What is Shift Left Security?
What is Shift Left Security?
Shift left security is a development approach that integrates security earlier, or "to the left," in the software development lifecycle (SDLC). Instead of waiting until the testing or deployment stages to identify vulnerabilities, security practices are embedded from the initial stages of coding and design. This proactive strategy helps teams detect and fix issues sooner, reduce risk, and accelerate delivery.
By “shifting left,” organizations can avoid the costly and time-consuming consequences of fixing vulnerabilities after software has already been built or released.
Shift Left vs Traditional Security
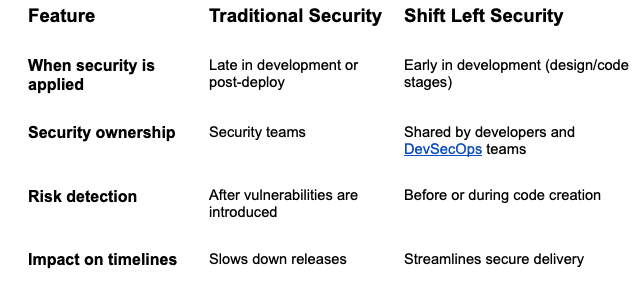
Shift left is foundational to modern DevSecOps practices, aiming to make secure coding part of the developer's everyday workflow.
Why Shift Left Security Matters
- Reduces security debt: Catching vulnerabilities early is far less expensive than fixing them in production.
- Empowers developers: Developers can identify and fix issues directly, without bottlenecks.
- Enables faster releases: Secure code gets delivered more efficiently.
- Improves collaboration: Security, development, and operations work together as a unified team.
- Minimizes attack surfaces: Early testing and validation help prevent exploitable flaws from reaching production.
As cyberattacks grow more sophisticated, integrating security early in the pipeline is a strategic necessity.
Key Components of Shift Left Security
- Secure Coding Practices
- Enforce security standards and guidelines at the code level.
- Educate developers with regular training and security champions.
- Automated Code Scanning
- Use static application security testing (SAST) and linting tools.
- Integrate scans directly into CI pipelines and IDEs.
- Threat Modeling
- Evaluate risks during design and architecture phases.
- Identify potential misuse cases early on.
- Security Unit Testing
- Include test cases that validate secure behavior and edge conditions.
- Run as part of the automated build process.
- Secrets Management
- Detect hardcoded secrets and enforce use of secret vaults.
- IaC and Container Security
- Scan infrastructure-as-code templates and container images for misconfigurations and vulnerabilities.
FAQs
1. Is shift left security only for developers?
No. While developers play a key role, it's a collaborative effort across security, DevOps, and engineering teams to embed security throughout the SDLC.
2. How is shift left different from DevSecOps
DevSecOps is the broader culture and practice of integrating security into DevOps. Shift left is one of its core strategies, emphasizing early security testing.
3. Does shifting left slow down development?
Quite the opposite. By catching issues early, teams avoid delays caused by last-minute security surprises or rework.
How Illumio Supports Shift Left Security
While shift left security focuses on catching vulnerabilities early in development, securing the production environment remains critical. Illumio complements shift left strategies by containing the impact of any undetected issues that make it into production.
Through real-time application visibility and segmentation, Illumio helps organizations prevent lateral movement and reduce the blast radius of exploited vulnerabilities, even if they slip past early security checks.
Conclusion
Shift left security moves security earlier in the development lifecycle, empowering teams to build secure software faster and with fewer risks. By combining proactive testing, developer enablement, and automation, organizations can embed security into the foundation of every application rather than patching it on later.
.png)