How Illumio Builds Cohesive Security for Containers
Deploying microservices using containers like Kubernetes and OpenShift offers valuable scalability benefits. But these solutions often lack sufficient security features outside of the cluster and zero visibility into multi-cloud and hybrid environments. This makes maintaining a cohesive security posture across deployments a daunting task for many security teams.
Illumio Zero Trust Segmentation solves this challenge by enforcing security policies and offering complete visibility into network traffic within all these types of environments – all in one platform.
The challenge: Cohesive security in hybrid and multi-cloud environments
The growing adoption of cloud and microservices-driven architectures has opened new horizons for organizations seeking improved scalability and agility in their operations. Containers provide the answer to this need. By nature, they are lightweight, agile, sometimes ephemeral workloads, and can be easily spun up anywhere in the infrastructure. This has led to an increase in the deployment of solutions such as Kubernetes and OpenShift.
Adding this type of workload introduces a new area attackers can exploit and increases complexity in managing hybrid and/or multi-cloud environments. Managing security across these environments is difficult for three reasons:
- It requires domain experience within multiple clouds (Azure, AWS), multiple OS types (Linux, Windows, Unix), and different flavors of containers orchestration (Docker, Kubernetes, Openshift).
- While Kubernetes offers valuable built-in network security features within the cluster, this protection often does not extend beyond the cluster boundaries. This limitation poses significant challenges when securing communication between microservices, especially in multi-cloud and hybrid deployments.
- You need visibility into both pod-to-pod traffic occurring within Kubernetes clusters as well as ingress and egress traffic from your clusters to your environment.
Existing offerings either solve only for security within your cloud environment or within your on-premises and endpoint environments. But to ensure a holistic security posture across these complex environments, you must have a solution that can do it all.
The solution: Illumio Zero Trust Segmentation
Illumio is agnostic to the underlying environment. This allows you to gain complete visibility into network traffic and enforce Zero Trust Segmentation policies across all environments and at scale. The more container environments that are deployed, the more critical it is that your environment can handle over 100,000 workloads and adapt to changes in the environment in real time.
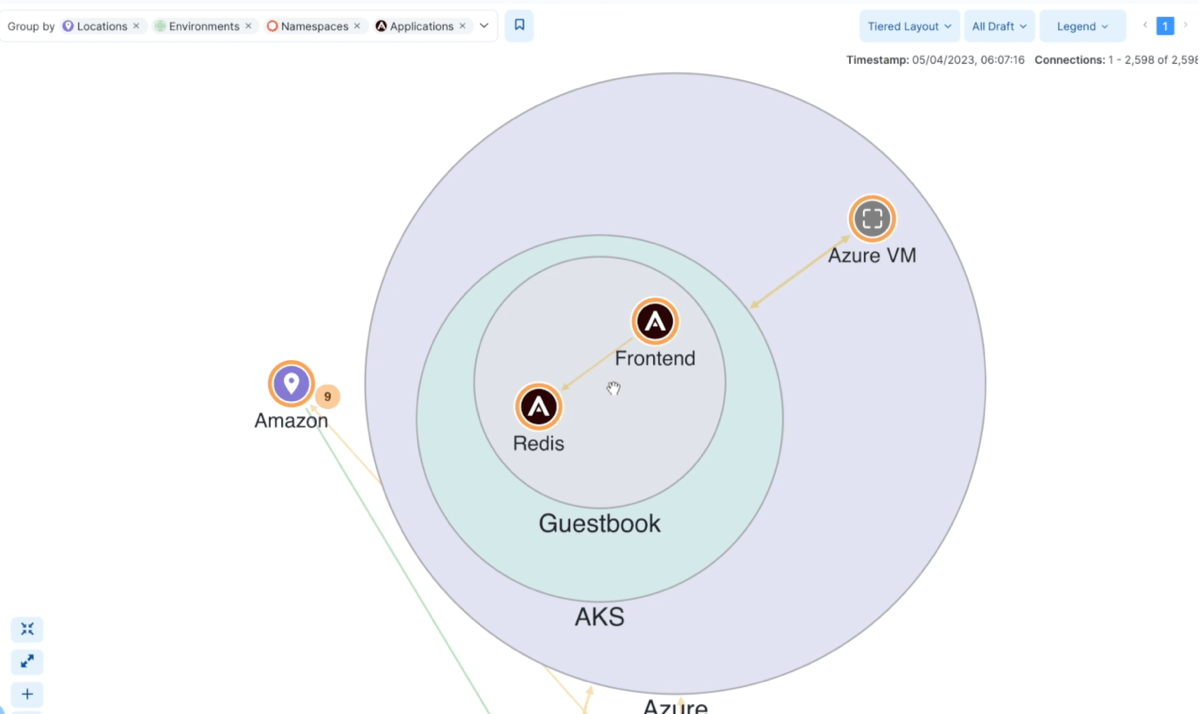
End-to-end visibility: Application dependency mapping
Using Illumio’s map, security teams get a clear and detailed view of how data flows across different segments of the organization’s infrastructure. This delivers comprehensive insights into environment traffic, spanning amongst pods within your clusters as well as any inbound or outbound traffic to these pods into your infrastructure – whether they are on-premises, cloud, or endpoint deployments.
By being able to visualize both pod-to-pod and cluster-to-workload traffic, Illumio can help discover any previously unknown communications and allow you to understand baseline traffic within the environment to craft more informed security policies.
Zero Trust Segmentation across cloud environments
Illumio's Zero Trust Segmentation allows security teams to secure across diverse deployments. By leveraging user-defined labels, organizations can implement fine-grained security policies that span the entire environment. This approach ensures that security measures are consistently applied, regardless of the infrastructure's complexity. It can also prevent a threat where an attacker could take control of a host that runs multiple applications and thus could cause cascading attacks on the entire infrastructure.
While Kubernetes and OpenShift do provide in-built features to secure traffic, these only protect traffic within the cluster itself. When dealing with applications that span across multiple clusters, let alone multiple cloud environments or hybrid environments, it becomes unfeasible to only leverage in-built security features within Kubernetes.
With Illumio, pods and services inherit associated policies dynamically and come online fully secure. Illumio’s user-defined labels ensure consistent segmentation policy within your Kubernetes and OpenShift clusters, as well as across your environment, eliminating the risks that come with a siloed approach to security.

Secure containers quickly and easily with Illumio
Using Illumio to secure containers helps your organization:
- Full visibility: Inventory container clusters and visualize real-time traffic between pods, their hosts, and across the entire infrastructure.
- Uniform policy across environments: Prevent the spread of breaches with a single policy across all workloads – and without hardware.
- Follow DevOps best practices and integrate into existing workflows: Easily deploy with the Helm Chart and support existing CICD processes.
- Seamless segmentation: Simplify container security by using the iptables in the Linux kernel of your Kubernetes host to apply policy.
Ready to learn more about securing your containers with Illumio? Contact us today.
.png)





