Cómo la CDR y la segmentación impulsadas por IA facilitan la contención de infracciones
A pesar de un arsenal de herramientas de seguridad (detección y respuesta de puntos finales (EDR), firewalls, sistemas de gestión de eventos e información de seguridad (SIEM) e incluso análisis de comportamiento), muchas organizaciones aún se enfrentan a ataques que se mueven lateralmente en la nube híbrida.
Es algo que puede ocurrir durante semanas antes de que las herramientas tradicionales activen una sola alerta significativa.
Las infracciones exitosas rara vez son resultado de una falta de datos. Son resultado de una falta de contexto y de una incapacidad para contener la amenaza una vez que surge.
Esta es la realidad de las organizaciones que intentan mantener al día con los riesgos de seguridad de la nube moderna empleando las defensas basadas en perímetro de ayer.
El futuro de la detección y respuesta en la nube (CDR) exige un nuevo enfoque: uno que combine CDR impulsada por IA con seguridad de segmentación para brindar una observación profunda, información procesable y una contención de violaciones más rápida y sencilla.
A medida que la IA continúa transformando tanto el ataque como la defensa, las organizaciones buscan enfoques de seguridad más unificados y automatizados. Por eso es el momento adecuado para explorar cómo el CDR y la segmentación se combinan.
La nube rompió el perímetro.
Los equipos de seguridad confiaron durante mucho tiempo en herramientas que monitorean el perímetro. Pero en los entornos multiplataforma y de nube híbrida actuales, no hay una única frontera que defender.
Las cargas de trabajo en la nube suben y bajan en AWS, Azure, Google Cloud y muchos más. Los desarrolladores envían código a producción diariamente. Los atacantes saben que los puntos débiles no siempre están en el borde: están ocultos en el tráfico de este a oeste entre aplicaciones, servicios y contenedores.

Los ataques de movimiento lateral modernos prosperan dentro de su entorno, no en la frontera. Pero la mayoría de las herramientas de detección tradicionales no fueron diseñadas para monitorear ese comportamiento.
En cambio, se basan en reglas, firmas y umbrales estáticos, inundando a los equipos con alertas que carecen de contexto o prioridad.
Según el Reporte global sobre detección y respuesta en la nube de 2025, las organizaciones enfrentan más de 2000 alertas al día en promedio. Clasificar ese ruido para encontrar los pocos que importan es como buscar un fósforo en una hoguera, mientras los atacantes se mueven silenciosamente por los sistemas, sin ser detectados ni contenidos.
El problema no es que los defensores no estén trabajando lo suficiente. Es que sus herramientas están diseñadas para observar, no para actuar.
Vea más y comprenda más rápido con la detección y respuesta en la nube
La detección y respuesta en la nube (CDR) está diseñada para entornos híbridos y multinube modernos.
A diferencia de los sistemas más antiguos que dependen únicamente de puntos finales o firmas estáticas, CDR analiza continuamente cómo se comunican las cargas de trabajo en las plataformas locales y en la nube.
Cuando el CDR impulsado por IA está en juego, no solo genera alertas, sino que aprende cómo es la normalidad. Modela patrones de comunicación típicos, detecta desviaciones y proporciona detección y respuesta ante amenazas en tiempo real con un contexto práctico.
Esto significa una detección de movimiento lateral más rápida, una mejor postura de seguridad y menos falsos positivos que desperdician el tiempo de los analistas.
Pero incluso la gran detección tiene un límite. Una vez que se detecta un patrón sospechoso, ¿cómo se puede contener? Ahí es donde entra en juego la segmentación.
Contenga las infracciones antes de que se propaguen mediante la segmentación
CDR te da concientización. La segmentación te da control.
La segmentación aplica políticas de seguridad estrictas y con el mínimo privilegio en todo el entorno. Aísla las cargas de trabajo y las aplicaciones entre sí, de modo que incluso si un atacante viola su red, no puede mover lateralmente para acceder a sistemas críticos.
Aquí es donde los beneficios de la microsegmentación quedan claros. Es lo que convierte una gran crisis de ciberseguridad en un evento contenido y manejable. Reduce la exposición de la superficie de ataque, limita la propagación de ransomware y brinda a los equipos de seguridad tiempo para investigar y responder sin perder el control.

La segmentación también cambia el modelo de seguridad tradicional. En lugar de perseguir miles de alertas, su equipo puede centrar en unas pocas señales de alta fidelidad y actuar con decisión.
Esa es la base de la segmentación: asumir la violación, aplicar el mínimo privilegio y emplear el aislamiento como estrategia de defensa predeterminada.
Illumio: CDR impulsado por IA se une a la segmentación
Illumio combina CDR impulsado por IA e inteligencia de segmentación en tiempo real para brindar estrategias de contención de brechas unificadas y adaptables.
Está diseñado para los entornos que realmente tienen los defensores: complejos, dinámicos, híbridos y nativos de la nube.
Illumio Insights: detección y respuesta en la nube impulsadas por IA
Illumio Insights analiza continuamente el tráfico en cargas de trabajo, contenedores, máquinas virtuales y servicios.
Emplea inteligencia artificial y aprendizaje automático para crear una base de comportamiento de cómo se comunican normalmente sus sistemas. Desde allí, detecta anomalías, señala posibles ataques de movimiento lateral y muestra rutas de comunicación de alto riesgo antes de que se conviertan en brechas.
Luego, Insights visualiza su entorno a través de un gráfico de seguridad de IA que proporciona un mapa vivo de dependencias, exposiciones y vulnerabilidades. Esto permite a los analistas del SOC ver instantáneamente qué activos están afectados y cómo podría actuar un atacante a continuación.
Debido a que Insights no tiene agentes en la nube, ofrece visibilidad de cargas de trabajo en contenedores y efímeras sin ralentizar el desarrollo ni agregar fricción para los equipos de DevOps.
Con este panel único, puede mejorar la resiliencia cibernética, acelerar las investigaciones y tomar medidas más rápidas y seguras.
Segmentación de Illumio: aplique controles detallados para contener las infracciones
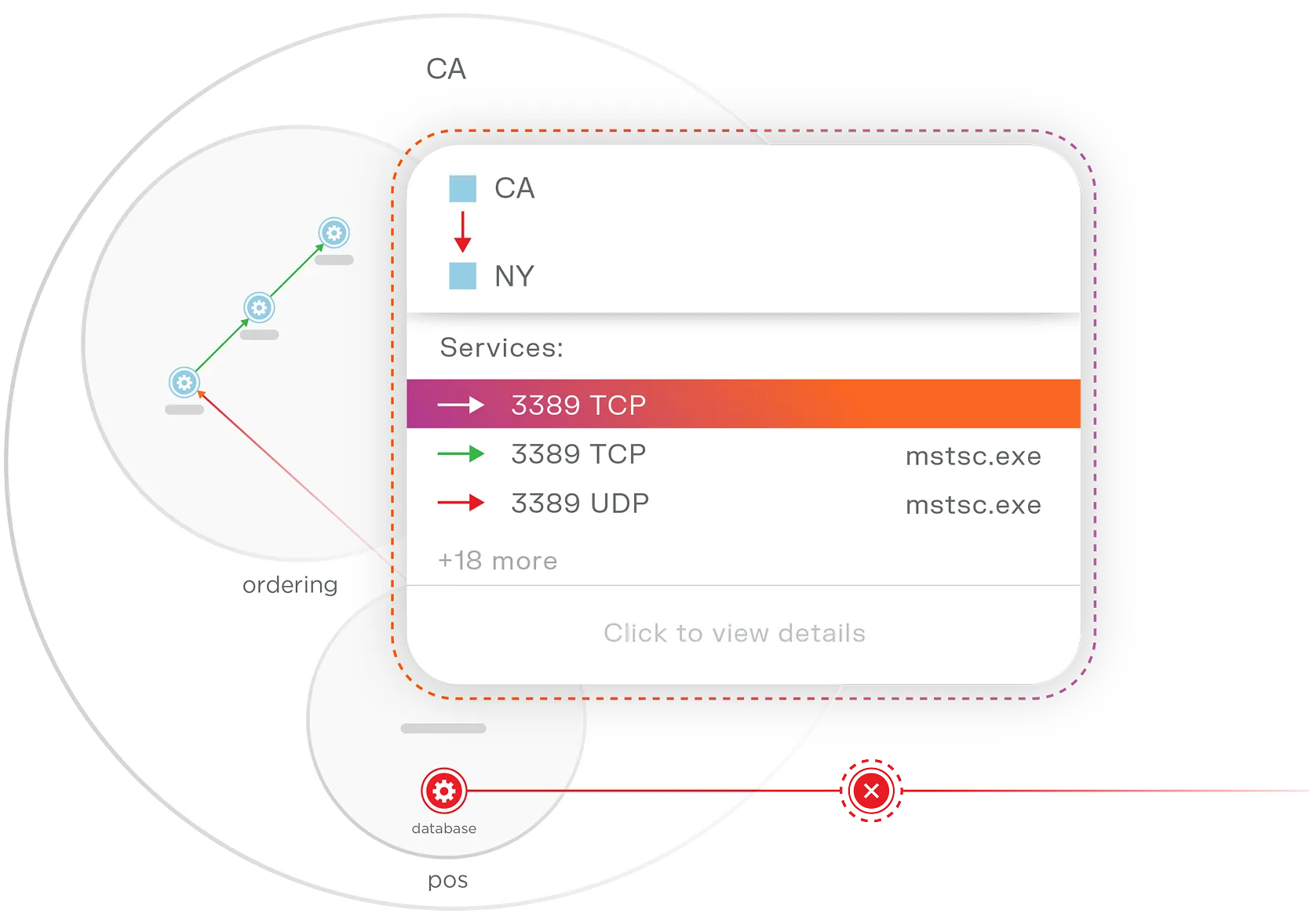
Illumio Segmentation toma la inteligencia de Insights y la convierte en políticas de contención prácticas.
Con Segmentación, los equipos de seguridad pueden definir qué se debe y qué no se debe comunicar, y luego aplicar automáticamente la segmentación de mínimo privilegio en entornos de nube, híbridos, de puntos finales y locales.
Cuando una carga de trabajo se ve comprometida, la segmentación la aísla instantáneamente del resto de la red, lo que evita fallas en la contención del ransomware y detiene el movimiento lateral.
Esta aplicación proactiva permite minimizar fácilmente el radio de explosión de un ataque, cumplir con los requisitos de cumplimiento y mantener la continuidad del negocio, todo sin intervención manual.
Juntos, Insights y Segmentation crean un ciclo de retroalimentación entre la visibilidad y la aplicación que fortalece cada capa de su arquitectura de seguridad.
Por qué la CDR + segmentación simplifica la contención de brechas
Juntos, la CDR y la segmentación impulsadas por IA crean una estrategia de contención de infracciones proactiva y escalable.
Así es como simplifican la defensa y fortalecen la postura de seguridad general de su organización:
- Reducir el tiempo de permanencia. La IA identifica los ataques en una etapa más temprana de la cadena de ataque y la segmentación detiene inmediatamente la propagación antes de que los atacantes lleguen a los sistemas sensibles.
- Eliminar puntos ciegos. Monitorear el tráfico de este a oeste y hacer cumplir el privilegio mínimo significa que ya no habrá caminos ocultos para el movimiento lateral.
- Alivie la carga de su equipo. Los analistas se centran en alertas de alto contexto y alta confianza en lugar de ahogar en ruido de bajo valor.
- Reduce tu superficie de ataque. La segmentación reduce los caminos potenciales que puede tomar un atacante y fortalece los principios de la arquitectura de Confianza Cero .
- Prepare su defensa para el futuro. A medida que los ataques impulsados por IA se vuelven más comunes, esta combinación le brinda a su equipo la agilidad para adaptar y la resiliencia para recuperar.
En resumen, la CDR y la segmentación impulsadas por IA trabajan en conjunto para hacer que la contención de brechas sea más rápida, más inteligente y más eficiente. Al combinar la detección inteligente con el control automatizado, convierten los desafíos complejos de seguridad en la nube en una estrategia de defensa optimizada que mantiene a su organización resiliente, sin importar lo que venga después.
El nuevo estándar para la seguridad en la nube es CDR + segmentación
El perímetro desapareció. La seguridad en la nube es más compleja que nunca. Y ahora los adversarios están aprovechando la IA para evadir la detección y amplificar el impacto.
Para defender eficazmente, las organizaciones necesitan más que visibilidad. Necesitan observabilidad en tiempo real, control de segmentación y un enfoque unificado que les permita detectar, comprender y contener las amenazas más rápidamente, sin importar dónde aparezcan.
Es por eso que combinar la detección y respuesta en la nube (CDR) impulsada por IA con la seguridad de segmentación es esencial en el panorama de amenazas actual.
Prueba Illumio Insights Hoy y vea lo fácil que puede ser construir un sistema de contención de brechas más fuerte y simple.






