.png)

Denken Sie wie ein Angreifer
Warum Sicherheitsdiagramme die nächste Grenze der Bedrohungserkennung und -abwehr sind
Cyberbedrohungen eskalieren, entwickeln sich weiter und werden von Tag zu Tag komplexer. Herkömmliche Sicherheitstools haben Mühe, Schritt zu halten. Um Ihr Unternehmen effektiv zu verteidigen, müssen Sie die Denkweise eines Angreifers annehmen. In diesem E-Book berichtet der Cybersicherheitsexperte Dr. Chase Cunningham (Dr. Zero Trust) erklärt, wie Security Graphs – eine revolutionäre Methode zur Abbildung Ihrer Cyber-Umgebung – Ihnen helfen können, versteckte Bedrohungen aufzudecken, Risiken klar zu visualisieren und schnell zu reagieren.

Du wirst lernen:
- Wie Sicherheitsdiagramme einen beispiellosen Einblick in die digitale Landschaft Ihres Unternehmens bieten.
- Praktische Möglichkeiten, Bedrohungen früher zu erkennen, indem versteckte Verbindungen und verdächtige Verhaltensweisen visualisiert werden.
- Die strategische Rolle der Graphenanalyse bei der Implementierung eines Zero-Trust-Cybersicherheits-Frameworks.
- Beispiele aus der Praxis, die veranschaulichen, wie führende Unternehmen graphenbasierte Sicherheit einsetzen, um Sicherheitsverletzungen zu verhindern.
- Zukünftige Trends, einschließlich der Frage, wie KI und maschinelles Lernen die Leistungsfähigkeit von Graphanalysen bei der Bedrohungserkennung verstärken werden.
Holen Sie sich noch heute Ihr kostenloses Exemplar.
Höhepunkte
Wesentliche Vorteile
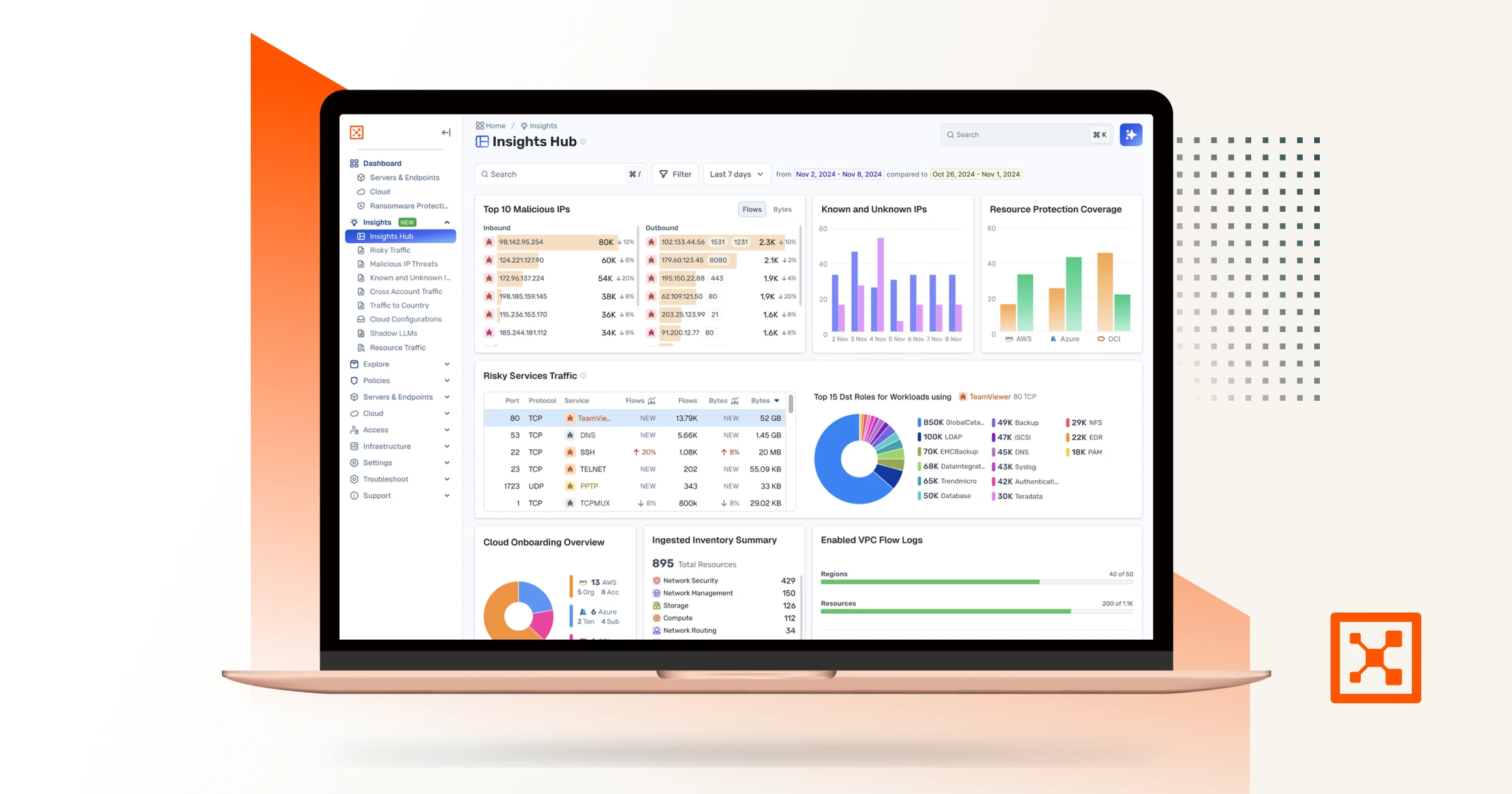
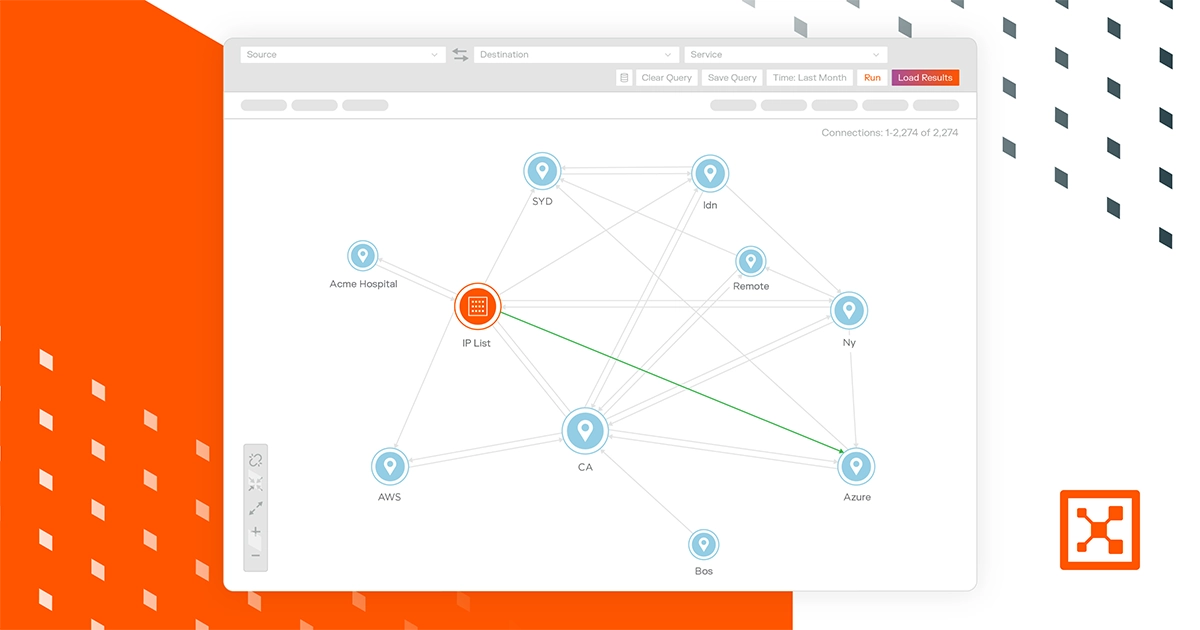
Asset-Vorschau






Gehen Sie von einer Sicherheitsverletzung aus.
Minimieren Sie die Auswirkungen.
Erhöhen Sie die Resilienz.
Sind Sie bereit, mehr über Zero Trust-Segmentierung zu erfahren?