La seguridad de contenedores sin agente de Illumio se expande a AKS, GKE y OpenShift OVN
Desea una seguridad que se mantenga al día con sus contenedores, no que los ralentice.
Los contenedores se mueven rápido. Los entornos de Kubernetes cambian constantemente. Y los atacantes aprovechan esa velocidad y escala para propagar las brechas antes de que te des cuenta.
Es por eso que la seguridad de contenedores sin agente de Illumio sigue evolucionando para brindarle una protección rápida y sin fricciones dondequiera que se ejecuten sus contenedores, sin ralentizar a sus equipos.
Y con nuestras últimas actualizaciones, su cobertura acaba de mejorar mucho.
Más formas de proteger los contenedores. Menos cosas que gestionar.
Estamos ampliando el funcionamiento de la seguridad de contenedores sin agente de Illumio, para que usted obtenga una cobertura de seguridad de contenedores más amplia sin mayor complejidad.
Compatibilidad ampliada con plataformas Kubernetes gestionadas en la nube
Illumio ahora protege los clústeres de Kubernetes en Azure Kubernetes Service (AKS) y Google Kubernetes Engine (GKE), dos de las plataformas de Kubernetes gestionadas más populares.
Eso significa seguridad consistente en entornos híbridos y multinube, todo sin agentes.
Compatibilidad con redes virtuales abiertas (OVN) para OpenShift
Ahora puede proteger clústeres de OpenShift que ejecutan OVN sin instalar agentes dentro de contenedores.
Eso significa políticas de seguridad más estrictas, mejor visibilidad y sin interrupciones en sus cargas de trabajo en OpenShift.
Cómo funciona: integración nativa de Kubernetes y CNI
Illumio se integra directamente con las API de Kubernetes, las API de proveedores de nube y las interfaces de red de contenedores.
Aprovechamos la telemetría que ya existe, para que usted obtenga una visibilidad y segmentación profundas, todo ello sin tocar sus contenedores.
Esto significa que obtiene seguridad Zero Trust, aplicada de forma dinámica y en tiempo real, con una sobrecarga mínima.
Con visibilidad sin agentes en toda su configuración en la nube, y nuestra nueva seguridad de contenedores sin agentes para Kubernetes, puede ver todo desde todos los ángulos:
- Dentro del clúster: tráfico de pod a pod, de servicio a servicio y con reconocimiento de espacio de nombres
- Fuera del clúster: flujos de entrada/salida, acceso a la nube y dependencias externas
- En todos los entornos: tráfico entre clústeres, servicios compartidos y cargas de trabajo no gestionadas
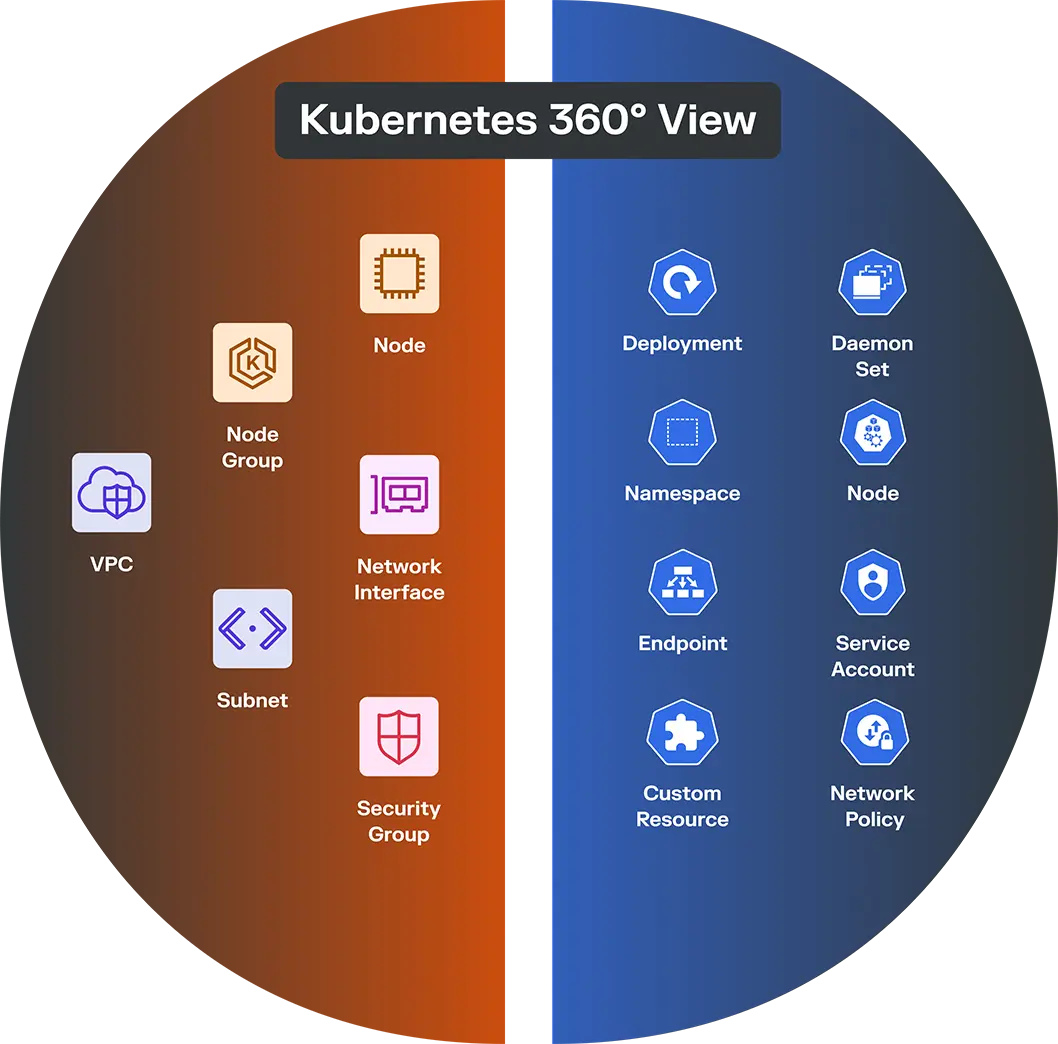
Por qué es importante ahora la seguridad de los contenedores sin agentes
Las herramientas tradicionales basadas en agentes lo ralentizan. No se escalan bien en entornos dinámicos de Kubernetes.
Nuestro enfoque sin agentes le brinda:
- Visibilidad en tiempo real del tráfico de contenedores, incluido el pod a pod, el servicio a servicio y los espacios de nombres.
- La capacidad de detectar y bloquear el movimiento lateral rápidamente, deteniendo las brechas antes de que se propaguen.
- Aplicación coherente de políticas en diversos entornos , ya sea que tus clústeres ejecuten OpenShift OVN, AKS, GKE o en cualquier otro lugar.
Todo esto es sin agregar agentes, sidecars, interrupciones, fricción del desarrollador o complejidad adicional de la canalización.
Cuando sus entornos de contenedores están protegidos de manera consistente y sin agentes, elimina uno de los mayores puntos de fricción en DevSecOps modernos: el constante tira y afloja entre velocidad y seguridad.
Ahora, no tienes que elegir.
Sus desarrolladores siguen mover rápido, sus equipos de operaciones mantienen las luces encendidas y su equipo de seguridad duerme mejor sabiendo que nada se está escapando.
Seguridad de contenedores más inteligente que crece con usted
Los atacantes se están moviendo más rápido que nunca para explotar vulnerabilidades en Kubernetes y cargas de trabajo en contenedores.
Cada punto ciego, cada grupo no gestionado, es un punto de apoyo potencial. Al extender la protección a través de estas plataformas principales y mantenerla sin agentes, Illumio cierra esas brechas antes de que se conviertan en titulares de infracciones.
Con la nueva compatibilidad de OVN con OpenShift y la protección ampliada para plataformas de Kubernetes gestionadas en la nube, como AKS y GKE, obtiene la flexibilidad y el control para proteger sus cargas de trabajo sin los habituales dolores de cabeza de los agentes ni la complejidad adicional.
¿Quieres saber más sobre los fundamentos de nuestra seguridad de contenedores sin agentes? Consulte nuestra publicación de blog anterior, Conozca la nueva solución de contenedores sin agentes de Illumio.
Contáctenos hoy para ver nuestra seguridad de contenedores sin agentes en acción.
.webp)


.webp)



