Illumio Agentless Container Security Expands to AKS, GKE, and OpenShift OVN
You want security that keeps up with your containers, not slows them down.
Containers move fast. Kubernetes’ environments shift constantly. And attackers exploit that speed and scale to spread breaches before you even notice.
That’s why Illumio agentless container security keeps evolving to give you fast, frictionless protection wherever your containers run, without slowing down your teams.
And with our latest updates, your coverage just got a lot better.
More ways to protect containers. Fewer things to manage.
We’re expanding where Illumio’s agentless containers security works, so you get broader container security coverage without added complexity.
Expanded support for cloud-managed Kubernetes platforms
Illumio now protects Kubernetes clusters on Azure Kubernetes Service (AKS) and Google Kubernetes Engine (GKE), two of the most popular managed Kubernetes platforms.
That means consistent security across hybrid and multi-cloud environments — all agentless.
Open virtual network (OVN) support for OpenShift
Now you can secure OpenShift clusters running OVN without installing agents inside containers.
That means tighter security policies, better visibility, and no disruption to your workloads on OpenShift.
How it works: native Kubernetes and CNI integration
Illumio integrates directly with Kubernetes APIs, cloud provider APIs, and container network interfaces.
We tap into the telemetry already there, so you get deep visibility and segmentation, all while leaving your containers untouched.
This means you get Zero Trust security, enforced dynamically and in real time, with minimal overhead.
With agentless visibility across your cloud setup — and our new agentless container security for Kubernetes — you can see everything from every angle:
- Inside the cluster: pod-to-pod, service-to-service, and namespace-aware traffic
- Outside the cluster: ingress/egress flows, cloud access, and external dependencies
- Across environments: cross-cluster traffic, shared services, and unmanaged workloads
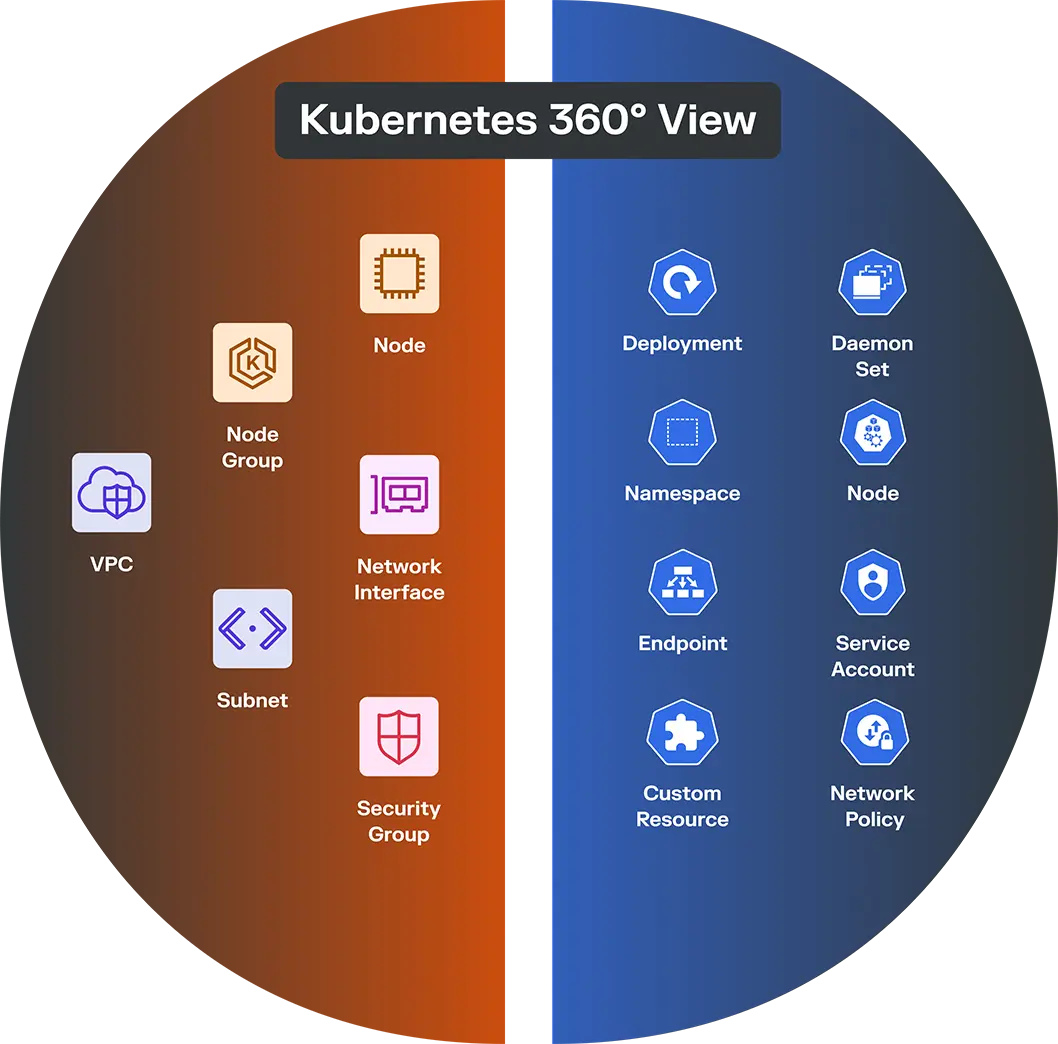
Why agentless container security matters now
Traditional agent-based tools slow you down. They don’t scale well in dynamic Kubernetes environments.
Our agentless approach gives you:
- Real-time visibility into your container traffic, including pod-to-pod, service-to-service, and across namespaces.
- The ability to detect and block lateral movement fast, stopping breaches before they spread.
- Consistent policy enforcement across diverse environments whether your clusters run OpenShift OVN, AKS, GKE, or elsewhere.
This is all without adding agents, sidecars, interruptions, developer friction, or extra pipeline complexity.
When your container environments are protected consistently and without agents, you remove one of the biggest friction points in modern DevSecOps: the constant tug-of-war between speed and security.
Now, you don’t have to choose.
Your developers keep moving fast, your ops teams keep the lights on, and your security team sleeps better knowing nothing’s falling through the cracks.
Smarter container security that grows with you
Attackers are moving faster than ever in exploiting vulnerabilities in Kubernetes and containerized workloads.
Every blind spot, every unmanaged cluster, is a potential foothold. By extending protection across these major platforms and keeping it agentless, Illumio closes those gaps before they become breach headlines.
With new OVN support for OpenShift and extended protection for cloud-managed Kubernetes platforms like AKS and GKE, you gain the flexibility and control to secure your workloads without the usual agent headaches or added complexity.
Want a deeper look into the foundations of our agentless container security? Check out our previous blog post, Meet Illumio’s New Agentless Containers Solution.
Contáctenos hoy to see our agentless container security in action.
.png)



.webp)

