Resource Center
Insights, news, and updates from the leader in breach containment

Demos








Cyber Resilience
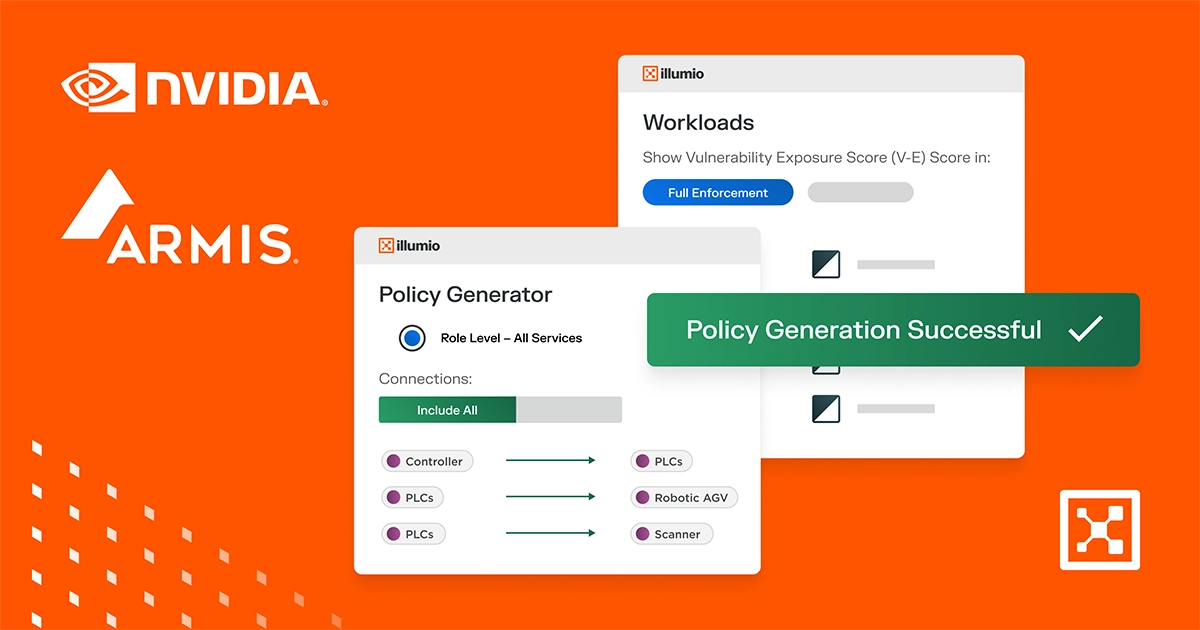
Illumio Segmentation Demo
Illumio Segmentation provides real-time visibility and microsegmentation to contain breaches.
Read more








Illumio for Containers
Secure your containerized applications in OpenShift using visibility and microsegmentation from Illumio.
Read more

Experience Illumio Insights today
See how AI-powered observability helps you detect, understand, and contain threats faster.