影を追いかけるのはもうやめよう:Illumio Insightsによるよりスマートな脅威ハンティング
今日の攻撃者は動きが速いです。そして AI の助けにより、これまで以上にステルス性が高まりました。
従来の検出ツールでは、アナリストに大量のアラートが送信されることがよくあります。適切な文脈がなければ、それは影を追いかけるようなものです。
ここで脅威ハンティングが役立ちます。つまり、攻撃者が環境全体に広がる前に、侵害の兆候を積極的に探すのです。
Illumio Insights はこれをさらに一歩進めます。ワークロード間およびワークロードからインターネットへのトラフィックを詳細に可視化することで、防御側は他のツールが見逃すものを把握できるようになります。
Insights は、誤検知を追跡するのではなく、脅威ハンターが実際の攻撃パスに素早く焦点を絞り、侵害が重要なリソースに広がる前にそれを封じ込めるのに役立ちます。
現代の脅威ハンティングの課題
攻撃者がより巧妙化する一方で、防御側は境界の可視性だけで十分であるという考えなど、時代遅れの仮定に依拠し続けています。
ハイブリッド インフラストラクチャと拡大し続けるクラウド ワークロードの世界では、従来のアプローチでは不十分です。
それで何が邪魔をしているのでしょうか?次のような一般的な問題点により、効果的な脅威ハンティングが本来よりも困難になっています。
- 東西の盲点:ほとんどのツールは南北の周辺トラフィックに焦点を当てているため、 横方向の動きは不明瞭です。
- ハイブリッド、マルチクラウドの複雑さ: Amazon Web Services (AWS)、Microsoft Azure、Google Cloud Platform (GCP)、Oracle Cloud Infrastructure (OCI)、オンプレミスのワークロードが混在すると、相関関係の把握が困難になる可能性があります。
- アラート疲労:シグナルが多すぎて優先順位が不十分なため、チームはアラートに溺れてしまいます。
- 調査の遅延:データ サイロによりツール間の切り替えが頻繁に発生し、対応が遅くなります。
こうした課題は、単に捜査を遅らせるだけではありません。それらは、敵が容易に悪用できる危険な盲点を生み出します。
現代の脅威に打ち勝つために、セキュリティ チームには、よりスマートな可視性、より緊密な統合、そして横方向の移動を正確に特定して阻止するより迅速な方法が必要です。
Illumio Insightsが脅威ハンティングを簡素化する方法
Illumio Insights は、AWS、Azure、GCP、OCI、オンプレミス環境、ファイアウォール、VPN などからフローログを取り込みます。AI セキュリティ グラフを使用して、承認または拒否されたすべての接続を 1 か所にマッピングします。
脅威ハンターとして、Insights ハブを使用すると、ネットワーク上のリソースと通信する悪意のある IP、外部データ転送、環境内の高リスク サービスなど、環境に対するすべての脅威を確認できます。
次に例を示します。
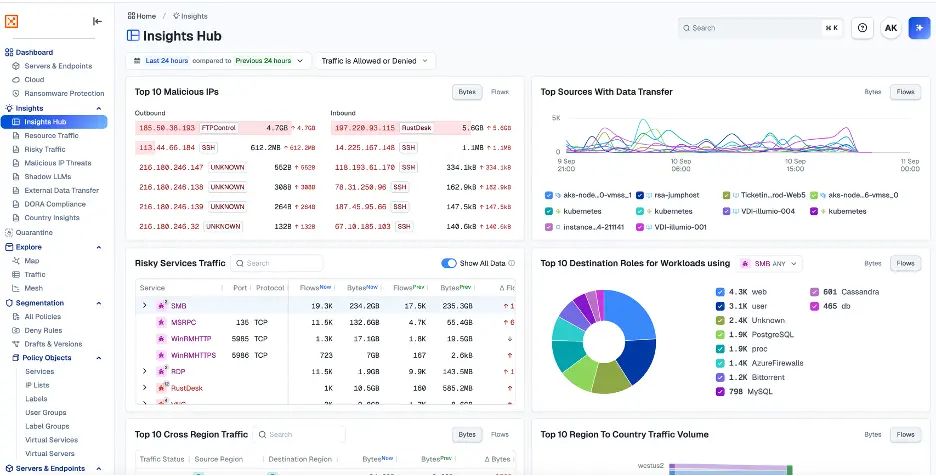
ダッシュボードから、ハンターは異常をすぐに見つけることができます。たとえば、悪意のある IP からの Rustdesk トラフィックの急増が目立ちます。
接続の詳細を調べると、悪意のある IP と内部仮想マシン (VM) の間で Rustdesk トラフィックが継続的に発生していることがわかります。
このパターンは単なる一回限りの調査ではありません。これは、攻撃者が環境内でアクティブなリモート セッションを確立したことを示します。
.webp)
Rustdesk 自体は本質的に悪いものではありませんが、既知の悪意のある IP がそれを介して接続すると、警鐘が鳴ります。脅威ハンターは数回クリックするだけで、攻撃者の経路を追跡できます。
- 攻撃者はまず環境を詳細に調査し、さまざまなリソースを発見するまでスキャンと調査を行います。これには、多くの組織が日常的に依存している重要な PaaS サービスが含まれます。
- この探索中に、彼らは、環境の最も貴重な資産を保護する機密の資格情報と秘密が保存されているキー ボールトを発見し、アクセスできるようになりました。
- 攻撃者は盗んだキーを使って、顧客レコードが満載のデータベース、高価値のストレージ アカウント、コア アプリケーションをサポートするキャッシュ レイヤーなどのミッション クリティカルなシステムへと体系的に攻撃を進めます。
- 攻撃者はこれらの資産を制御することで、環境から機密データを流出させる経路を確立します。彼らは、気付かれないようにしながら、自分たちの管理下にある外部ストレージ アカウントに資金を流し込みます。
.webp)
この時点で、ハンターは攻撃を確認するだけでなく、Illumio Insights によるワンクリック隔離で攻撃を即座に阻止することができます。この機能により、脅威ハンターは侵害されたワークロードを即座に分離し、環境の残りの部分や外部の宛先との通信を防ぐことができます。
これを強力にしているのはスピードです。別のファイアウォール コンソールに移動したり、手動での変更を待ったりする必要はありません。封じ込めは即時に行われます。
また、Illumio は隔離されたシステムへの制御されたアクセスを提供するため、管理者とセキュリティ オペレーション センター (SOC) チームは、さらなる拡散のリスクを負うことなく、引き続きログインして調査、フォレンジック収集、修復を行うことができます。
つまり、脅威ハンターは攻撃経路を視覚化し、それをリアルタイムで封じ込めることができるのです。

法医学は検疫で終わるわけではありません。過去のフローデータがあれば、ハンターは次の質問をすることができます。
- このワークロードが最初に悪意のある IP と通信したのはいつですか?
- どのくらいのデータが転送されましたか?
- 他のワークロードでも同様な疑わしい動作が見られますか?
このコンテキストにより、調査が迅速化され、優先順位が明確になり、対応が強化されます。
Illumio Insights: 事後対応型防御から予防型防御へ
脅威ハンティングは、悪意のある行為者を捕まえることだけではありません。また、リスクを軽減し、感染が広がる前に横方向の移動を阻止することも重要です。
Illumio Insights を使用すると、セキュリティ チームはサイロ化されたアラートからコンテキストに応じた攻撃パスの可視性に移行できます。つまり、次のようになります。
- すべてのデータを 1 か所に集めることで、調査を高速化できます。
- 実際の攻撃パスに基づいた、よりスマートな優先順位付け。
- 統合検疫によるより強力な対応。
- ハイブリッドおよびマルチクラウド環境全体にわたるスケーラビリティ。
防御者は、ノイズに埋もれることなく、実用的なインテリジェンスを獲得し、攻撃者よりも重要な一歩先を行くことができます。
試す Illumio Insights 14日間無料トライアル 今日。




