Pare de perseguir sombras: caça a ameaças mais inteligente com o Illumio Insights
Os atacantes de hoje se movem rápido. E com a ajuda da IA, eles estão mais furtivos do que nunca.
Ferramentas de detecção tradicionais geralmente inundam os analistas com alertas. Sem o contexto certo, é como perseguir sombras.
É aí que entra a caça a ameaças: procurar proativamente por sinais de comprometimento antes que os invasores possam se espalhar pelo seu ambiente.
A Illumio Insights vai um passo além. Ao fornecer visibilidade profunda do tráfego entre cargas de trabalho e entre cargas de trabalho e internet, ele ajuda os defensores a ver o que outras ferramentas não percebem.
Em vez de perseguir falsos positivos, o Insights ajuda os caçadores de ameaças a identificar rapidamente os verdadeiros caminhos de ataque e conter violações antes que elas se espalhem para recursos críticos.
Os desafios da caça às ameaças modernas
Enquanto os atacantes se tornam mais sofisticados, os defensores ainda confiam em suposições ultrapassadas — como a ideia de que a visibilidade do perímetro é suficiente.
Em um mundo de infraestrutura híbrida e cargas de trabalho em nuvem em constante expansão, as abordagens tradicionais estão falhando.
Então o que está atrapalhando? Esses pontos problemáticos comuns tornam a busca eficaz por ameaças mais difícil do que deveria ser:
- Pontos cegos leste-oeste: a maioria das ferramentas se concentra no tráfego perimetral norte-sul, deixando o movimento lateral sem visibilidade.
- Complexidade híbrida e multinuvem: a combinação de Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), Oracle Cloud Infrastructure (OCI) e cargas de trabalho locais pode dificultar a correlação.
- Fadiga de alerta: muitos sinais sem priorização suficiente deixam as equipes se afogando em alertas.
- Investigações lentas: silos de dados forçam mudanças infinitas entre ferramentas, retardando a resposta.
Esses desafios não apenas atrasam as investigações. Eles criam pontos cegos perigosos que os adversários estão sempre prontos para explorar.
Para superar as ameaças modernas, as equipes de segurança precisam de visibilidade mais inteligente, integração mais estreita e maneiras mais rápidas de identificar e conter movimentos laterais.
Como o Illumio Insights simplifica a busca por ameaças
O Illumio Insights ingere logs de fluxo da AWS, Azure, GCP, OCI, ambientes locais, firewalls, VPNs e muito mais. Ele mapeia todas as conexões, aceitas ou negadas, em um único local usando um gráfico de segurança de IA.
Como um caçador de ameaças, o hub Insights permite que você veja todas as ameaças ao seu ambiente, sejam IPs maliciosos se comunicando com quaisquer recursos na rede, transferências de dados externos ou serviços de alto risco dentro do ambiente.
Aqui está um exemplo:
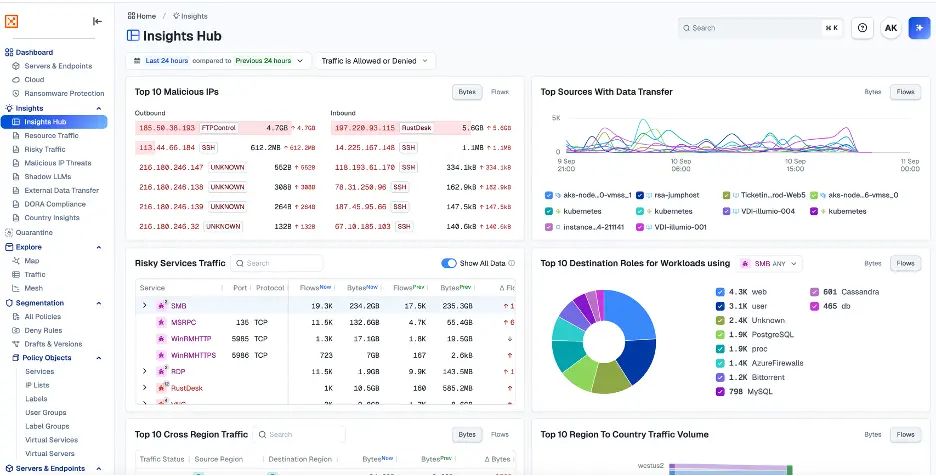
No painel, os caçadores podem detectar anomalias rapidamente. Por exemplo, um pico repentino no tráfego do Rustdesk proveniente de um IP malicioso se destaca.
Ao examinar os detalhes da conexão, vemos tráfego contínuo do Rustdesk entre o IP malicioso e uma máquina virtual (VM) interna.
Esse padrão não é apenas uma investigação única. Isso indica que o invasor estabeleceu uma sessão remota ativa dentro do ambiente.
.webp)
O Rustdesk em si não é inerentemente ruim, mas quando um IP malicioso conhecido se conecta através dele, o alarme dispara. Com alguns cliques, o caçador de ameaças pode rastrear o caminho do invasor:
- O invasor primeiro mapeia o ambiente, escaneando e investigando até descobrir uma ampla gama de recursos. Isso inclui serviços PaaS essenciais dos quais muitas organizações dependem diariamente.
- Durante essa exploração, eles descobrem e ganham acesso a um cofre de chaves, que armazena credenciais e segredos confidenciais que protegem os ativos mais valiosos do ambiente.
- Munido dessas chaves roubadas, o invasor avança sistematicamente em direção aos sistemas de missão crítica, como bancos de dados cheios de registros de clientes, contas de armazenamento de alto valor e camadas de cache que dão suporte aos principais aplicativos.
- Com controle sobre esses ativos, o invasor cria um caminho para extrair dados confidenciais do ambiente. Eles canalizam tudo para uma conta de armazenamento externo sob seu controle, enquanto tentam passar despercebidos.
.webp)
Nesse ponto, o caçador pode fazer mais do que apenas ver o ataque — ele pode detê-lo com a quarentena de um clique do Illumio Insights. Esse recurso permite que os caçadores de ameaças isolem instantaneamente a carga de trabalho comprometida, impedindo que ela se comunique com o restante do ambiente ou com destinos externos.
O que torna isso poderoso é a velocidade. Não é necessário acessar consoles de firewall separados nem esperar por alterações manuais. A contenção é imediata.
E como a Illumio fornece acesso controlado a sistemas em quarentena, administradores e equipes do centro de operações de segurança (SOC) ainda podem fazer login para investigar, coletar dados forenses e remediar o problema, sem correr o risco de uma maior propagação.
Em outras palavras, os caçadores de ameaças podem visualizar o caminho do ataque e contê-lo em tempo real.

A perícia forense não para na quarentena. Com dados históricos de fluxo, os caçadores podem perguntar:
- Quando essa carga de trabalho se comunicou pela primeira vez com o IP malicioso?
- Quantos dados foram transferidos?
- Outras cargas de trabalho apresentam o mesmo comportamento suspeito?
Esse contexto acelera as investigações, aprimora a priorização e fortalece a resposta.
Illumio Insights: passe da defesa reativa para a proativa
A caça a ameaças não se trata apenas de capturar os maus atores. Também se trata de reduzir riscos e interromper o movimento lateral antes que ele se espalhe.
Com o Illumio Insights, as equipes de segurança passam de alertas isolados para visibilidade contextual do caminho de ataque. Isso significa:
- Investigações mais rápidas com todos os dados em um só lugar.
- Priorização mais inteligente com base em caminhos de ataque reais.
- Resposta mais forte por meio de quarentena integrada.
- Escalabilidade em ambientes híbridos e multinuvem.
Em vez de se afogarem no barulho, os defensores obtêm informações úteis e um passo crucial à frente dos atacantes.
Tentar Teste gratuito de 14 dias do Illumio Insights hoje.

.webp)



