Illumio + Armisが最新のOT環境を保護する方法

組織は何十年にもわたってサイバーセキュリティ防御に投資してきました。
では、なぜ昨年サイバー攻撃を受けた組織の 58% が依然として業務を停止しなければならなかったと報告しているのでしょうか。
そして、なぜこれらの攻撃により、組織の 40% が多額の収益を失い、35% がブランドのダメージを受けるのでしょうか?
特にオペレーショナルテクノロジー(OT)チームにとって、これらの統計は存続の脅威です。
何十年もの間、工場、公益事業、重要インフラはエアギャップネットワークと境界セキュリティに依存してきました。しかし、デジタルトランスフォーメーションがIT/OTコンバージェンスを推進する中、これらの戦略はもはや成り立ちません。
レガシー産業システムは、クラウドプラットフォーム、IoTセンサー、仮想化ゲートウェイと共存するようになりました。その結果、攻撃対象領域が大きく開かれます。
イルミオとArmisの共同ソリューションは、セキュリティギャップを埋めるのに役立ちます。
OTセキュリティに対するゼロトラストの義務化
最新のOT システムを保護するのは簡単ではありません。今日のセキュリティ チームは次のことを強いられています。
- エアギャップ環境からハイブリッド環境への移行
- コンテナ化されたゲートウェイとSASEアーキテクチャの導入
- IaaS と PaaS の統合を管理する
しかし、このモダナイゼーションはセキュリティへの投資を上回ることが多く、危険な「セキュリティ変革の赤字」を生み出します。
古いパデューモデルは、産業システムが孤立していたときに機能しました。

しかし、コンテナ化されたゲートウェイ、ハイブリッド環境、仮想化されたOTの世界では、静的な境界は崩壊します。その後、パデュー モデルは現代の複雑さを反映するように更新されました。
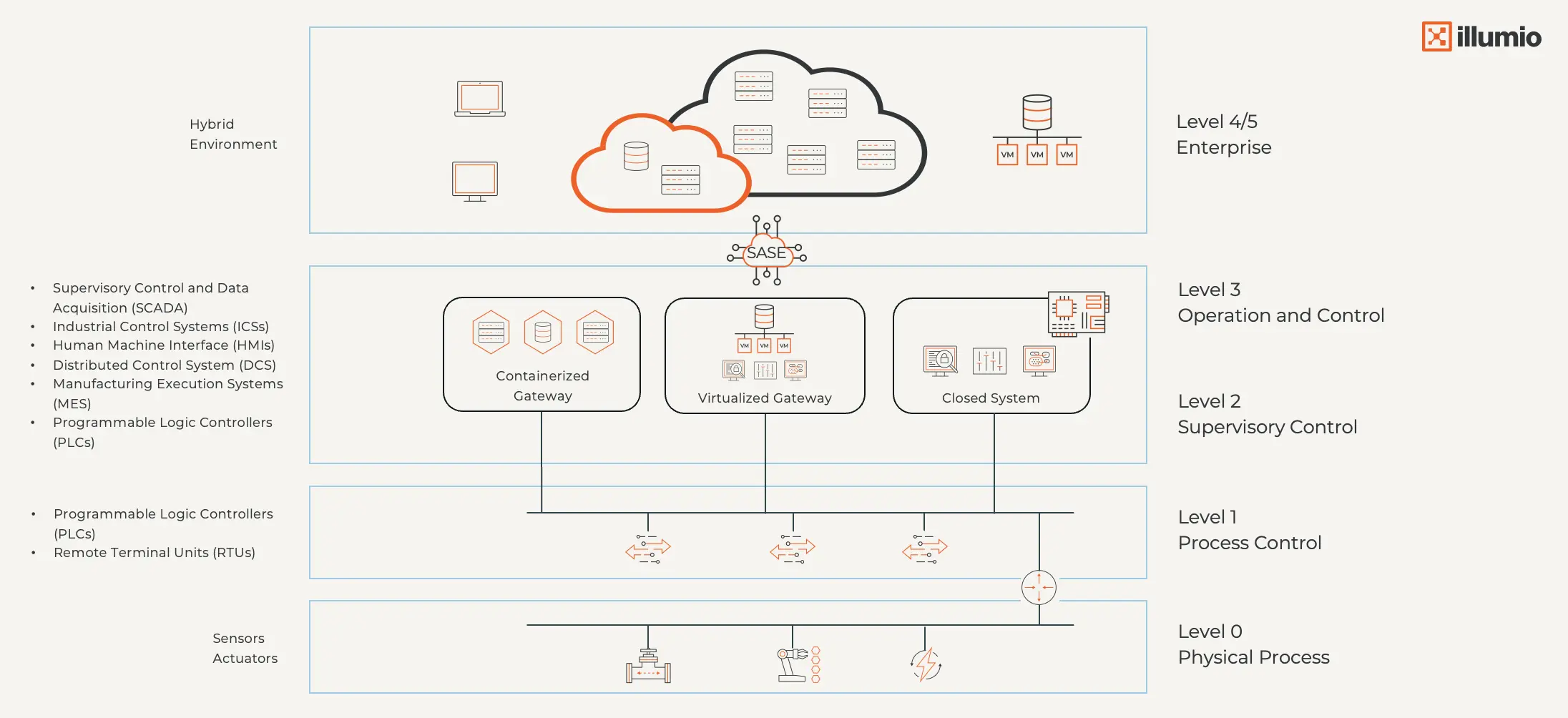
OT 環境に対するゼロ トラスト戦略こそが唯一の前進の道です。すべてのユーザー、デバイス、ワークロードを継続的に検証し、アクセスを必要なものだけに制限し、環境やリスクの変化に応じてポリシーを自動的に適応させます。
イルミオ + Armis: OT におけるゼロトラストへの実践的な道
Armis と Illumio は、複雑な産業環境におけるゼロ トラストのあり方を再定義しています。
これらを組み合わせることで、運用を中断することなく、資産の詳細な可視性とリアルタイムのセグメンテーションおよび適用を組み合わせます。
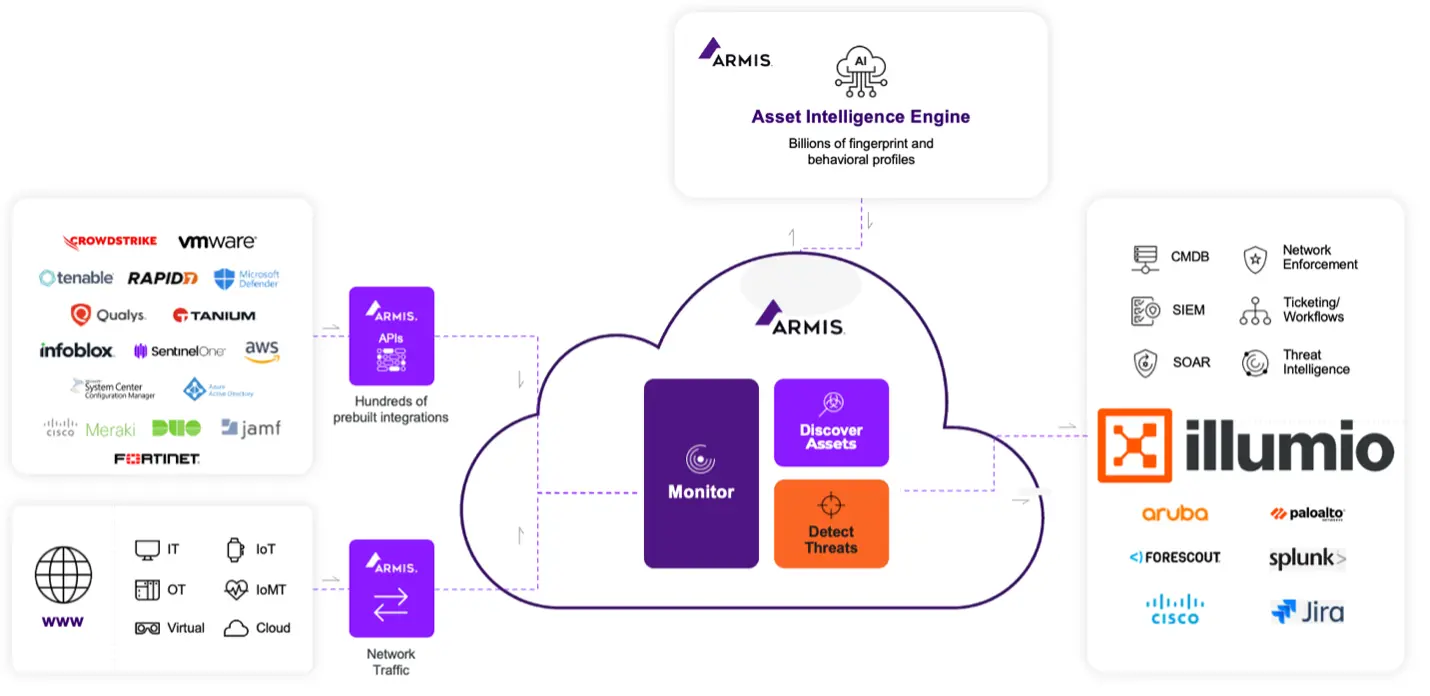
Armis:IT、OT、IoTを見て理解する
Armis は、IT、OT、IoT 全体にわたる詳細な可視性を実現します。
そのパッシブ監視により、デバイスの種類と役割、ネットワークの動作と通信パターン、パデュー モデル内での配置、リスクと脆弱性のコンテキストが明らかになります。
そのインテリジェンスは、セグメンテーションと保護の基盤です。
Armisは、IT、OT、IoTの接続されたすべてのデバイスを受動的に監視し、以下に対する比類のない可視性を提供します。
- デバイスの種類と役割
- ネットワークの動作と通信パターン
- Purdue モデル内のレイヤーの配置
- リスクと脆弱性のコンテキスト
このコンテキストは、重要なOT資産をセグメント化して保護するために不可欠です。
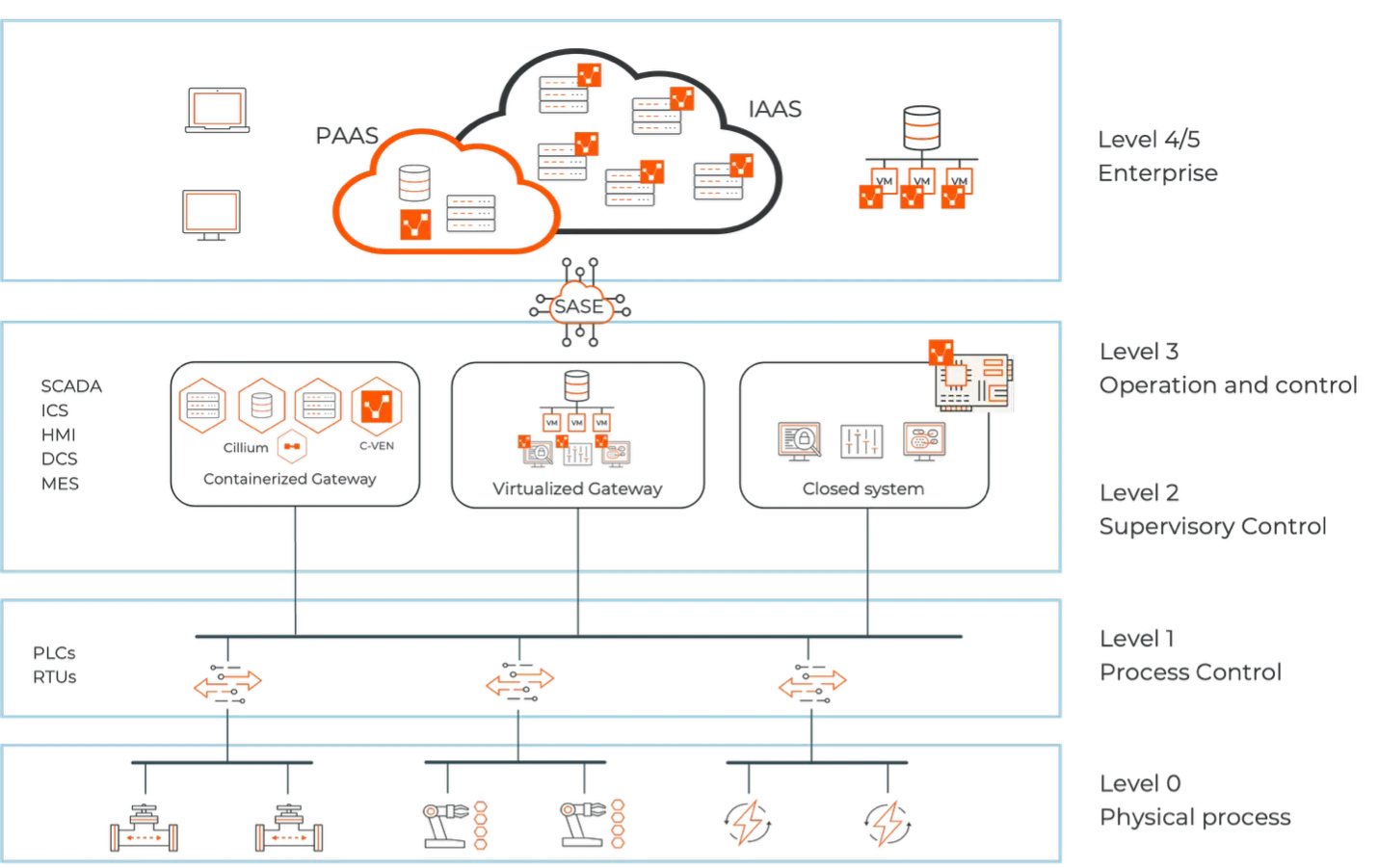
イルミオ:リスクなしでセグメンテーションを実施
イルミオはArmisから洞察を取り入れ、適応性のあるリスクに基づいたセグメンテーションポリシーを適用します。
これも:
- Segmentation パデューモデルを念頭に置いて: SCADA、DCS、MES、ERP間のトラフィックをロックダウンし、すべてのシステムが通信すべき内容のみを通信できるようにします。
- 脅威への動的対応: Armisが不審なものを見つけると、イルミオは即座に対応し、脅威が広がる前にアクセスを遮断したり、デバイスを隔離したりします。
- エージェントレス制御: 壊れやすいICSやPLCデバイスに触れずに保護します。Illumio VEN/NENアーキテクチャは、エージェントを必要とせずにポリシーを安全に適用します。
このアプローチは安全で拡張が容易であり、最も厳しく規制された環境であっても、アクティブな攻撃中でも運用の回復力を維持します。
イルミオ + Armis統合の主な利点
イルミオとArmisの共同ソリューションは、OTチームとセキュリティチームが直面する日々の課題のために構築されています。
運用の中断なし
ほとんどのセキュリティツールは、エージェントや大規模なネットワーク変更により速度が低下します。しかし、イルミオとアーミスは異なるアプローチをとっています。
軽量アーキテクチャは、PLC、RTU、SCADAコントローラーなどの壊れやすいデバイスに触れることなく、重要なシステムを保護します。
イルミオはVEN/NENモデルを通じてポリシーを適用し、Armisは受動的でエージェントレスな可視性を提供するため、リスクを追加することなくすべてを確認し、セキュリティを維持できます。
リアルタイムに適応するクローズドループ防御
検出と適用はサイロ化できません。彼らはお互いに餌を与え合っています。
Armisが奇妙なプロトコルアクティビティやパブリックIPにpingを送信するデバイスなど、不審なものを見つけると、イルミオは即座にロックダウンするか、アクセスを強化します。その結果、応答が速くなり、滞留時間が短縮され、手動介入を待たずに爆発半径が小さくなります。
コンプライアンスに配慮した可視性と監査証跡
規制の厳しい業界では、ハイブリッド環境を可視化することで生き残ることができます。
Illumio + Armisの統合により、監査対応のログ、ポリシーシミュレーション、変更前チェックが提供されるため、チームは自信を持って更新を行うことができます。
NIST、IEC 62443、ISO 27001のいずれに準拠している場合でも、この共同ソリューションにより、業務を遅らせることなく、コンプライアンスをより明確、迅速、簡単に行うことができます。
真のビジネス価値を備えた統合セキュリティ
イルミオとArmisは協力して、より強力な防御、よりスムーズな監査、より安全なモダナイゼーションなど、最も重要な成果をもたらします。
横方向の移動が広がる前に阻止し、ランサムウェアを発生源で遮断し、明確で監査可能な制御によってコンプライアンスを簡素化します。
また、SASE、仮想化ゲートウェイ、ハイブリッドクラウドなど、OT環境が進化するにつれて、ソリューションも適応します。これにより、可視性や稼働時間を失うことなく回復力を得ることができます。
進行状況と保護のどちらかを選択する必要はありません。イルミオとArmisは、最も重要なシステムが一貫して安全に保たれていることを知っているため、自信を持ってモダナイズできます。
OT変革のギャップを埋める
サイバー攻撃は衰えることはなく、OT環境はますます複雑化しています。
エアギャップ、静的な境界、サイロ化されたツールなどの従来の防御は、まったく追いつくことができません。「セキュリティ変革の赤字」の解消が遅れるたびに、重要なインフラストラクチャはランサムウェア、ダウンタイム、規制リスクにさらされることになります。
そのため、イルミオ + アームスの統合がこれまで以上に重要になっています。
資産の詳細な可視性とリアルタイムのセグメンテーションおよび適用を組み合わせることで、本番環境に対応し、コンプライアンスに配慮し、最新のOTの現実に合わせて構築されたゼロトラストセキュリティを提供します。
次の事件が変化を余儀なくされるのを待ちきれません。イルミオとArmisを使用すると、今すぐレジリエンスを構築できるため、組織は混乱を恐れることなく革新、最新化、成長できます。


.webp)
%20(1).webp)



