Cómo Illumio + Armis protegen los entornos OT modernos

Las organizaciones pasaron décadas invirtiendo en defensas de ciberseguridad.
Entonces, ¿por qué el 58% de las organizaciones afectadas por un ciberataque durante el último año todavía informan que tuvieron que detener sus operaciones?
¿Y por qué estos ataques hacen que el 40% de las organizaciones pierdan una cantidad significativa de ingresos y el 35% experimenten daños a la marca?
Para los equipos de tecnología operativa (OT), en individua, estas estadísticas son amenazas existenciales.
Durante décadas, las fábricas, los servicios públicos y la infraestructura crítica dependieron de las redes aisladas y la seguridad perimetral. Pero con la transformación digital impulsando la convergencia de TI / OT, esas estrategias ya no se mantienen.
Los sistemas industriales heredados ahora coexisten con plataformas en la nube, sensores de IoT y puertas de enlace virtualizadas. El resultado es una superficie de ataque que se abre de par en par.
La solución conjunta de Illumio y Armis puede ayudarlo a cerrar la brecha de seguridad.
El mandato de Zero Trust para la seguridad de OT
Proteger los sistemas OT modernos no es fácil. Los equipos de seguridad de hoy se ven obligados a:
- Migrar de entornos aislados a híbridos
- Introducción de puertas de enlace en contenedores y arquitecturas SASE
- Gestionar integraciones de IaaS y PaaS
Pero esta modernización a menudo supera la inversión en seguridad, creando un peligroso "déficit de transformación de seguridad".
El antiguo modelo de Purdue funcionó cuando los sistemas industriales estaban aislados.

Pero en un mundo de puertas de enlace en contenedores, entornos híbridos y OT virtualizado, los perímetros estáticos se desmoronan. Desde entonces, el modelo de Purdue se actualizó para reflejar la complejidad moderna.
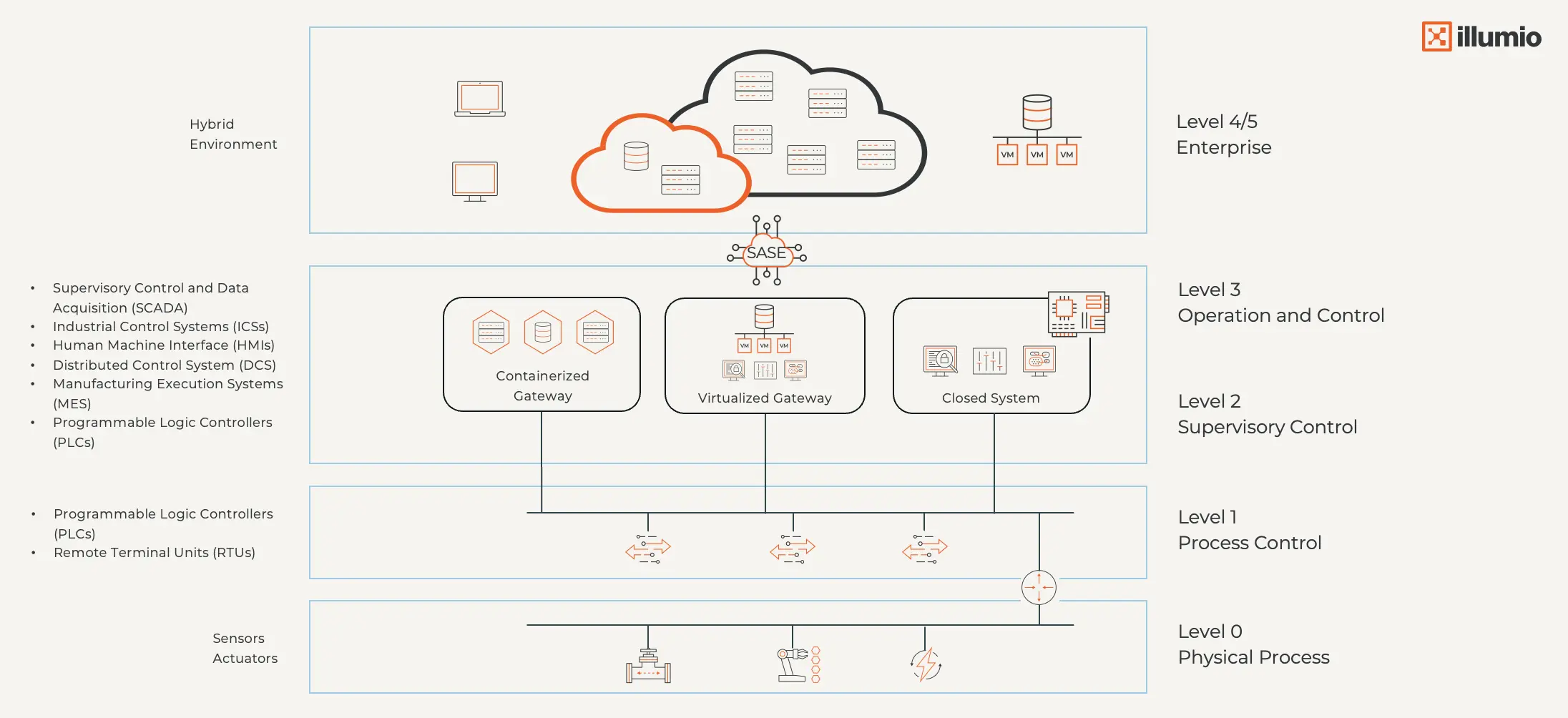
Una estrategia de Confianza Cero para entornos OT es el único camino a seguir. Valida continuamente cada usuario, dispositivo y carga de trabajo, limita el acceso únicamente a lo necesario y adapta automáticamente las políticas a medida que cambian los entornos y los riesgos.
Illumio + Armis: un camino práctico hacia la Confianza Cero en OT
Armis e Illumio están redefiniendo el concepto de Confianza Cero en entornos industriales complejos.
Juntos, combinan una profunda visibilidad de los activos con la segmentación y la aplicación en tiempo real sin interrumpir las operaciones.
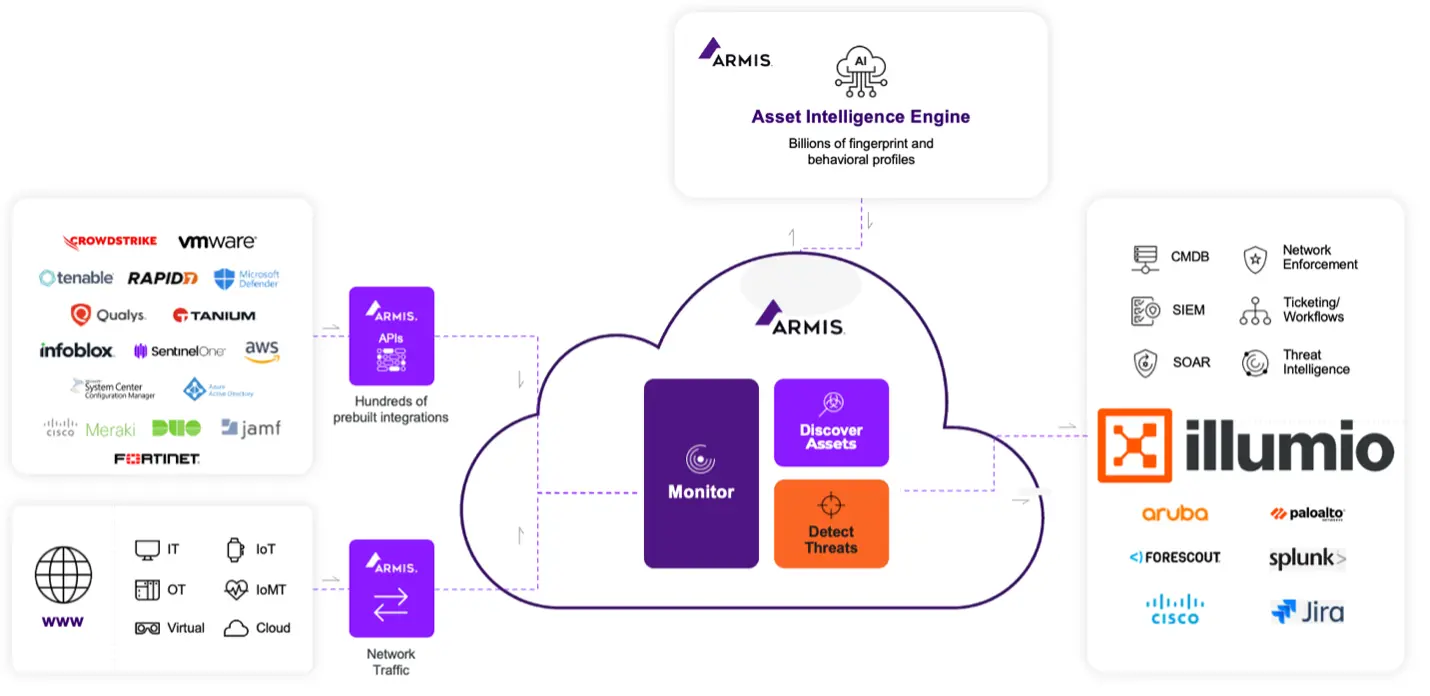
Armis: vea y comprenda su TI, OT e IoT
Armis ofrece una visibilidad profunda en TI, OT e IoT.
Su monitoreo pasivo descubre el tipo y la función del dispositivo, el comportamiento de la red y los patrones de comunicación, la ubicación dentro del modelo de Purdue y el contexto de riesgo y vulnerabilidad.
Esa inteligencia es la base para la segmentación y la protección.
Armis monitorea pasivamente todos los dispositivos conectados a través de TI, OT e IoT, ofreciendo una visibilidad inigualable de:
- Tipo de dispositivo y función
- Comportamiento de la red y patrones de comunicación
- Colocación de capas dentro del modelo de Purdue
- Contexto de riesgo y vulnerabilidad
Este contexto es esencial para segmentar y proteger los activos críticos de OT.
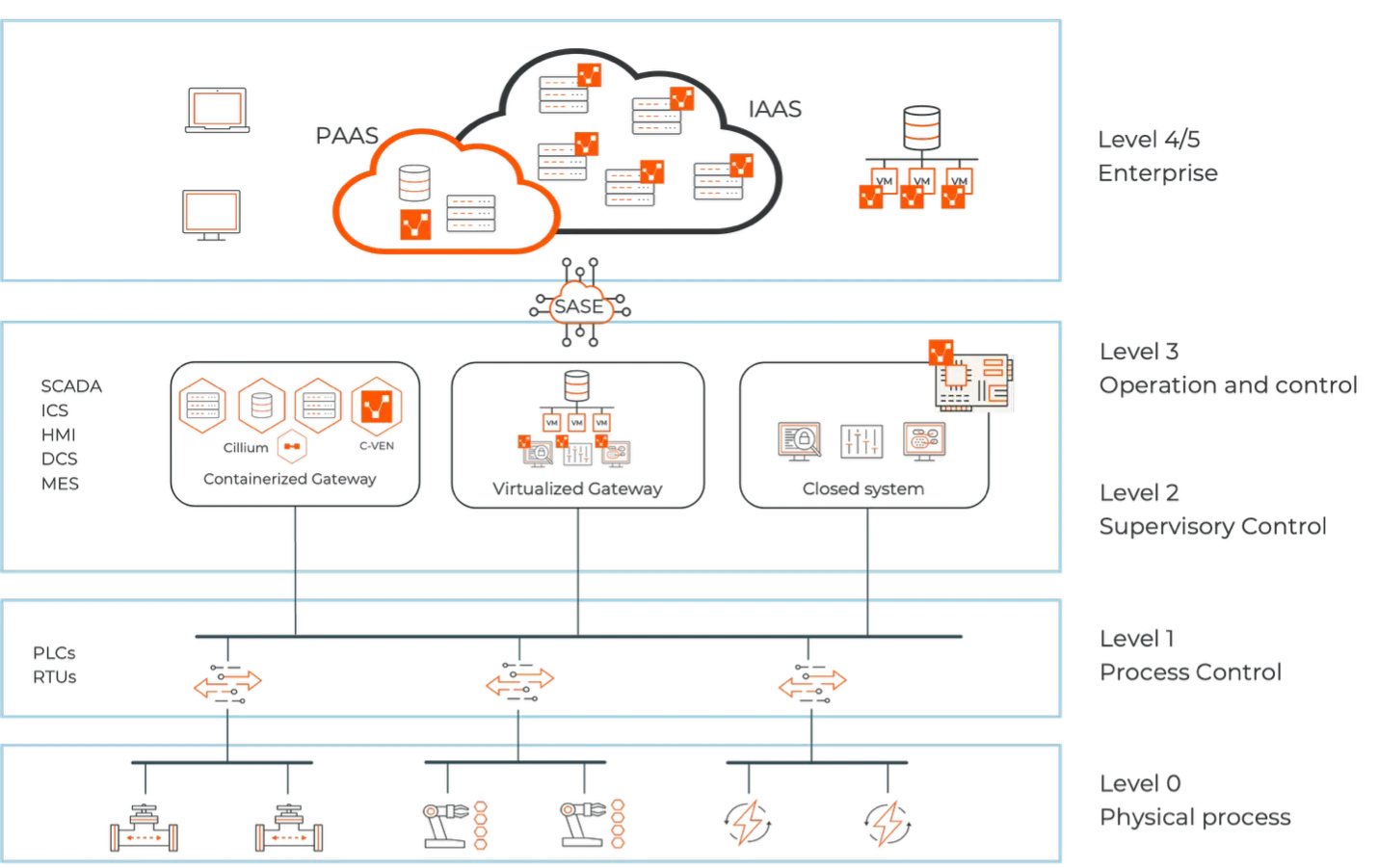
Illumio: aplica la segmentación sin riesgo
Illumio toma los conocimientos de Armis y aplica políticas de segmentación adaptativas e informadas sobre el riesgo.
Esto incluye:
- segmentación con el modelo de Purdue en mente: Bloquee el tráfico entre SCADA, DCS, MES y ERP para que cada sistema solo hable con lo que debería.
- Respuesta dinámica a las amenazas: Cuando Armis detecta algo sospechoso, Illumio reacciona instantáneamente, cortando el acceso o aislando los dispositivos antes de que las amenazas se propaguen.
- Control sin agentes: Proteja los frágiles dispositivos ICS y PLC sin tocarlos. La arquitectura VEN/NEN de Illumio aplica políticas de forma segura sin necesidad de agentes.
Este enfoque es seguro, fácil de escalar y mantendrá sus operaciones resilientes incluso durante un ataque activo, incluso en los entornos más estrictamente regulados.
Beneficios clave de la integración de Illumio + Armis
La solución conjunta de Illumio y Armis está diseñada para los desafíos diarios que enfrentan los equipos de OT y seguridad.
Sin interrupciones en las operaciones
La mayoría de las herramientas de seguridad lo ralentizan con agentes o cambios de red pesados. Pero Illumio y Armis adoptan un enfoque diferente.
Una arquitectura liviana protege los sistemas críticos sin tocar dispositivos frágiles como PLC, RTU o controladores SCADA.
Illumio aplica políticas a través de su modelo VEN/NEN, mientras que Armis ofrece visibilidad pasiva y sin agentes, para que pueda verlo todo y mantener seguro sin agregar riesgos.
Defensa de circuito cerrado que se adapta en tiempo real
La detección y la aplicación no pueden funcionar en aislamiento. Se alimentan mutuamente.
Cuando Armis detecta algo sospechoso, como una actividad de protocolo extraña o un dispositivo que hace ping a una IP pública, Illumio reacciona instantáneamente bloqueándolo o restringiendo el acceso. El resultado son respuestas más rápidas, menos tiempo de permanencia y un radio de explosión más pequeño sin esperar la intervención manual.
Visibilidad y registros de auditoría fáciles de cumplir
En industrias altamente reguladas, la visibilidad de sus entornos híbridos significa supervivencia.
La integración de Illumio + Armis ofrece registros listos para auditorías, simulaciones de políticas y verificaciones previas al cambio para que los equipos puedan realizar actualizaciones con confianza.
Ya sea que se esté alineando con NIST, IEC 62443 o ISO 27001, esta solución conjunta hace que el cumplimiento sea más claro, rápido y fácil sin ralentizar las operaciones.
Seguridad unificada con valor empresarial real
Juntos, Illumio y Armis ofrecen los resultados que más importan: defensas más estables, auditorías más fluidas y una modernización más segura.
Detienen el movimiento lateral antes de que se propague, cortan el ransomware en la fuente y simplifican el cumplimiento con controles claros y auditables.
Y a medida que su entorno de OT evolucione, ya sea SASE, puertas de enlace virtualizadas o nube híbrida, la solución se adaptará. Esto garantiza que gane resiliencia sin perder visibilidad ni tiempo de actividad.
No tienes que elegir entre progreso y protección. Illumio y Armis le permiten modernizar con confianza, sabiendo que sus sistemas más vitales permanecen seguros de manera constante.
Cerrando la brecha de transformación de OT
Los ciberataques no se están ralentizando y los entornos OT solo se están volviendo más complejos.
Las defensas heredadas (espacios de aire, perímetros estáticos y herramientas aisladas) simplemente no pueden seguir el ritmo. Cada retraso en el cierre del "déficit de transformación de seguridad" deja la infraestructura crítica expuesta al ransomware, el tiempo de inactividad y el riesgo regulatorio.
Es por eso que la integración de Illumio + Armis es importante ahora más que nunca.
Al combinar una profunda visibilidad de los activos con la segmentación y la aplicación en tiempo real, ofrece una seguridad confiable cero lista para la producción, fácil de cumplir y diseñada para las realidades de la OT moderna.
No puedes esperar al próximo incidente para forzar el cambio. Con Illumio y Armis, puede desarrollar resiliencia hoy, para que su organización pueda innovar, modernizar y crecer sin temor a interrupciones.


.webp)
%20(1).webp)



