Threat Intelligence: A Complete Guide for Organizations
Organizations use different types of threat intelligence to identify potential cybersecurity threats it could face. Read about threat intelligence with our guide.
What is Threat Intelligence?
Threat intelligence refers to the collection, processing, and analysis of data to understand a threat actor’s motives, targets, and attack methods. It transforms raw data into actionable insights, enabling security teams to make informed, data-driven decisions. This proactive approach shifts organizations from a reactive to a proactive stance in defending against cyber threats.
This guide delves into the nuances of threat intelligence, exploring its types, importance, implementation strategies, industry-specific use cases, and future trend
Data vs. Information vs. Intelligence
Understanding the distinctions between data, information, and intelligence is crucial:
- Data: Raw, unprocessed facts without context (e.g., IP addresses, log files).
- Information: Processed data that provides some context (e.g., a list of suspicious IP addresses).
- Intelligence: Analyzed information that offers actionable insights (e.g., understanding that a specific IP address is associated with a known threat actor targeting your industry).
Types of Threat Intelligence
Threat intelligence is categorized into four main types:
- Strategic Threat Intelligence: High-level analysis focusing on broader trends and motivations of threat actors. It aids executives in making informed decisions about security policies and resource allocation. citeturn0search21
- Tactical Threat Intelligence: Details specific techniques, tactics, and procedures (TTPs) used by attackers. It assists security teams in understanding and mitigating specific threats.
- Operational Threat Intelligence: Provides insights into the capabilities, intentions, and opportunities of threat actors. It focuses on understanding the TTPs and behaviors of threat actors — the attack vectors they use, the vulnerabilities they exploit, the assets they target, and other defining characteristics.
- Technical Threat Intelligence: Concentrates on specific indicators of compromise (IoCs) like malicious IP addresses, file hashes, or domain names. It's highly detailed and often used for immediate threat detection.
Threat Intelligence Lifecycle
The process of developing threat intelligence involves several stages:
- Collection: Gathering raw data from various sources, including open-source intelligence (OSINT), dark web forums, internal logs, and industry threat feeds.
- Processing: Organizing and filtering collected data to remove redundancies and irrelevant information.
- Analysis: Interpreting processed data to identify patterns, trends, and actionable insights.
- Dissemination: Sharing the analyzed intelligence with relevant stakeholders in a usable format.
- Feedback: Gathering input on the usefulness of the intelligence to refine future collection and analysis efforts.
Common Sources of Threat Intelligence
- Open-Source Intelligence (OSINT): Publicly available information from websites, news outlets, and reports.
- Dark Web: Data from underground forums and marketplaces where threat actors operate.
- Internal Logs: Data from an organization's own systems, such as firewall logs and intrusion detection systems.
- Shared Industry Feeds: Collaborative platforms where organizations share threat data and indicators.
Why Threat Intelligence is Important
In the modern cybersecurity landscape, threat intelligence plays a pivotal role:
- Enhanced Decision-Making: Provides context to security alerts, enabling prioritization based on potential impact.
- Proactive Threat Detection: Identifies emerging threats before they can exploit vulnerabilities.
- Regulatory Compliance: Assists in meeting compliance requirements by understanding and mitigating relevant threats.
- Incident Response: Offers insights that speed up the response time and effectiveness during security incidents.
Benefits of Threat Intelligence for Organizations
Implementing a robust threat intelligence program offers numerous advantages:
- Improved Threat Detection and Response: Enables faster identification and neutralization of threats.
- Enhanced Security Posture: Provides a comprehensive understanding of the threat landscape, allowing for better defense strategies.
- Reduced Alert Fatigue: Helps in filtering out false positives, allowing security teams to focus on genuine threats.
- Informed Risk Management: Assists in identifying and prioritizing risks based on potential impact.
- Better Communication: Facilitates clearer discussions between technical teams and executives regarding security threats and needs.
- Competitive Advantage: Protects brand reputation and builds customer trust by demonstrating a commitment to security.
How to Implement Threat Intelligence Effectively
1. Establish Objectives
- Align with Business Goals: Ensure that the threat intelligence program supports the organization's overall objectives.
- Define Stakeholders: Identify who will use the intelligence, from technical teams to executive leadership.
2. Choose the Right Tools & Technologies
- Threat Intelligence Platforms (TIPs): Centralize the collection and analysis of threat data.
- SIEM and SOAR Integrations: Integrate intelligence into existing security information and event management systems for automated responses.
- Threat Feeds: Paid vs. Free:
- Free feeds provide baseline insights and community-sourced data.
- Paid feeds often offer curated, enriched, and highly contextualized intelligence. These are typically better suited for enterprise-level protection.
- Free feeds provide baseline insights and community-sourced data.
Pro Tip from Illumio: Don't rely solely on threat feeds. Combine feed data with contextual visibility of your own network to maximize its relevance and effectiveness.
3. Build Internal Capabilities
- Hire or Upskill Threat Analysts: Build a team with the skills to interpret and act on threat intelligence.
- Foster Cross-Department Collaboration: Security teams should regularly communicate with IT, legal, risk, and executive teams.
- Establish Governance Policies: Ensure data privacy, ethical sourcing, and legal compliance when gathering intelligence.
4. Data Collection and Management
- Curate High-Quality Data: Prioritize data relevancy over volume. Collect only what aligns with your risk profile.
- Ensure Legal & Ethical Sourcing: Avoid legal complications by sticking to vetted sources and complying with regulations like GDPR.
5. Analysis and Action
- Correlate with Internal Telemetry: Overlay external intel with your network’s data for deep, contextual insights.
- Create Actionable Reports: Intelligence should result in clear, easy-to-understand guidance for stakeholders.
- Prioritize and Coordinate Responses: Develop a playbook for responding to various threat types based on risk severity.
Threat Intelligence Use Cases by Industry
1. Financial Services
- Detect and block phishing campaigns targeting online banking portals.
- Prevent insider threats by monitoring anomalous employee behaviors.
- Correlate threat intel with fraud detection systems for real-time alerts.
2. Healthcare
- Identify ransomware threats targeting electronic health records (EHRs).
- Monitor the dark web for stolen patient data.
- Comply with HIPAA through proactive threat modeling.
3. Retail & eCommerce
- Monitor for compromised customer credit card data.
- Track supply chain threats, including vulnerable third-party vendors.
- Defend against brand impersonation attacks on social media and search engines.
4. Government & Defense
- Track nation-state actors targeting infrastructure and defense assets.
- Share intelligence with inter-agency partners and Information Sharing and Analysis Centers (ISACs).
- Monitor geopolitical threats that could impact national cybersecurity posture.
5. Technology & SaaS
- Identify leaked API keys or login credentials from public repositories.
- Preempt DDoS attacks through early alerts and infrastructure hardening.
- Monitor open-source software dependencies for zero-day vulnerabilities.
Regardless of your industry, segmentation through tools like Illumio helps isolate threats and reduce lateral movement — essential when intelligence reveals active threats inside your network.
Threat Intelligence Platforms and Vendors
Several cyber threat intelligence platforms help automate, contextualize, and operationalize threat data. Top vendors include:
- Recorded Future – Strong in real-time threat analysis and automation.
- ThreatConnect – Great for workflow and orchestration.
- Anomali – Known for its breadth of integrations and robust threat database.
- Mandiant – Offers elite threat actor attribution and post-breach insights.
Key Features to Evaluate:
- Integrations: Must integrate with your SIEM, SOAR, firewalls, and ticketing systems.
- Automation: Ability to auto-ingest and act on threat data.
- Customization: Tailor dashboards, alerts, and reports to match internal workflows.
- Community Sharing: Participate in threat sharing networks like FS-ISAC or InfraGard.
How to Operationalize Threat Intelligence
Moving from theory to practice requires embedding threat intelligence into daily operations.
- Integrate into SIEM & SOAR Tools: Enrich alerts and automate containment actions.
- Develop Threat Intel Dashboards: Visualize threat trends and incidents for all stakeholders.
- Internal Sharing: Disseminate tailored intel across IT, legal, compliance, and C-suite.
- External Sharing: Participate in industry intelligence-sharing programs to build a collective defense.
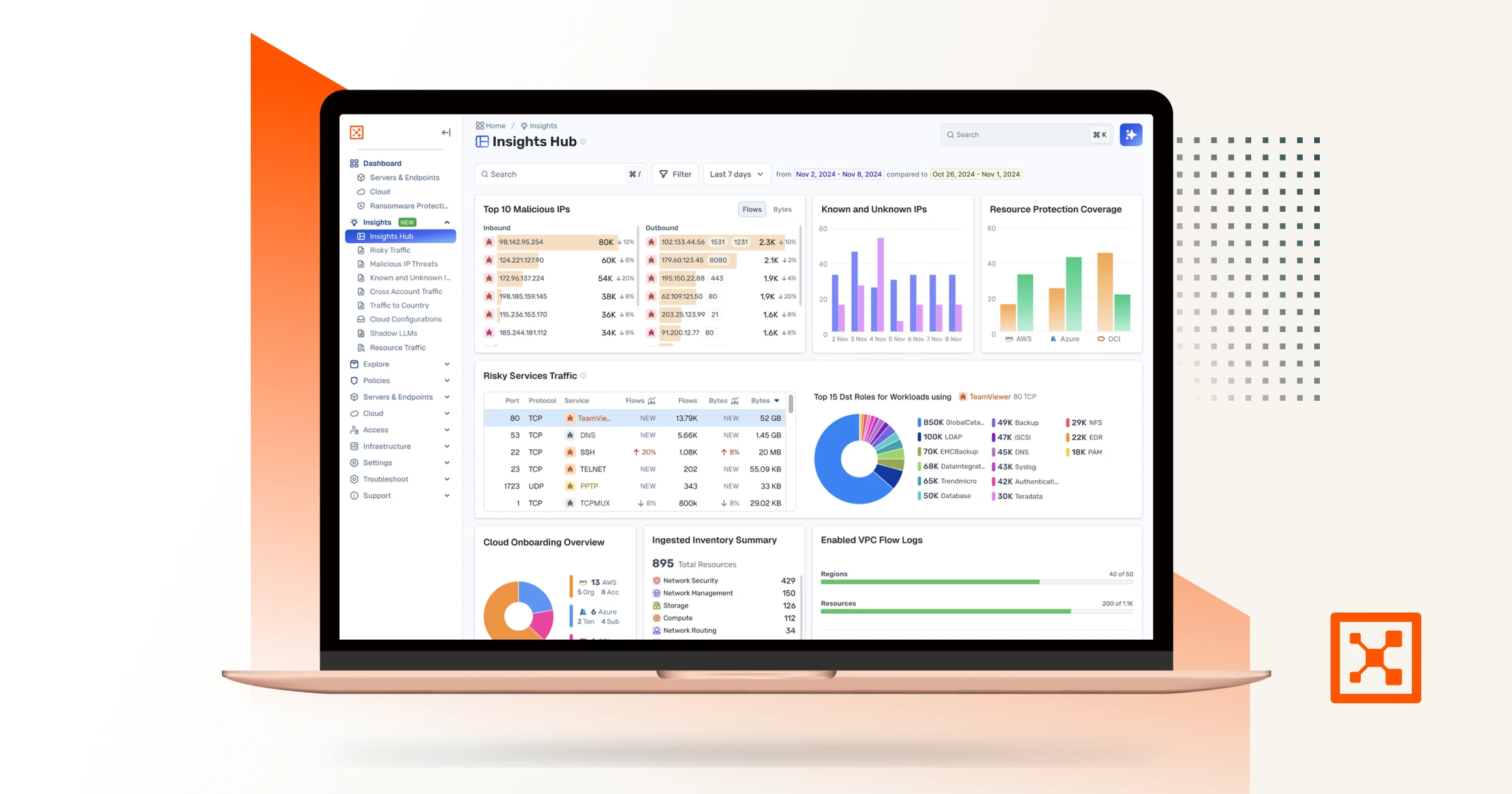
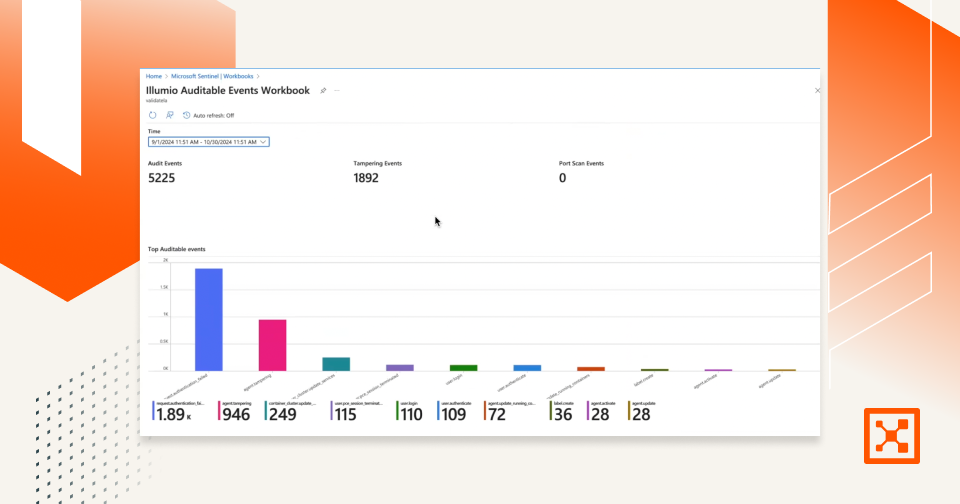
Pro Tip from Illumio: Operational threat intelligence becomes exponentially more powerful when paired with network visibility. Tools like Illumio allow your team to instantly visualize application flows and isolate affected systems — crucial for fast, confident responses.
Metrics and KPIs to Measure Effectiveness
You can’t improve what you don’t measure. Track these metrics to assess your threat intelligence program:
- Alerts Enriched with Threat Intel: The percentage of security alerts contextualized with external intelligence.
- Time-to-Detection (TTD) / Time-to-Response (TTR): How quickly your team can identify and contain threats.
- Reduction in False Positives: Improved alert quality due to contextual threat data.
- Relevance Score: How often threat intel matches your environment’s risk profile.
- ROI: Estimate the financial savings from avoided breaches or faster incident resolution.
Common Challenges and How to Overcome Them
- Information Overload: Focus on curated, relevant data rather than drowning in unfiltered feeds.
- Shortage of Skilled Analysts: Upskill internal teams and leverage managed threat intelligence services.
- Data Source Integration: Use platforms that support APIs and normalized threat data formats.
- Keeping Data Fresh: Use automation to pull updated feeds daily.
- Breaking Down Silos: Ensure intelligence is visible across departments, not just in the SOC.
Future Trends in Threat Intelligence
- AI & Machine Learning: Improve threat prediction and anomaly detection at scale.
- Threat Intelligence Sharing Ecosystems: Increased cooperation among industries and governments.
- Behavioral Intelligence: Focus on patterns of human behavior to detect insider threats
- Zero Trust Architectures: Enhanced microsegmentation and least-privilege access reduce the impact of breaches.
- Cloud-Native Intelligence: Adapting intel feeds to dynamic, containerized, and serverless environments.
Illumio Insight: As more organizations adopt Zero Trust, operational threat intelligence must evolve to monitor workloads in motion — not just static endpoints.
Real-World Case Studies
Case Study 1: Financial Institution Thwarts Phishing Campaign
A regional bank used a cyber threat intelligence platform to detect a phishing domain mimicking its login portal. Thanks to automation, the domain was blocked across its infrastructure within minutes — saving customer data and brand reputation.
Case Study 2: Healthcare Organization Prevents Ransomware
A hospital system monitored dark web chatter and detected a ransomware gang planning to exploit a vulnerable imaging server. Preemptive patching and segmentation helped avoid disruption of patient services.
Case Study 3: Retailer Stops Brand Impersonation
A major eCommerce player discovered fake social media accounts posing as customer support. Cyber threat intelligence flagged the impersonators, who were taken down before launching a malicious campaign.
Threat Intelligence Frequently Asked Questions (FAQs)
What are the best sources of threat intelligence?
A mix of OSINT, dark web monitoring, internal telemetry, and premium threat feeds is ideal.
How much does threat intelligence typically cost?
It varies — from free tools to six-figure enterprise platforms, depending on your scale and needs.
Can small businesses benefit from threat intelligence?
Absolutely. Even basic monitoring of phishing or malware trends can reduce risk significantly.
How is threat intelligence different from a threat feed?
Threat feeds provide raw data. Threat intelligence analyzes and contextualizes that data for action.
Do I need a dedicated threat intelligence team?
Not necessarily. Small teams can leverage managed services or automation to stay effective.
How does Zero Trust Segmentation enhance threat intel?
It contains threats, limits lateral movement, and offers clear application context to your threat data.
What is strategic intelligence in cybersecurity?
It provides high-level insight into global threat trends and motivations, useful for leadership decisions.
What are indicators of compromise (IoCs)?
IoCs are forensic artifacts like IPs, hashes, or URLs that signal malicious activity.
How can threat intelligence support compliance?
It helps meet requirements for continuous monitoring and documented response plans under frameworks like NIST, HIPAA, and PCI-DSS.
Is threat intelligence useful after an attack?
Yes. Post-incident analysis with threat intel can reveal how the attack occurred and prevent reoccurrence.
Conclusion
Threat intelligence is no longer a “nice-to-have” for enterprises — it’s essential. By transforming raw data into actionable, contextual insight, organizations can proactively defend against today’s sophisticated threats.
With the right mix of tools, internal expertise, and platforms like Illumio, threat intelligence evolves from a static function to a living, breathing engine of security.
Start small. Measure everything. Scale smartly. That’s how organizations build resilience in the face of a volatile threat landscape.
.png)

.webp)
%20(1).webp)
.webp)