Illumio がハイブリッド・マルチクラウド環境でランサムウェアの横展開を阻止する方法
2019年3月、世界最大のアルミニウム製造会社の一つであるノルスク・ハイドロにとって、ランサムウェアがシステムを停止させるまでは、他の火曜日の朝と何ら変わらない朝が始まった。
攻撃者は一夜にして、同社の全世界のネットワーク上にある数千台のサーバーとPCを暗号化した。このため、複数の国の工場では、IT チームが被害の抑制と再建に努める中、デジタル システムを停止して手動操作に切り替えることを余儀なくされました。
これは、ランサムウェアが境界をすり抜けると、世界規模で業務を急速に混乱させる可能性があることを強く思い知らせるものでした。
残念ながら、この話は例外ではなく、規則になりつつあります。
今日の複雑なハイブリッド マルチクラウド環境では、ランサムウェアが急速に侵入し、拡散します。そのため、横方向の移動は現在、サイバー攻撃の最も危険な段階となっています。
だからこそ、組織には予防以上のものが必要なのです。侵害の封じ込め、攻撃パスの可視性、そしてランサムウェアをリアルタイムで阻止する方法が必要です。
この投稿では、Illumio が隠れた攻撃経路を明らかにして侵害を封じ込め、ハイブリッド マルチクラウドが停止する前にランサムウェアの横方向の拡散を阻止する方法について説明します。
ランサムウェアの根本的な問題:横方向の移動
最新のランサムウェアは、ハイブリッド IT における横方向の移動を悪用して成功します。
攻撃者は 1 台のマシンに侵入してそこに留まるわけではありません。攻撃者はクラウド ワークロード、仮想マシン、エンドポイントを巡回し、価値の高いターゲットを探し出して被害を拡大します。
この動きは内部的に(ネットワークの東西方向に)発生し、境界防御に重点を置いた従来のセキュリティ ツールでは検出されないことがよくあります。

これが、 ハイブリッド環境におけるランサムウェアが非常に危険な理由です。攻撃者が内部に侵入すると、ほとんど気付かれずに活動できるようになります。
ハイブリッド インフラストラクチャにより、状況はさらに複雑になります。アプリケーションは現在、オンプレミスのデータセンター、パブリック クラウド、コンテナ クラスター、SaaS 統合にまで広がっています。
ワークロードは常に変化します。トラフィックフローは動的かつ一時的です。従来の防止および検出ツールは、このレベルの複雑さに対応するようには構築されていませんでした。
ランサムウェアの拡散を防ぐために、組織は検出と対応へのアプローチ方法を再考する必要があります。きめ細かな可視性は、ハイブリッド IT ランサムウェア防止の基盤です。
ランサムウェア攻撃を阻止するには検出だけでは不十分な理由
多くの場合、セキュリティ チームは、被害が始まってからアラートを送信する検出ツールに依存しています。
従来のシステムが異常を検出する頃には、ランサムウェアがすでにシステムを暗号化したり、バックアップを削除したり、管理者の資格情報を取得したりしている可能性があります。
ここで重要な指標は速度です。平均検出時間 (MTTD) と平均対応時間 (MTTR) は、ランサムウェアの封じ込めに重要です。しかし、多くのSOC チームでは、攻撃者が環境内をどのように移動したかを理解するのに、依然として数時間、場合によっては数日もかかります。
この遅れが、単発のインシデントを企業全体の危機に変える原因となります。
組織に必要なのは、代わりに次のことを可能にするプラットフォームです。
- 攻撃される前に、あらゆる可能性のある攻撃パスを確認します。
- クラウドおよびデータセンターのワークロード全体の悪意のある動きをリアルタイムで検出します。
- 侵害を受けたシステムを隔離し、さらなる拡散を防ぐために直ちに行動してください。
Illumioはランサムウェアの拡散を阻止します
今日のハイブリッド マルチクラウド環境でランサムウェアを阻止するには、アラートを増やすだけでは不十分です。攻撃者がどこにいるのかをリアルタイムで把握し、攻撃の拡大を阻止する必要があります。
まさにそれがIllumioが提供するものです。Illumio プラットフォームは、 クラウド検出および対応 (CDR) 用の Illumio Insights と、リアルタイムの侵害封じ込めおよび横方向の移動保護用の Illumio Segmentation を 組み合わせています。
これらのソリューションを組み合わせることで、セキュリティ チームは、ランサムウェアの動作を早期に検出し、リスクの高いワークロードを即座に分離し、将来の拡散を阻止するセグメンテーション ポリシーを適用するための可視性、制御性、俊敏性を獲得できます。
従来のツールは静的なルールや事後ログに依存していますが、Illumio は動的なハイブリッド環境全体での侵害の封じ込めを目的として構築されています。ワークロードとアプリケーションが実際にどのように通信するかを監視し、クラウド、データセンター、エンドポイント、コンテナ全体の東西トラフィックのライブ可視性を提供します。
Illumio Insights
Illumio Insights は、ランサムウェア防御に新たなレベルの可視性をもたらします。
既知の脅威をスキャンするのではなく、ランサムウェアがワークロード間、クラウド環境とオンプレミス環境間、そして最も重要なシステムにどのように移動するかをモデル化します。
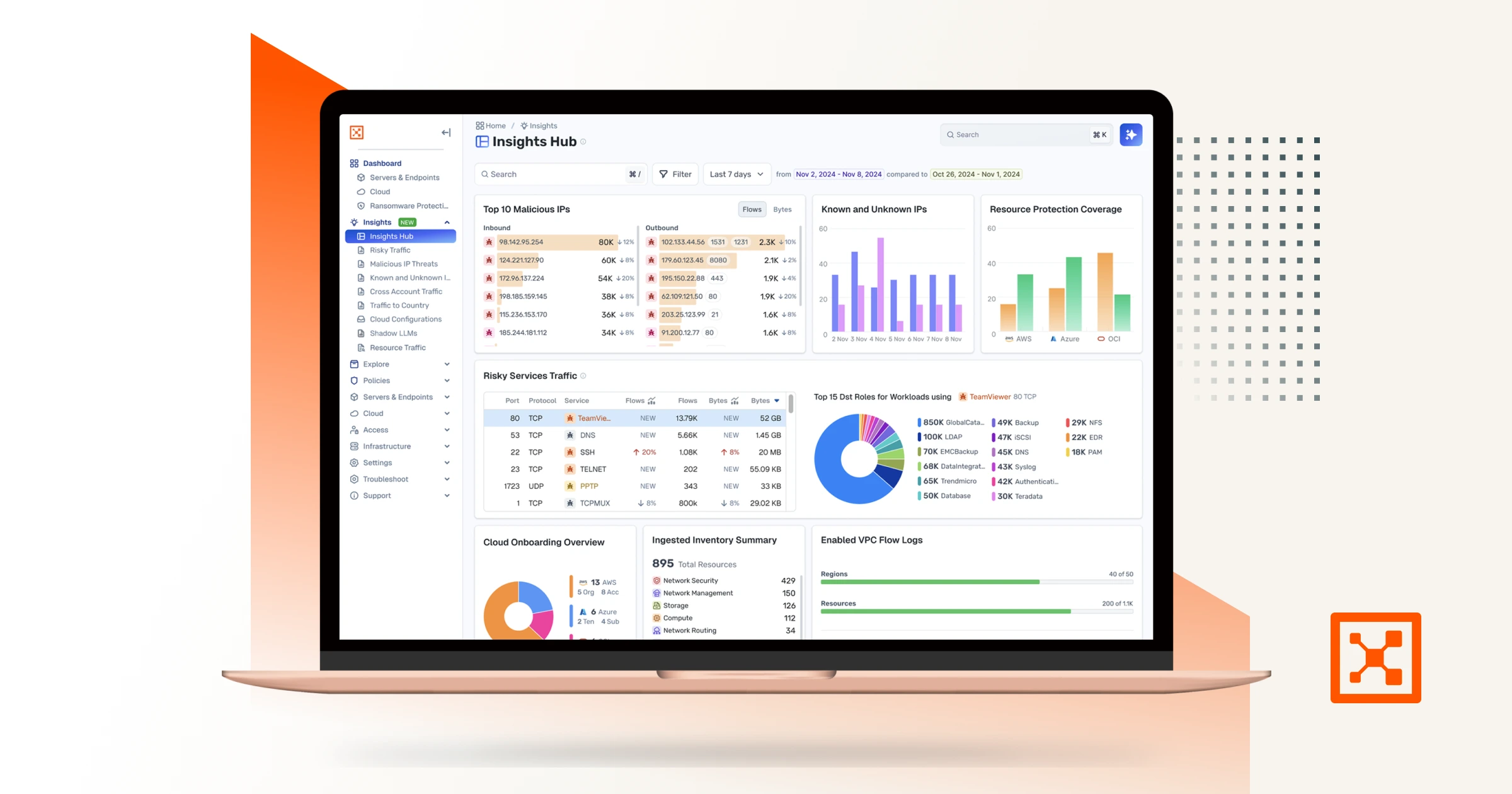
AI セキュリティ グラフを活用した AI 主導の分析により、攻撃者が悪用する可能性のある高リスクの経路を明らかにします。次に、ギャップを埋めるためのセグメンテーション ポリシーを自動的に推奨し、Illumio Segmentation を通じて即座に適用できます。
Insights Agent 機能は、セキュリティ オペレーション センター (SOC) アナリスト、CISO、インフラストラクチャ エンジニア、アプリケーション所有者向けにカスタマイズされた役割固有のダッシュボードも提供します。つまり、各チームは最も関連性の高いリスクを把握し、どのように対応するかを正確に把握していることになります。
Illumioセグメンテーション
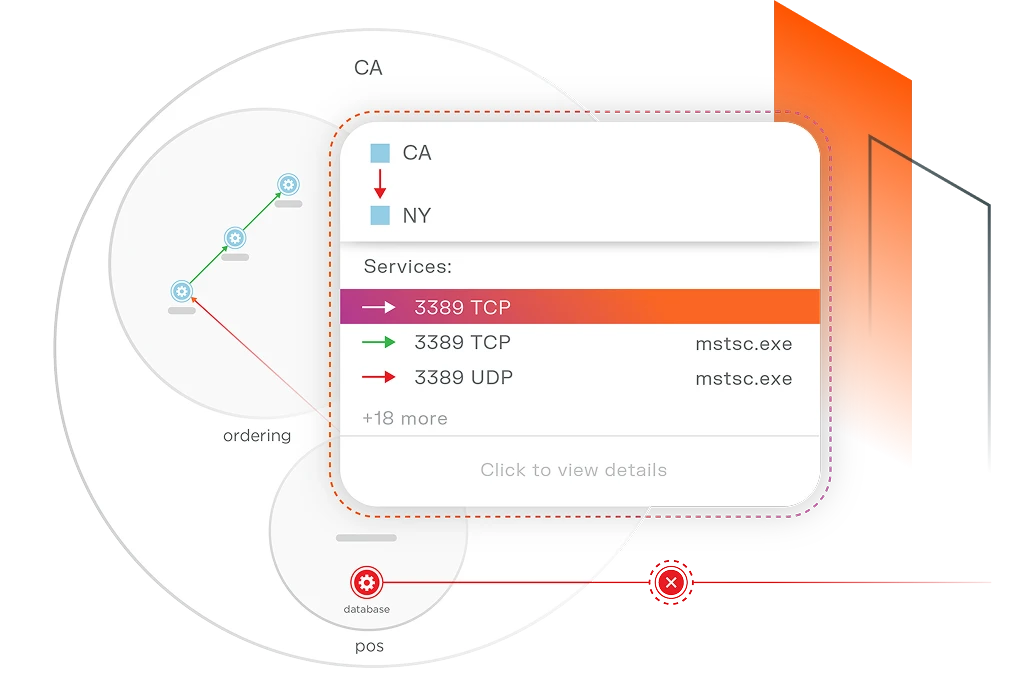
Illumio Segmentation はそれらの洞察を行動に移します。
数回クリックするだけで、ネットワークを再構築したり複雑なファイアウォール ルールを記述したりすることなく、侵害されたワークロードを分離し、 最小権限のアクセスを強制し、ランサムウェアが他のシステムに侵入するのを防ぐことができます。
セグメンテーションはワークロード レベルで動作するため、パブリック クラウド、プライベート データ センター、ハイブリッド インフラストラクチャ、コンテナー全体でシームレスに機能します。
仮想ローカル エリア ネットワーク (VLAN) や厳格なゾーニングに依存しません。環境の変化に応じてリアルタイムで適応し、ビジネスのペースに合わせたスケーラブルなランサムウェア セグメンテーション ソリューションを提供します。
Illumioがランサムウェアの横展開を防ぐ4つの方法
Illumio は、エンドツーエンドの可視性と制御を提供することで、ハイブリッド IT におけるランサムウェアの拡散を防御します。
1. 起こる前にイメージする
ほとんどのツールは、ランサムウェアが何を行ったかを教えてくれます。Illumio は、実際に動く前に何ができるかを示します。
Illumio Insights は、環境のリアルタイムのトラフィック パターンと関係をマッピングし、侵害の潜在的な爆発半径を明らかにします。これにより、セキュリティ チームは、公開されているパスと有害な組み合わせを事前に特定し、攻撃者が悪用する前にセグメント化することができます。
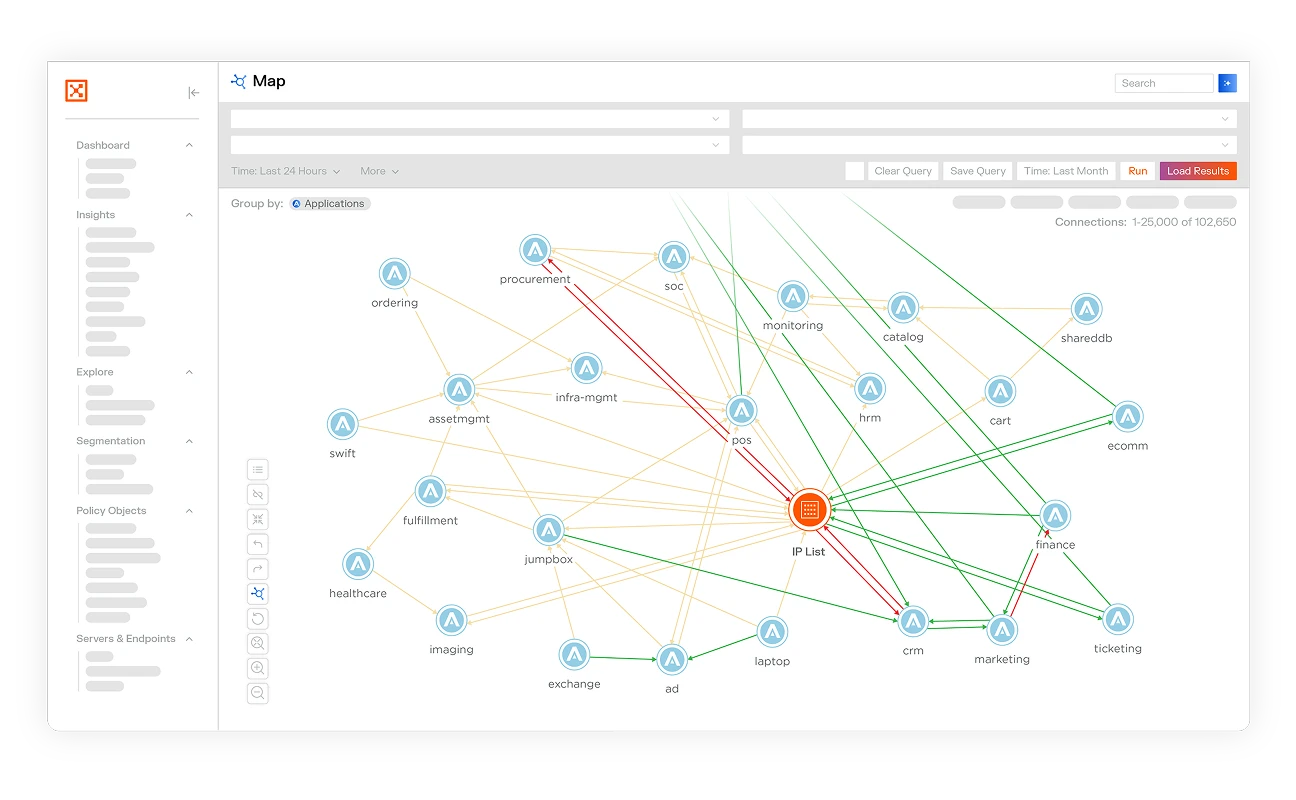
2. 横方向の動きを即座に検知する
ランサムウェアは急速に拡散します。Illumio はそれをより速く検出します。
Insights は、ワークロード全体の動作の変化を継続的に監視し、脅威が既知のシグネチャをまだトリガーしていない場合でも、疑わしいピボットや東西トラフィックの異常にフラグを付けます。
被害が発生した後だけでなく、ランサムウェアの動きを捕捉するために必要な可視性です。
3. 感染したワークロードを即座に隔離する
脅威が検出されると、Illumio Segmentation により即座に対応できるようになります。
環境全体を停止したり、時間のかかる手動介入に頼る代わりに、ワンクリックのポリシー適用で感染したシステムを外科的に隔離できます。これにより爆発範囲が制限され、影響を受けないサービスの稼働時間が維持されます。
4. 回復力のあるセグメンテーション戦略を構築する
Illumio は、トラフィックを継続的に分析し、露出を減らす新しいポリシーを推奨することで、チームがゼロ トラスト アーキテクチャを徐々に進化させるのを支援します。
これにより、ハイブリッドおよびマルチクラウド インフラストラクチャ全体で、ランサムウェア封じ込め戦略が最新かつ適応性に優れ、実行可能な状態に保たれます。
Illumioが従来のランサムウェア対策ツールに勝る理由
ファイアウォール、エンドポイント検出、従来のネットワーク セグメンテーションなど、多くの従来のセキュリティ ソリューションは、依然として古い前提に基づいて動作しています。彼らは、攻撃者を締め出すことができ、環境は変化せず、アラートによって救われると想定しています。
現実には、ランサムウェアは誰にも気付かれずに静かに侵入し、横方向に拡散していくことが多いのです。
ファイアウォール ベースのツールは、依然として、ネットワークに出入りするトラフィックである南北トラフィックに重点を置いています。
ハイブリッド インフラストラクチャ内の東西方向の移動を追跡またはブロックするのは困難です。ほとんどの場合、集中的な手動構成、静的なスコープ定義、事前定義されたゾーンが必要ですが、そのどれもが動的なクラウド ワークロードに対応できません。
では、いつ返答すればよいのでしょうか?ランサムウェアが拡散してから、カスタム ルールを記述したり、変更を待ったりすることになりますが、これには何時間もかかる可能性があります。
対照的に、Illumio は従来のツールでは見逃されていたものも認識します。
ワークロード間のリアルタイム通信を即座に可視化できます。ランサムウェアが最もよく実行されるパスにフラグを付けます。また、横方向の移動が始まる数分前にそれらのパスをブロックする機能も提供します。
攻撃が拡大するまで待たずに行動を起こしましょう
ランサムウェアが被害をもたらすのに数週間もかかりません。数分かかります。
ウイルス対策ソフトが作動したり、ログにフラグが立てられたりする頃には、攻撃者は既に横方向に移動して機密システムにアクセスし、重要なワークロードを暗号化している可能性があります。
Illumio はあなたをその先へ導きます。
ランサムウェアの拡散を防ぎ、侵害を迅速に封じ込め、ハイブリッド環境を内部から保護するのに役立ちます。
現在のツールでランサムウェアの横方向の移動を阻止できない場合は、アプローチを再考する時期です。
Illumio Insightsを無料でお試しください 検出から封じ込めまでをわずか数分で実行できる方法をご覧ください。

.webp)
.webp)
.webp)
.webp)


