Warum die Erkennung ohne Eindämmung scheitert (und wie Sicherheitsdiagramme Abhilfe schaffen können)
Vor einigen Jahren maßen Sicherheitsteams ihren Erfolg daran, wie schnell sie einen Eindringling erkennen konnten.
Viele von ihnen können heute verdächtiges Verhalten innerhalb von Minuten, manchmal sogar Sekunden, erkennen. Moderne KI-gestützte Erkennungswerkzeuge können sogar Signale korrelieren, Anomalien kennzeichnen und Warnmeldungen schneller ausgeben, als es je ein menschlicher Analyst könnte.
Doch die Sicherheitslücken nehmen immer weiter zu.
In einem Vorfall nach dem anderen werden Angreifer zwar frühzeitig entdeckt, schaffen es aber dennoch, Daten zu stehlen und den Betrieb zu stören. Die Warnmeldungen kommen rechtzeitig an, aber der Schaden entsteht trotzdem.
Diese Diskrepanz hat sich zu einer der frustrierendsten Realitäten im modernen Sicherheitsbereich entwickelt. Eine schnellere Erkennung hat nicht zu besseren Ergebnissen geführt.
Der Grund liegt nicht darin, dass die Erkennungswerkzeuge versagen. Es liegt daran, dass die Erkennung allein nie dazu ausgelegt war, die Ausbreitung eines Angriffs zu verhindern.
Ohne eine integrierte Eindämmung von Sicherheitslücken, die auf einem KI-gestützten Sicherheitsdiagramm basiert, können selbst die schnellsten Warnmeldungen weder eine seitliche Ausbreitung verhindern noch den Wirkungsradius begrenzen, sobald ein Angreifer in Ihr Netzwerk eingedrungen ist.
Die Nachweisgrenzen
Die Bedrohungserkennung hat ihre Grenzen. Doch neue KI-Fähigkeiten haben die Erkennung zweifellos intelligenter gemacht.
Modelle des maschinellen Lernens können abnormales Verhalten erkennen und die Alarmmüdigkeit reduzieren. Es kann Sicherheitsteams einen weitaus besseren Kontext liefern als herkömmliche regelbasierte Systeme es je könnten.
Dieser Fortschritt ist wichtig, insbesondere in komplexen Hybrid-Cloud-Umgebungen, in denen die Signale verrauscht sind und sich ständig etwas ändert.
Doch selbst die besten Erkennungsinstrumente konzentrieren sich immer noch auf die Beobachtung. Sie weisen auf Probleme hin, geben Hinweise auf mögliche Ursachen und helfen Analysten bei der Priorisierung einer Reaktion.
Was sie konstruktionsbedingt nicht tun, ist, die nächsten Ziele der Angreifer einzuschränken.
Sobald Angreifer Fuß gefasst haben, ist ihr Ziel, sich weiterzuentwickeln. Sie erkunden die Umgebung, verwenden legitime Anmeldeinformationen wieder und wechseln zwischen verschiedenen Arbeitslasten mithilfe von Standardprotokollen, die Sicherheitsteams oft als sicher ansehen.
Angreifer bewegen sich seitlich – schnell und leise – oft bevor ein Reaktionsprozess auf einen Vorfall vollständig eingreifen kann.
KI-Erkennungswerkzeuge können diese Aktivitäten beobachten. Das kann es nicht verhindern, es sei denn, es gibt bereits andere Maßnahmen zur Durchsetzung von Grenzen.
Genau hier entwickeln sich die meisten Sicherheitslücken von einer einzelnen Kompromittierung zu einem ausgewachsenen Vorfall.
Warum Früherkennung immer noch zu schwerwiegenden Sicherheitslücken führt
Wenn die Erkennung die Hauptsteuerungsmaßnahme ist, wird die Eindämmung reaktiv.
Die Sicherheitsteams erhalten eine Warnmeldung, untersuchen diese, überprüfen die Absicht und entscheiden dann über die weitere Vorgehensweise.
Theoretisch klingt das vernünftig. In der Praxis setzt dies voraus, dass sich Menschen immer schneller bewegen können als Angreifer.
Bei einem aktiven Sicherheitsvorfall ist diese Annahme nicht mehr gültig. Analysten müssen möglicherweise mehrere Warnmeldungen gleichzeitig bearbeiten. Die Maßnahmen zur Reaktion auf einen Zwischenfall erfordern möglicherweise eine Koordination der Teams. Die Eindämmungsmaßnahmen können manuelle Änderungen erfordern, deren Genehmigung und Umsetzung Zeit in Anspruch nehmen.
Die Angreifer warten derweil nicht. Sie bewegen sich weiterhin seitlich, erweitern ihren Zugang und steigern ihre Wirkung mit jeder erfolgreichen Verbindung. Bis zur endgültigen Eindämmung ist der Explosionsradius bereits viel größer als nötig.
Deshalb stehen so viele Teams vor einem scheinbaren Paradoxon. Sie erkennen Angriffe früher als je zuvor, sind aber dennoch weiterhin von Ransomware-Angriffen, Datenverlust und längeren Ausfallzeiten betroffen.
Die Erkennungsfunktion hat ihren Zweck erfüllt. Die Eindämmungsmaßnahmen kamen einfach zu spät.
Die Eindämmung von Sicherheitslücken ist die fehlende Kontrollmaßnahme.
Die Eindämmung verändert die Gleichung. Es beschränkt die Möglichkeiten der Angreifer nach ihrer Entdeckung, nicht davor.
Anstatt sich darauf zu verlassen, dass Menschen unter Druck perfekt reagieren, schafft Containment Grenzen, die ständig bestehen.
Wenn die Eindämmungsmaßnahmen eingerichtet sind, erhält eine kompromittierte Arbeitslast nicht automatisch Zugriff auf alles andere, was sie erreichen kann. Der Ost-West-Verkehr ist eingeschränkt. Vertrauen erstreckt sich nicht automatisch. Seitliche Bewegungswege werden reduziert oder vollständig eliminiert.
In diesem Modell wird die Erkennung leistungsfähiger, da sie innerhalb vorgegebener Grenzen operiert. Eine Warnung signalisiert nicht mehr den Beginn eines Wettlaufs gegen die Zeit, sondern vielmehr ein Ereignis, das bereits unter Kontrolle ist.
Warum dies für den Aufbau von Zero Trust in hybriden Cloud-Umgebungen wichtig ist
Zero Trust basiert auf der Idee, dass der Zugriff explizit, begrenzt und kontinuierlich überprüft werden sollte.
In dynamischen Hybrid-Cloud-Umgebungen ist es nahezu unmöglich, dieses Maß an Kontrolle ohne Einblick in die Verbindungen zu erreichen.
Sicherheitsdiagramme bieten die für Zero Trust erforderliche Transparenz. Und die Segmentierung, als grundlegender Bestandteil jeder Zero-Trust-Strategie, sorgt für deren Durchsetzung. Zusammen gewährleisten sie, dass eine Bedrohung, die von den Erkennungswerkzeugen aufgedeckt wird, bereits durch die Systemarchitektur eingedämmt ist.

Dieser Ansatz ist besonders wichtig in Cloud- und Hybridumgebungen, wo Veränderungen an der Tagesordnung sind und statische Kontrollmechanismen schnell veralten.
Ein kontinuierlich aktualisiertes Sicherheitsdiagramm spiegelt neue Arbeitslasten, Verbindungen und Risiken wider, sobald sie auftreten. Dadurch kann die Eindämmung mit den Veränderungen der Umwelt Schritt halten.
Wie Illumio die Erkennung in die Eindämmung verwandelt
Illumio basiert auf der Idee, dass Sicherheitslücken zwar unvermeidlich sind, flächendeckende Schäden aber nicht zwangsläufig die Folge sein müssen.
Seit Jahren konzentriert sich Illumio auf eines der kritischsten und schwierigsten Probleme im Bereich der Sicherheit: die Verhinderung der seitlichen Ausbreitung, sobald ein Angreifer in Ihr Netzwerk eingedrungen ist.
Was Illumio von anderen Anbietern unterscheidet, ist, dass es Erkennung, Sichtbarkeit und Eindämmung nicht als separate Probleme behandelt. Es verbindet sie durch ein gemeinsames Verständnis davon, wie Umgebungen tatsächlich funktionieren.
Dieses gemeinsame Verständnis bildet den KI-Sicherheitsgraphen.
Kernstück der Illumio-Plattform ist ein kontinuierlich aktualisiertes Echtzeitmodell Ihrer Umgebung. Es bildet Arbeitslasten, Datenflüsse und Risikobeziehungen über Cloud-, On-Premise- und Hybridinfrastrukturen hinweg ab.
Der Sicherheitsgraph spiegelt reale Verbindungen, reales Verhalten und reale Gefährdung wider, während sich die Umgebung verändert.
Alles, was Illumio tut, einschließlich Illumio Insights und Illumio Segmentation, baut auf dieser Grundlage auf.
Illumio Insights: Erkennung mit Echtzeitkontext, nicht nur Warnmeldungen
Illumio Insights nutzt den KI-gestützten Sicherheitsgraphen, um Echtzeit-Überwachung in Ihrer Hybrid-Cloud-Umgebung zu ermöglichen.
Anstatt Ereignisse isoliert zu analysieren, betrachtet Insights das Verhalten im Hinblick darauf, wie Systeme miteinander verbunden sind und wie sich Angreifer tatsächlich bewegen.
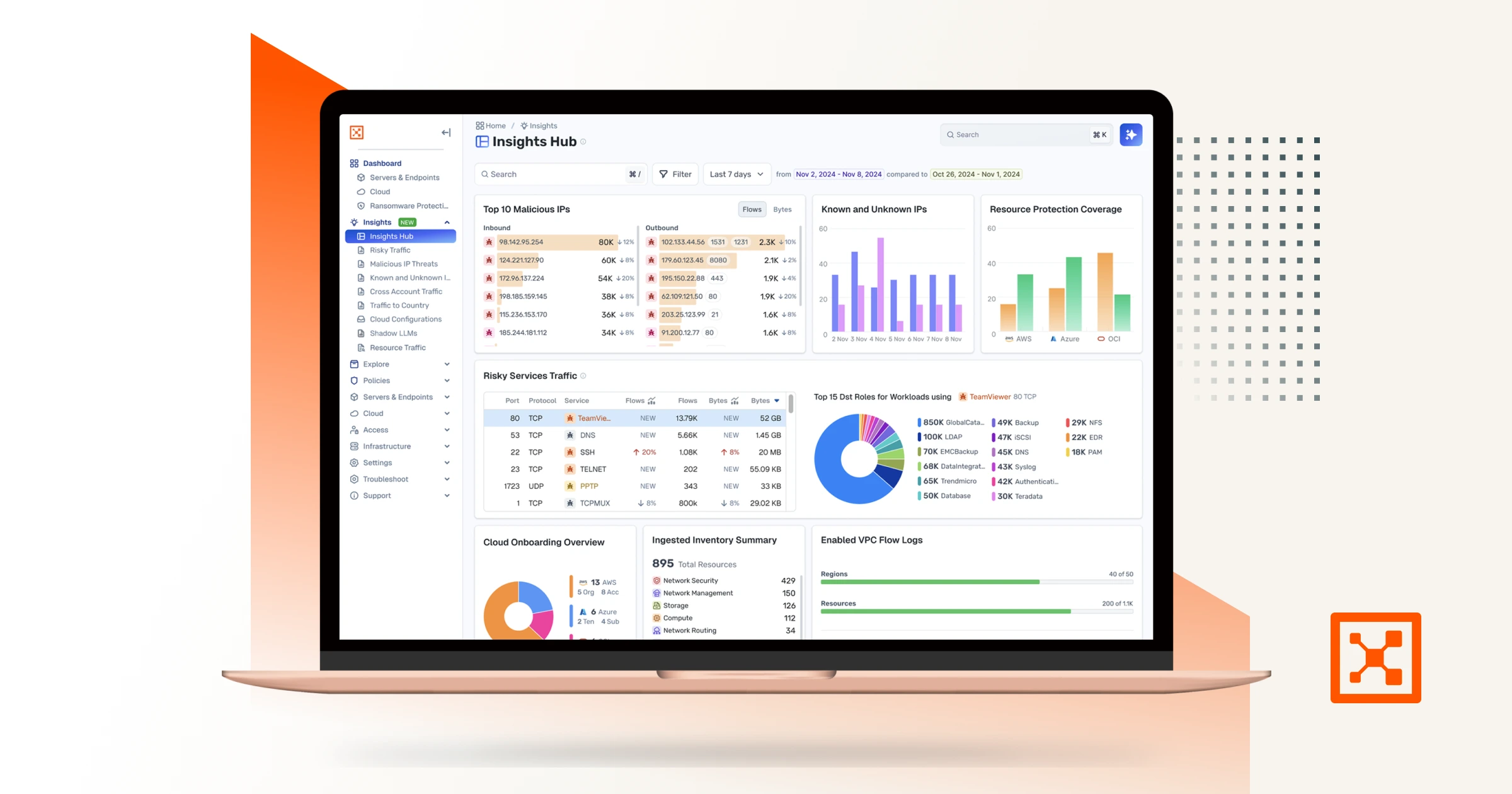
Dies ist deshalb wichtig, weil nicht jede verdächtige Aktivität das gleiche Risiko birgt. Ein Verbindungsversuch, der ins Leere läuft, ist etwas ganz anderes als einer, der einen klaren Weg zu kritischen Systemen eröffnet.
Durch die Möglichkeit, Netzwerkverkehrsflüsse zu beobachten, hilft Insights Teams dabei, aufkommende Bedrohungen früher und mit deutlich mehr Kontext zu erkennen und zu priorisieren. Es hebt riskantes Verhalten, exponierte Angriffswege und abnormale Bewegungsmuster hervor, die darauf hindeuten, dass ein Angreifer versucht, seitlichen Zugang zu erlangen.
Das Ergebnis ist eine bessere Erkennung – nicht weil es mehr Warnmeldungen gibt, sondern weil die Warnmeldungen direkt mit potenziellen Auswirkungen verknüpft sind. Sicherheitsteams können sich auf das Wesentliche konzentrieren, anstatt sich mit Nebensächlichkeiten zu beschäftigen.
Als Teil von Insights bietet Insights Agent einen auf die jeweilige Person abgestimmten, KI-gestützten Assistenten, der kontinuierlich im Hintergrund Ihrer Umgebung läuft. Es agiert wie ein vertrauenswürdiger Teamkollege, der Ihre Sprache spricht, egal ob Sie Bedrohungsanalyst, Compliance-Beauftragter, Cloud-Ingenieur oder in einer anderen Sicherheitsrolle tätig sind, und liefert Ihnen die relevantesten Erkenntnisse direkt.
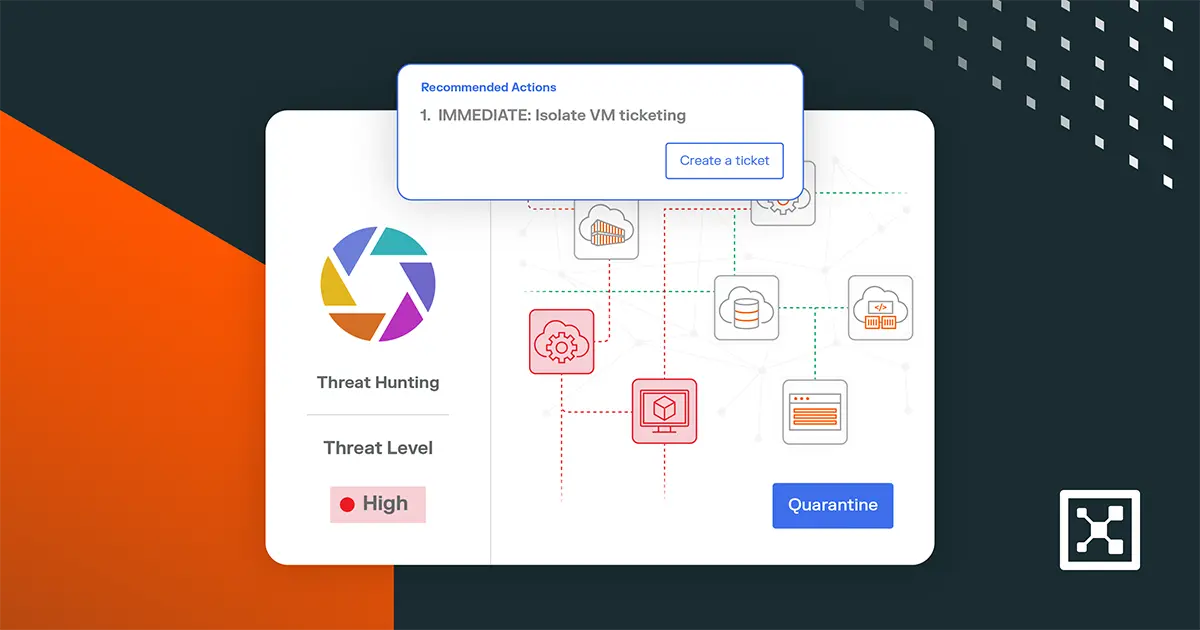
Der Agent analysiert in Echtzeit die Workload-Kommunikation und die Netzwerkflüsse und ordnet verdächtiges Verhalten dem MITRE ATT&CK-Framework zu. Es erkennt Anomalien und erklärt anschließend deren Bedeutung, warum sie wichtig sind und wie man darauf reagieren sollte.
Da es in Illumio Segmentation integriert ist, beschränkt es sich nicht nur auf die Erkennung. Es bietet Ihnen mit einem Klick Eindämmungsoptionen, die Ihnen helfen, seitliche Ausbreitung zu stoppen und gefährdete Arbeitslasten sofort zu isolieren.
Illumio-Segmentierung: Containment durch Design erzwingen
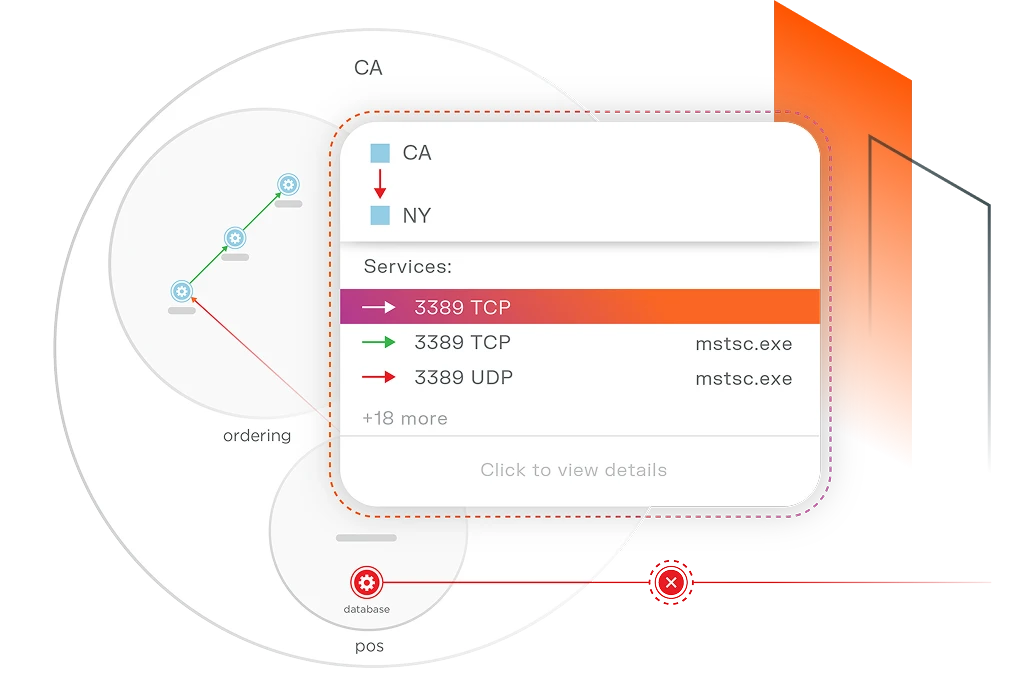
Illumio Segmentation erzwingt den Zugriff nach dem Prinzip der minimalen Berechtigungen zwischen Workloads, um Sicherheitslücken einzudämmen, bevor sie sich in Ihrer Umgebung ausbreiten können.
Anstatt auf flache Netzwerke oder breite Vertrauenszonen zu setzen, beschränkt die Segmentierung, welche Systeme miteinander kommunizieren können und unter welchen Bedingungen.
Wenn eine Segmentierung eingerichtet ist, können Sie laterale Bewegungspfade reduzieren oder eliminieren, bevor ein Angreifer überhaupt versucht, sie auszunutzen. Wenn eine Arbeitslast kompromittiert ist, ist ihre Fähigkeit, andere Systeme zu erreichen, bereits eingeschränkt.
Dadurch wird der Zustand der Eindämmung zum Standardzustand der Umgebung.
Die Erkennung ohne Eindämmung reicht nicht mehr aus
Die Erwartungen an die Geschwindigkeit, mit der Sicherheitsteams Bedrohungen erkennen können, sind durch die künstliche Intelligenz gestiegen. Angreifer haben die Erwartungen hinsichtlich der Geschwindigkeit, mit der sie sich Zugang verschaffen können, erhöht.
Teams, die sich ausschließlich auf die Erkennung verlassen, setzen immer noch auf perfekte menschliche Reaktionen unter unvollkommenen Bedingungen. Diese Wette scheitert öfter, als Führungskräfte zugeben wollen.
Sicherheitsdiagramme verändern das Ergebnis. Sie liefern den Kontext, den Sicherheitsteams benötigen, um die Eindämmung zu unterstützen, und nicht nur das Bewusstsein zu schärfen. Wenn Sicherheitslücken unvermeidbar sind, liegt der Unterschied zwischen einem Sicherheitsvorfall und einer Unternehmenskrise darin, deren Auswirkungen zu begrenzen.
Deshalb ist die Eindämmung nicht länger optional. Es ist die Kontrolle, die aus Früherkennung echte Resilienz macht.
Testen Sie Illumio Insights kostenlos um zu sehen, wie KI-gestützte Sicherheitsgraphen Ihnen helfen, Sicherheitslücken in Echtzeit einzudämmen.





