientes modernos de OT

As organizações passaram décadas investindo em defesas de segurança cibernética.
Então, por que 58% das organizações atingidas por um ataque cibernético no último ano ainda relatam ter que interromper suas operações?
E por que esses ataques fazem com que 40% das organizações percam uma quantidade significativa de receita e 35% sofram danos à marca?
Para equipes de tecnologia operacional (OT), em particular, essas estatísticas são ameaças existenciais.
Durante décadas, fábricas, serviços públicos e infraestrutura crítica confiaram em redes isoladas e na segurança do perímetro. Mas com a transformação digital impulsionando a convergência de TI/OT, essas estratégias não são mais válidas.
Os sistemas industriais legados agora coexistem com plataformas em nuvem, sensores de IoT e gateways virtualizados. O resultado é uma superfície de ataque totalmente aberta.
A solução conjunta Illumio e Armis pode ajudá-lo a preencher a lacuna de segurança.
O mandato Zero Trust para segurança de OT
Proteger os sistemas de tecnologia operacional modernos não é fácil. As equipes de segurança atuais são obrigadas a:
- Migre de ambientes com isolamento aéreo para ambientes híbridos
- Apresente gateways em contêineres e arquiteturas SASE
- Gerencie integrações de IaaS e PaaS
Mas essa modernização geralmente supera o investimento em segurança, criando um perigoso “déficit de transformação da segurança”.
O antigo modelo de Purdue funcionava quando os sistemas industriais eram isolados.

Mas em um mundo de gateways em contêineres, ambientes híbridos e OT virtualizada, os perímetros estáticos se desfazem. Desde então, o modelo Purdue foi atualizado para refletir a complexidade moderna.
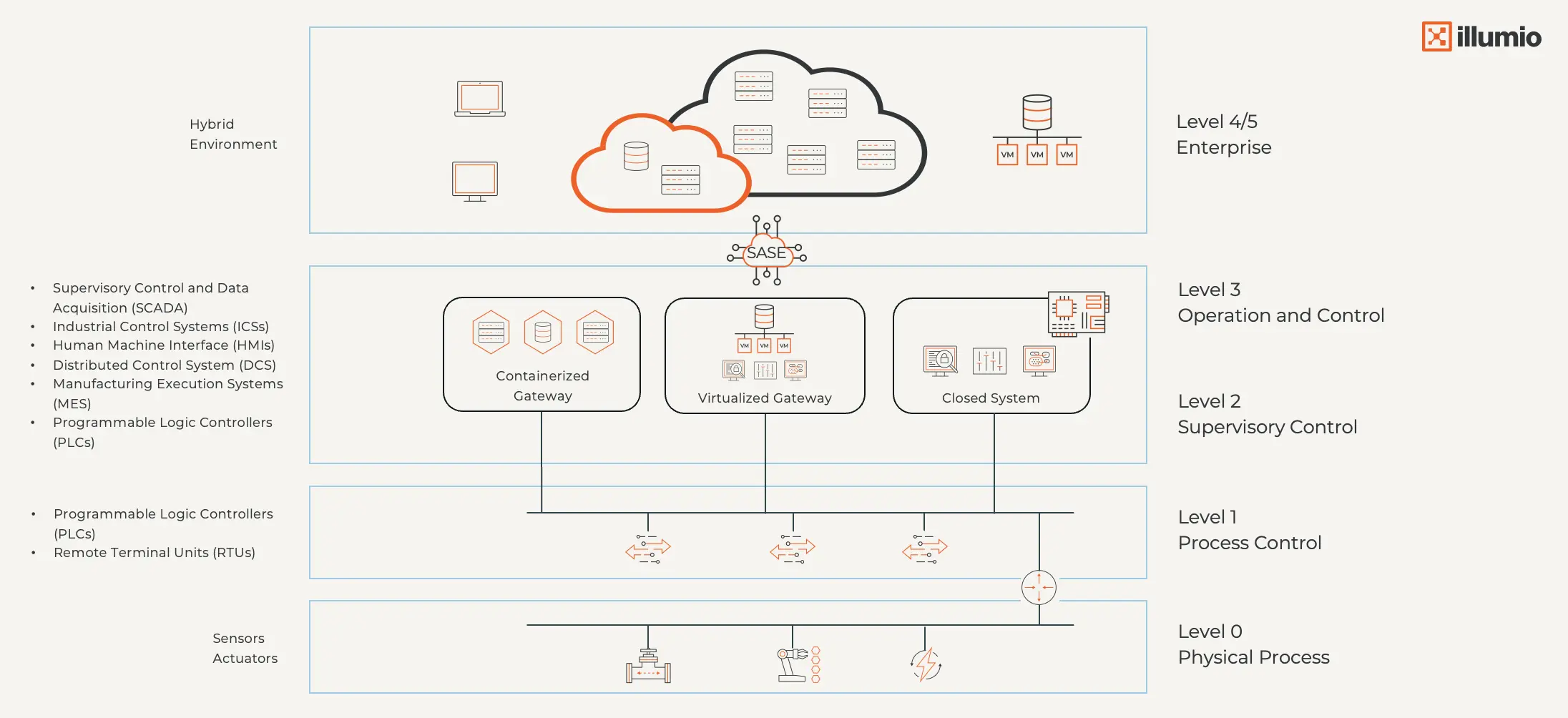
Uma estratégia de Confiança Zero para ambientes de Tecnologia Operacional é o único caminho a seguir. Valida continuamente cada usuário, dispositivo e carga de trabalho, limita o acesso apenas ao necessário e adapta automaticamente as políticas conforme os ambientes e os riscos mudam.
Illumio + Armis: um caminho prático para Zero Trust em OT
A Armis e a Illumio estão redefinindo o conceito de Zero Trust em ambientes industriais complexos.
Juntos, eles combinam visibilidade profunda de ativos com segmentação e fiscalização em tempo real sem interromper as operações.
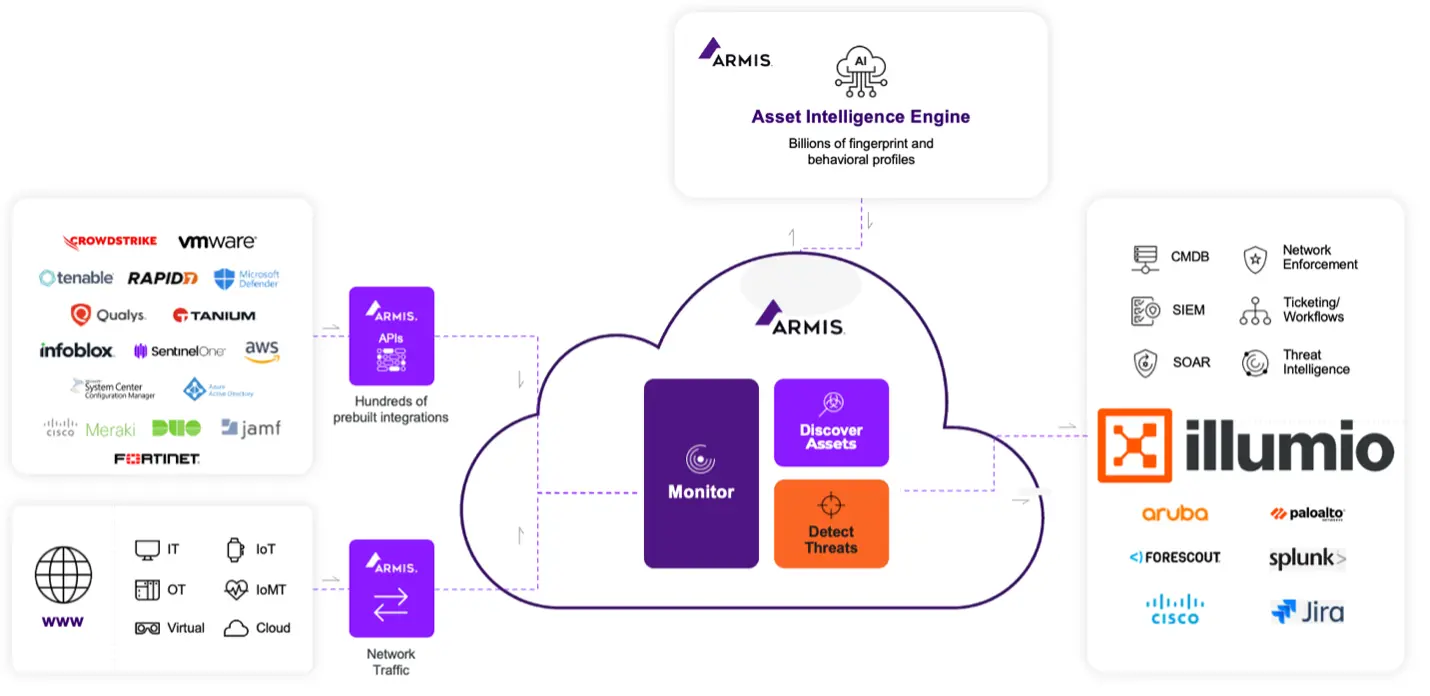
Armis: veja e entenda sua TI, OT e IoT
A Armis oferece visibilidade profunda em TI, TO e IoT.
Seu monitoramento passivo revela o tipo e a função do dispositivo, o comportamento da rede e os padrões de comunicação, o posicionamento no Modelo de Purdue e o contexto de risco e vulnerabilidade.
Essa inteligência é a base para segmentação e proteção.
O Armis monitora passivamente cada dispositivo conectado em TI, OT e IoT, oferecendo visibilidade incomparável de:
- Tipo e função do dispositivo
- Comportamento da rede e padrões de comunicação
- Posicionamento da camada dentro do modelo Purdue
- Contexto de risco e vulnerabilidade
Esse contexto é essencial para segmentar e proteger ativos críticos de OT.
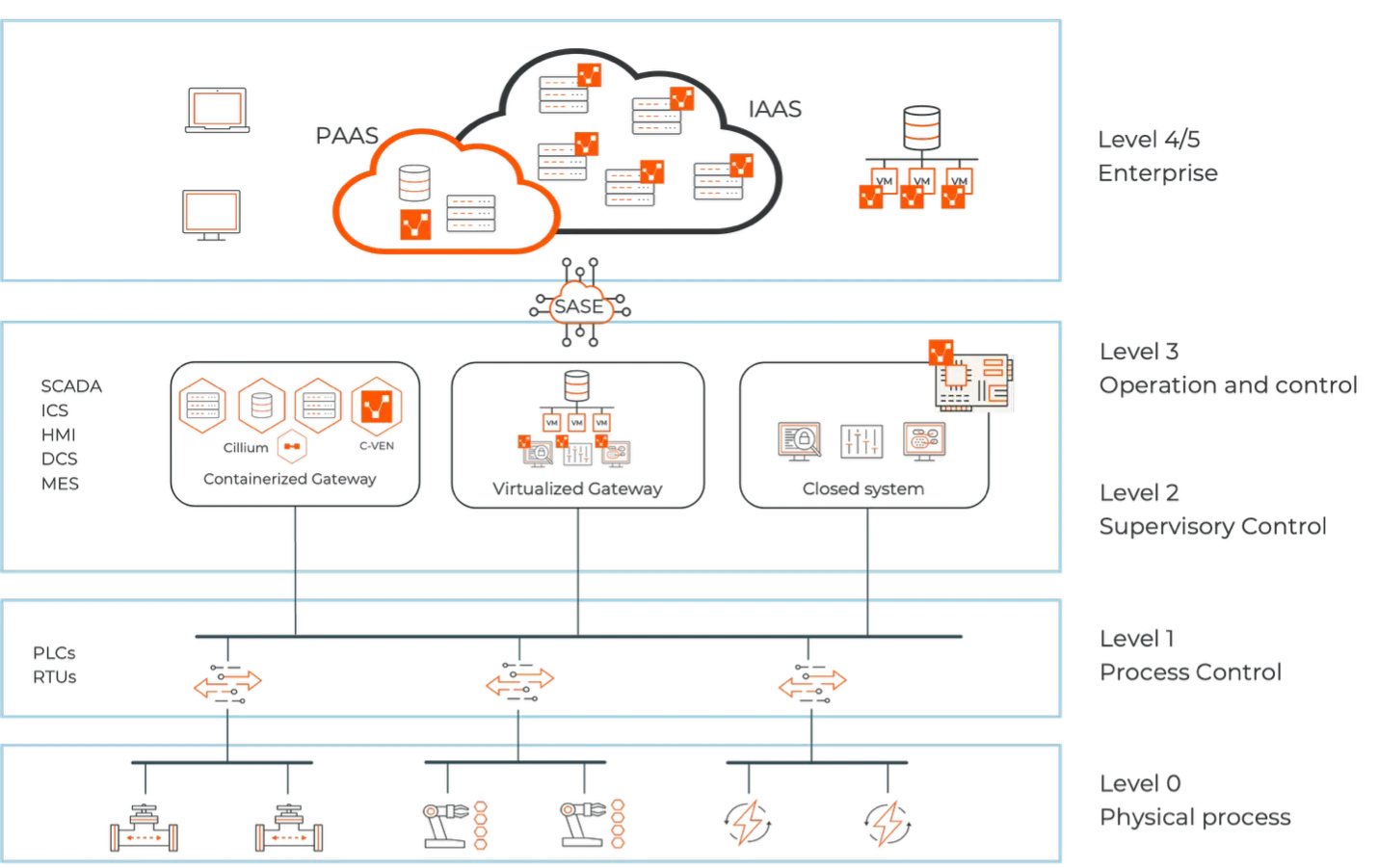
Illumio: imponha a segmentação sem o risco
A Illumio obtém os insights da Armis e aplica políticas de segmentação adaptáveis e baseadas em riscos.
Isso inclui:
- segmentação com o modelo Purdue em mente: bloqueie o tráfego entre SCADA, DCS, MES e ERP para que cada sistema fale apenas com o que deveria. ․
- Resposta dinâmica às ameaças: quando a Armis detecta algo suspeito, o Illumio reage instantaneamente, cortando o acesso ou isolando dispositivos antes que as ameaças se espalhem. ․
- Controle sem agente: proteja dispositivos ICS e PLC frágeis sem tocá-los. A arquitetura Illumio VEN/NEN impõe políticas com segurança, sem a necessidade de agentes.
Essa abordagem é segura, fácil de escalar e manterá suas operações resilientes mesmo durante um ataque ativo, mesmo nos ambientes mais rigorosamente regulamentados.
Principais benefícios da integração Illumio + Armis
A solução conjunta da Illumio e da Armis foi criada para os desafios diários que as equipes de OT e segurança enfrentam.
Sem interrupções nas operações
A maioria das ferramentas de segurança atrasa você com agentes ou mudanças pesadas na rede. Mas Illumio e Armis adotam uma abordagem diferente.
Uma arquitetura leve protege sistemas críticos sem tocar em dispositivos frágeis, como PLCs, RTUs ou controladores SCADA.
A Illumio aplica políticas por meio de seu modelo VEN/NEN, enquanto a Armis oferece visibilidade passiva e sem agente, para que você veja tudo e permaneça seguro sem adicionar riscos.
Defesa de circuito fechado que se adapta em tempo real
A detecção e a fiscalização não podem funcionar em silos. Eles se alimentam.
Quando a Armis detecta algo suspeito, como uma atividade de protocolo estranha ou um dispositivo fazendo ping em um IP público, o Illumio reage instantaneamente bloqueando-o ou restringindo o acesso. O resultado são respostas mais rápidas, menos tempo de espera e um raio de explosão menor sem esperar pela intervenção manual.
Visibilidade e trilhas de auditoria favoráveis à conformidade
Em setores altamente regulamentados, a visibilidade em seus ambientes híbridos significa sobrevivência.
A integração do Illumio + Armis oferece registros prontos para auditoria, simulações de políticas e verificações pré-alterações para que as equipes possam fazer atualizações com confiança.
Esteja você alinhado com o NIST, a IEC 62443 ou a ISO 27001, essa solução conjunta torna a conformidade mais clara, rápida e fácil sem atrasar as operações.
Segurança unificada com valor comercial real
Juntas, a Illumio e a Armis oferecem os resultados mais importantes: defesas mais fortes, auditorias mais suaves e modernização mais segura.
Elas impedem a movimentação lateral antes que ela se espalhe, bloqueiam o ransomware na origem e simplificam a conformidade com controles claros e auditáveis.
E à medida que seu ambiente de OT evolui, seja SASE, gateways virtualizados ou nuvem híbrida, a solução se adaptará. Isso garante que você ganhe resiliência sem perder visibilidade ou tempo de atividade.
Você não precisa escolher entre progresso e proteção. A Illumio e a Armis permitem que você se modernize com confiança, sabendo que seus sistemas mais importantes permanecem consistentemente seguros.
Fechando a lacuna da transformação da OT
Os ataques cibernéticos não estão diminuindo, e os ambientes de OT estão ficando cada vez mais complexos.
As defesas antigas — aberturas de ar, perímetros estáticos e ferramentas isoladas — simplesmente não conseguem acompanhar o ritmo. Cada atraso no fechamento do “déficit de transformação da segurança” deixa a infraestrutura crítica exposta a ransomware, tempo de inatividade e risco regulatório.
É por isso que a integração do Illumio + Armis é importante agora mais do que nunca.
Ao combinar visibilidade profunda de ativos com segmentação e fiscalização em tempo real, ela oferece segurança Zero Trust pronta para produção, compatível com a conformidade e desenvolvida para as realidades da OT moderna.
Você não pode esperar pelo próximo incidente para forçar a mudança. Com a Illumio e a Armis, você pode criar resiliência hoje, para que sua organização possa inovar, modernizar e crescer sem medo de interrupções.


.webp)
.webp)



