Pontos cegos do Kubernetes: por que a segurança de contêineres sem agente é essencial
A adoção de contêineres está explodindo. Assim como os riscos.
Enquanto as equipes de segurança correm para acompanhar os amplos ambientes do Kubernetes, uma coisa ficou clara: você não pode proteger o que não pode ver.
Essa foi a principal conclusão do recente webinar da Illumio, "Descobrindo pontos cegos e expondo ameaças com contêineres sem agente". Apresentado pelos especialistas da Illumio, Nathan Tran, gerente de linha de produtos técnicos, e Christer Swartz, diretor de marketing de soluções.
Eles discutiram como os aplicativos nativos da nuvem modernos apresentam lacunas perigosas de visibilidade e por que as ferramentas tradicionais não foram criadas para resolvê-las. Eles também destacaram como a solução de segurança de contêineres sem agente da Illumio oferece a visibilidade, a escalabilidade e o controle que as equipes de segurança precisam para reduzir o risco em ambientes Kubernetes.
O Kubernetes e seus riscos estão crescendo
Segundo a Gartner, mais de 90% das organizações globais estarão executando aplicativos conteinerizados em produção até o final de 2025. O Kubernetes se tornou a plataforma preferida para orquestrar esses ambientes, desde microsserviços nativos da nuvem até infraestrutura híbrida.
Mas esse crescimento não veio sem desafios. As equipes de segurança enfrentam um cenário cada vez mais complexo de:
- Expandindo as superfícies de ataque. Mais serviços, APIs e portas significam mais pontos de entrada para os atacantes. ․
- Cargas de trabalho de curta duração. Os contêineres giram para cima e para baixo constantemente, dificultando o monitoramento e a fiscalização.
- ․Configurações incorretas. O Kubernetes é poderoso, mas complexo e geralmente é implantado com padrões inseguros. ․
- Lacunas de visibilidade. A maioria das ferramentas não consegue fornecer uma imagem clara do que está acontecendo dentro dos clusters Kubernetes. ․
- Risco da cadeia de suprimentos. As imagens de contêiner podem apresentar vulnerabilidades e dependências desconhecidas. ․
- Controles de identidade inadequados. O controle de acesso baseado em funções (RBAC) nativo não leva em consideração a intenção, a duração do privilégio ou a detecção de movimentação lateral.
Isso cria a tempestade perfeita para que as ameaças cibernéticas floresçam. E sem uma visibilidade profunda e contínua, as organizações estão às cegas.
Segurança de contêineres sem agente da Illumio: o que é e por que é diferente
A segurança de contêineres sem agente da Illumio foi desenvolvida para lidar exatamente com esses desafios.
Ele fornece visibilidade e controle em tempo real sobre as cargas de trabalho do contêiner sem o atrito de instalar agentes em cada nó.
Essa solução faz parte da plataforma Illumio, que estende nossos recursos comprovados de segmentação nativa da nuvem para ambientes conteinerizados.
Veja como funciona e o que o torna diferente.
Criado para a forma como o Kubernetes realmente funciona
Em vez de depender de agentes por nó, a Illumio implanta um agente leve no nível do cluster. Esse agente se integra diretamente às APIs do Kubernetes e aos plug-ins CNI, como o Cilium. Ele reúne informações sobre tráfego, metadados e conectividade em namespaces, serviços e contas na nuvem.
O resultado é uma visão completa de 360 graus do que está em execução, do que está falando e do que não deveria estar, sem interromper o desempenho ou exigir implantações pesadas.
Visibilidade unificada da nuvem e do Kubernetes
O Illumio fornece um único mapa do tráfego na nuvem e no Kubernetes. Você pode ver como pods, serviços e clusters se comunicam com VPCs, data warehouses e outros ativos em todo o seu ambiente.
Essa visibilidade unificada ajuda a eliminar os pontos cegos que os atacantes exploram para movimentação lateral e escalonamento de privilégios.
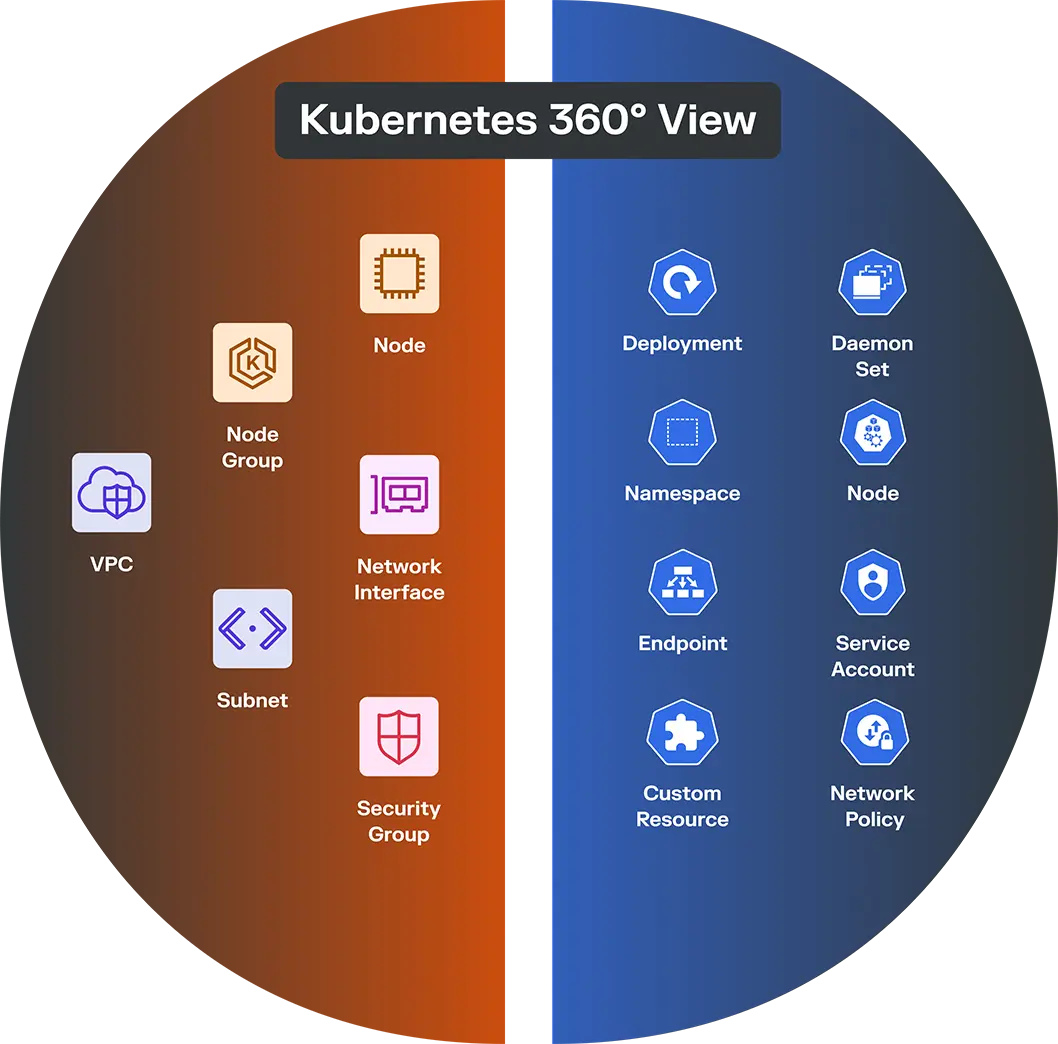
Funciona em qualquer infraestrutura
Com o Illumio, o Kubernetes não precisa viver em um silo.
Nossa abordagem sem agente funciona perfeitamente em ambientes EKS, GKE, OpenShift, AKS e locais. Se você estiver executando na nuvem, no bare metal ou em algum lugar intermediário, o Illumio oferece resultados de segurança consistentes.
Projetado para escalar
Criamos nossa plataforma para lidar com ambientes com milhões de cargas de trabalho. Isso significa que você pode integrar milhares de clusters com o Terraform com apenas alguns cliques. Você obtém insights acionáveis rapidamente, sem criar gargalos operacionais.
Três casos de uso que comprovam o poder da segurança de contêineres sem agente da Illumio
A segurança de contêineres sem agente da Illumio ajuda as equipes a resolver seus desafios mais urgentes do Kubernetes. Vamos explorar os três casos de uso mais comuns.
1. Elimine os pontos cegos da nuvem para o Kubernetes
Muitas equipes de segurança gerenciam ambientes de nuvem e Kubernetes como entidades separadas, usando equipes, ferramentas e visibilidade diferentes. Mas os atacantes não enxergam esses limites.
Com o Illumio, as organizações podem ver como os recursos de nuvem e as cargas de trabalho do Kubernetes interagem, até o nível do namespace e do pod. Por exemplo, você pode visualizar um cluster EKS se comunicando com um data warehouse em uma VPC separada e validar se essa conexão é esperada ou arriscada.
Esse tipo de visibilidade é fundamental para remover pontos cegos, entender possíveis caminhos de ataque e garantir que os recursos do Kubernetes não exponham inadvertidamente ativos confidenciais da nuvem.
2. Valide o comportamento do aplicativo antes e depois da implantação
As equipes de DevOps querem implantar rapidamente, mas a segurança precisa ter a garantia de que os aplicativos se comportarão conforme o esperado.
O Illumio preenche essa lacuna ao permitir que os usuários pesquisem pelo rótulo Kubernetes, visualizem a comunicação de serviço a serviço e auditem conexões antes que o código chegue à produção.
As equipes de segurança podem exportar dados de tráfego, gerar relatórios e aprovar implantações com base no comportamento observado, não apenas em suposições.
Uma vez em produção, o Illumio continua monitorando a comunicação da carga de trabalho para garantir que os aplicativos ainda se comportem conforme o esperado. Se algo mudar, como uma comunicação inesperada entre serviços, as equipes serão alertadas imediatamente.
Isso ajuda a detectar mudanças arriscadas, configurações incorretas ou ameaças emergentes sem diminuir os ciclos de lançamento.
3. Detecte e contenha o movimento lateral em tempo real
Os contêineres são efêmeros. Os invasores sabem disso e usam cargas de trabalho de curta duração para evitar a detecção e se mover lateralmente entre os ambientes.
Quando um pod é reiniciado, as ferramentas tradicionais de registro geralmente perdem o rastro.
O Illumio captura as tentativas de movimento lateral à medida que elas acontecem, visualizando o tráfego não autorizado e identificando as cargas de trabalho exatas envolvidas. Por exemplo, se um pod comprometido voltado para o público tentar se conectar a um plano de controle ou serviço interno do Kubernetes, o Illumio o sinaliza instantaneamente e mostra se ele foi permitido ou bloqueado.
Essa visão em tempo real é fundamental. Ele dá às equipes o poder de investigar, isolar e conter ameaças antes que elas aumentem, mesmo em ambientes altamente dinâmicos e de curta duração.
Por que a segurança de contêineres sem agente da Illumio é essencial agora
As equipes de segurança não podem mais se dar ao luxo de tratar o Kubernetes como uma caixa preta. E eles não podem confiar em ferramentas antigas para monitorar um ambiente projetado para ser rápido, distribuído e em constante mudança.
A segurança de contêineres sem agente da Illumio fornece exatamente o que as equipes de segurança precisam acompanhar:
- Visibilidade profunda de como os contêineres se comportam e se comunicam
- Observabilidade unificada em ambientes de nuvem e Kubernetes
- Implantação sem atrito , sem agentes ou impacto no desempenho.
- Detecção de movimento lateral em tempo real e contenção de ameaças
- Arquitetura escalável criada para ambientes modernos de vários clusters
A Illumio ajuda você a habilitar uma segurança Zero Trust consistente em ambientes Kubernetes, impedindo a movimentação lateral e protegendo o futuro nativo da nuvem.
Se sua organização está adotando contêineres, agora é a hora de fechar a lacuna de visibilidade. As equipes de segurança não conseguem proteger o que não conseguem ver, e os atacantes contam com isso.
Com a Illumio, você pode adotar uma abordagem proativa e consistente para a segurança de contêineres que acompanha você.
Pronto para saber mais? Assista ao webinar completo sob demanda ou Entre em contato conosco hoje.
.webp)





