3 Steps to Cyber Resilience for the Energy Industry
Experts from IBM Security and Illumio recently gathered for a seminar to review the latest TSA Security Directive and to discuss the latest trends in the energy industry.
Featuring Greg Tkaczyk, an executive consultant with IBM, Rob Dyson, IBM Global OT Security Leader, and Paul Dant, Illumio Senior Systems Engineer, the event featured a deep dive into the shifting state of the energy sector through the lens of evolving cybersecurity needs.
Keep reading to learn more about the TSA Security Directive updates, security expert recommendations for the energy sector, and three steps to cyber resilience in today’s complex threat landscape.
Revised and reissued TSA Security Directive updates
A key topic for the lunch was the TSA’s recent decision to revise cybersecurity requirements for pipeline owners, also known as Ransomware and TSA Security Directive Pipeline 2021-02C. The reissued guidance followed the May 2021 ransomware attack on the Colonial Pipeline, which caused significant fuel shortages, changed flight schedules, and increased fuel prices.
The guidance outlined numerous steps for pipeline owners to take in ensuring up-to-date cybersecurity, including:
- Network segmentation policies and controls
- Access control measures to secure and prevent unauthorized access
- Continuous monitoring and detection policies
- Extensive risk reduction applications
When implementing cybersecurity requirements, grid and distributed energy resource planners should build cyber defenses with the goal of surviving an attack while maintaining critical functionality." – Department of Energy report, Cybersecurity considerations for DER on the US electric grid
Energy sector security requires innovation, digitization, and big data analytics
Beyond breaking down the TSA’s updated guidance, the headlining moment of the event was Dant’s presentation on the challenges facing the modern energy landscape. A heavy focus was around the new challenges plaguing the energy industry. Climate change and the weaponization of energy supply in conflicts such as the war in Ukraine have caused prices to skyrocket recently, forcing rapid change and innovation across the board.
To face these challenges, Dant recommended that energy leaders continue to push innovation in all facets of the industry. Aside from digitizing more assets to optimize supply and manage demand, he noted that security and compliance should be top-of-mind in this new landscape.
Big data analytics must also play an instrumental role, offering benefits for optimizing the efficiency behind a number of key outcomes. Storage, transmission, production, consumer usage, and renewables are all areas that could stand for optimization, said Dant. This means digitizing assets that don’t already produce in-depth data.

3 key steps to cyber resilience in the energy sector
All this rapid innovation and digitization means one thing: an expanding attack surface for ransomware. But a growing emphasis from attackers on inflicting pain to achieve their ends does not help the equation.
According to the 2023 World Economic Forum Global Cybersecurity Report, “Respondents now believe that cyberattackers are more likely to focus on business disruption and reputational damage.”
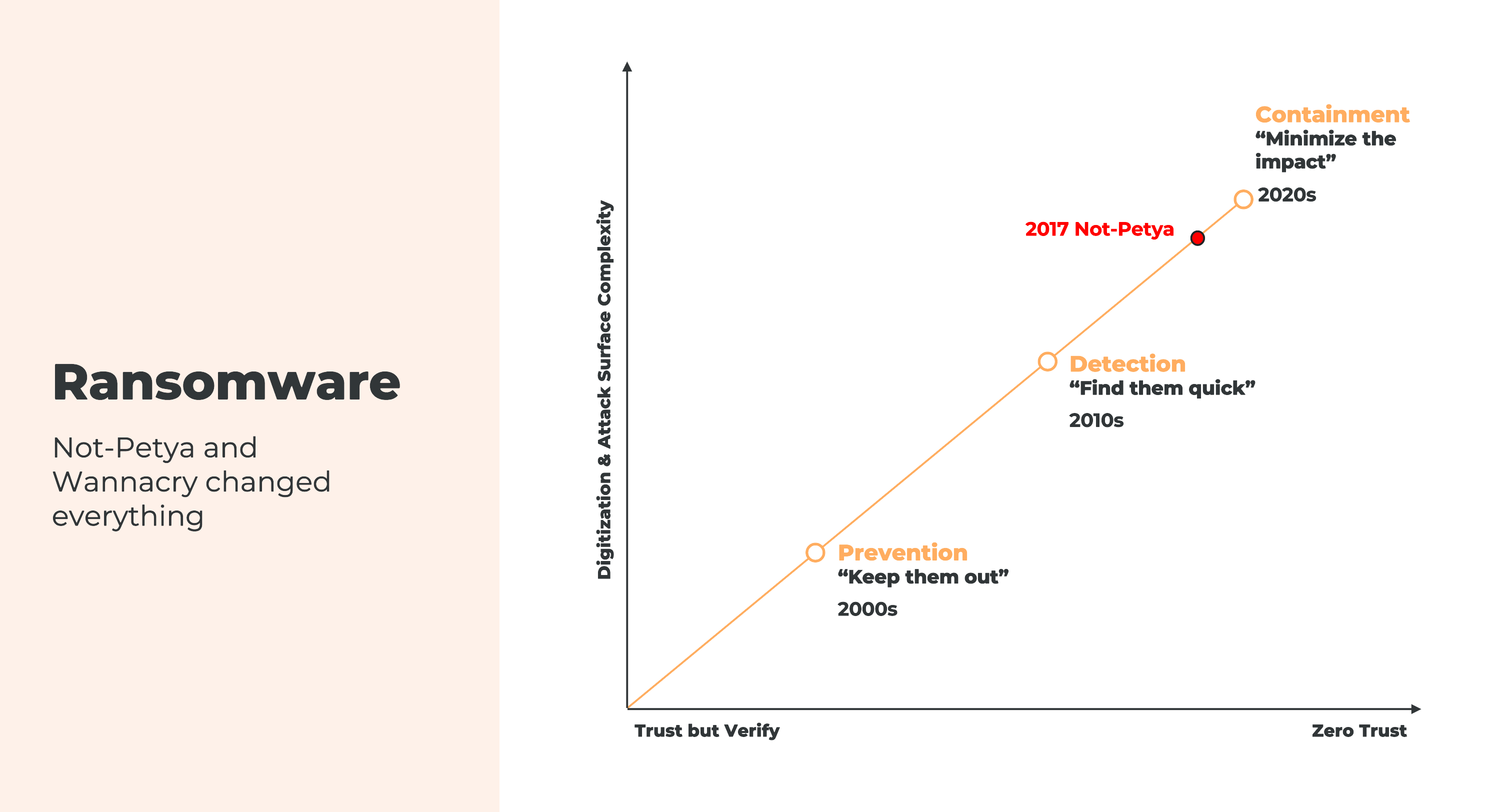
To match the new mindset presented by modern threats, Dant pointed to the mindset changes energy and stakeholders should adopt themselves. Cyberattacks like Not Petya and WannaCry have made the attack surface more complex and accelerated the cyber landscape dramatically towards Zero Trust. A refocusing on containment and resilience is the key.
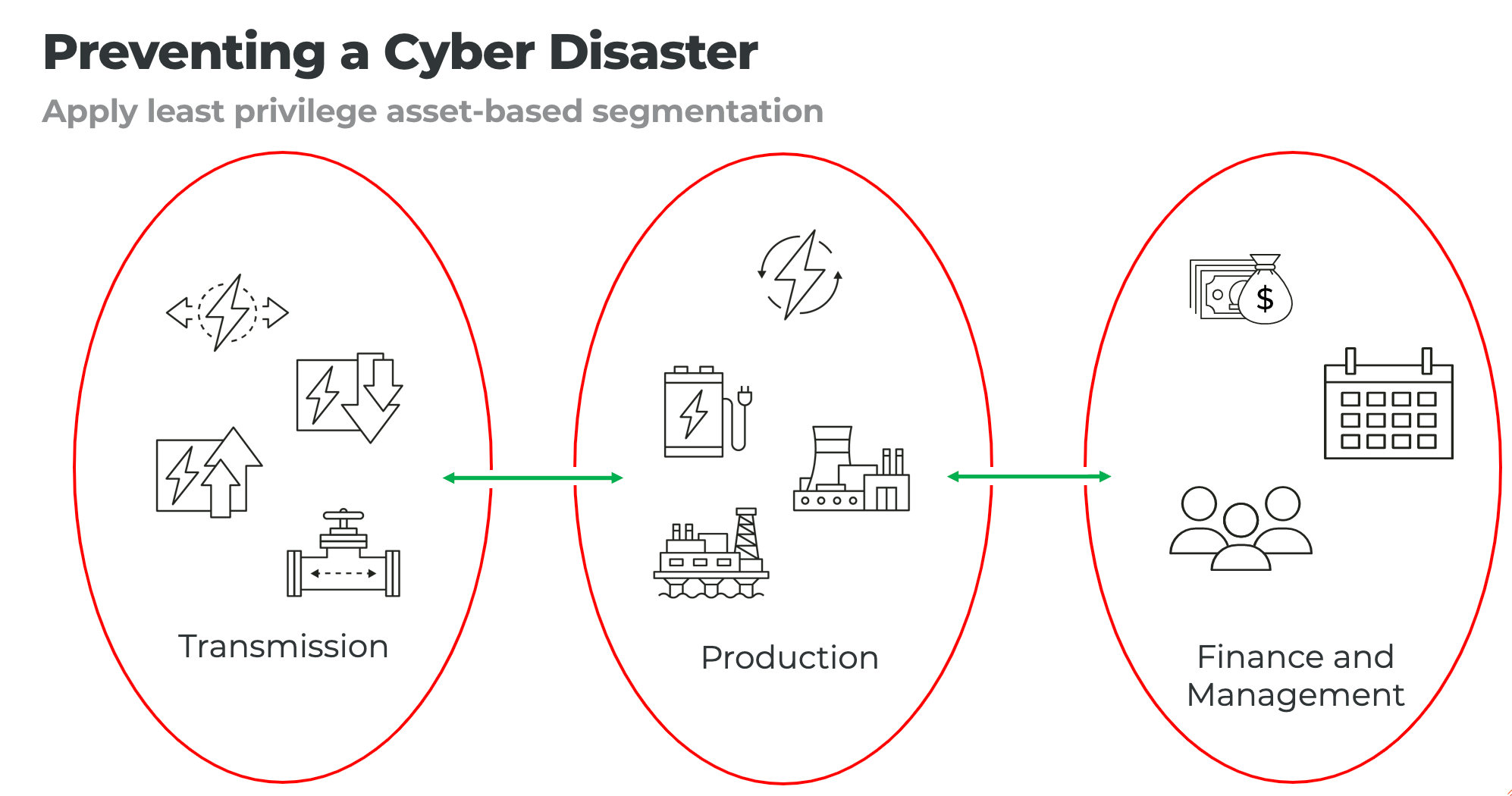
In his presentation, Dant outlined the 3 key steps to cyber resilience:
1. Identify high-risk areas: Remember that threats are drawn towards major societal/business impacts.
2. Develop a response plan: Identify potential risks like assets with highly connected ports, peer-to-peer ports, and well-known ports.
3. Build a long-term strategy: Segment transmission, production, and finance/management. Your new gameplan is to prevent attacks turning into disasters
With simple mindset changes and key practices, the energy industry can adapt to a rapidly shifting landscape with ease.
- Learn how Illumio Zero Trust Segmentation (ZTS) can help contain ransomware and breaches in the energy sector.
- See more upcoming Illumio-hosted events and webinars.
- Contact us today for a free consultation and demo.
.png)



.webp)

.webp)