How Zero Trust Keeps Federal Cybersecurity Strong During Uncertainty
.webp)
When I sat down for the Federal Tech Podcast recently, it was during yet another U.S. government shutdown — the longest one in our nation’s history, in fact.
The timing wasn’t lost on me. Agencies across Washington were short-staffed, operations slowed, and a lot of critical work was paused.
But there’s one thing that doesn’t pause no matter what state the federal government is in: cyber threats.
Our adversaries don’t take time off during a shutdown. They read the same headlines we do. They know when agencies are distracted, understaffed, and stretched thin. And they’re ready to exploit it.
I’ve been in government and federal cybersecurity for more than 35 years, and I’ve seen this pattern repeat itself over and over. Every time the federal workforce faces uncertainty, cyber adversaries take advantage.
The question isn’t whether an attack will happen during these periods but whether your agency is prepared to contain it.
In my recent conversation with John Gilroy on the Federal Tech Podcast episode, How Zero Trust Automation Helps Federal Agencies Do More with Less, I shared why Zero Trust is the key to sustaining resilience when resources are limited and uncertainty is inevitable.
When uncertainty mounts, Zero Trust steps up
A federal shutdown like the one we just experienced is a stress test for cybersecurity. You suddenly have fewer people in the office, fewer eyes on screens, and more tasks piling up for those still working.
That kind of instability is a perfect recipe for risk.
Zero Trust helps reduce that risk by doing what people can’t always do: automating verification and enforcing policy in real time.
Instead of depending on every security decision to come from someone sitting behind a keyboard, a Zero Trust architecture constantly checks who’s accessing what, when, and how. It automatically enforces the rules you’ve set with no exceptions, no shortcuts, no manual workarounds.
It’s the digital equivalent of a 24/7 security guard who never gets tired, distracted, or furloughed.
That automation gives your human teams space to focus on the high-value problems only they can solve. And in a world where resource and staffing challenges are inevitable, that’s one of the smartest investments a federal agency can make.
Building resilience into your agency’s security processes
There’s another reason Zero Trust matters when the unexpected happens. It assumes failure will occur.
I’ve said it before that defenders have to be right all the time, but adversaries only have to be right once. You can’t plan to be perfect, but you can plan to be resilient.
A strong Zero Trust strategy doesn’t just try to prevent breaches. It builds breach containment directly into your architecture so that when, not if, attackers gets in, the damage stops fast.
That’s where segmentation comes in. At Illumio, we use segmentation to create what I call “rings of defense.” Instead of relying on one big wall around your network, you build many smaller walls inside it.
If an attacker breaches one ring, they can’t move freely across your systems. Each application, workload, or server has its own protective boundary. The more boundaries you build, the harder it is for attackers to move, and the easier it is for defenders to spot them.
In short, Zero Trust makes your environment resilient by design, not dependent on human reaction time.
From policy to proof: how Zero Trust strengthens compliance
If you’ve ever gone through a federal audit, you know auditors love data. They want proof that what you say you’re doing is actually happening.
That’s another advantage of Zero Trust.
Too often, agencies have great written security policies that don’t translate into practice. The controls exist on paper, but not at the “keyboard and mouse” level. A Zero Trust environment closes that gap.
When you implement continuous verification, automated access control, and microsegmentation, you generate real-time evidence that your policies are enforced, not just documented.
That kind of visibility doesn’t just make you more secure. It makes audits faster, compliance reporting easier, and leadership more confident that your policies aren’t just shelfware.
Taming complexity with complete visibility
Federal IT environments are some of the most complex in the world.
You’ve got decades-old legacy systems living alongside cloud-native apps, endpoint devices, and now AI models. The attack surface grows by the day.
Complexity is the enemy of security. And without fine-grained visibility into that complexity, you can’t protect what you can’t see.
That’s why complete visibility is such a crucial first step toward Zero Trust. You need to see how applications and systems interact across on-premises, hybrid, and multi-cloud environments based on real network data, not assumptions.
Once you can see those connections, you can start to enforce policies that make sense: allow only what’s necessary, block everything else, and dynamically adjust as systems evolve.
That’s operational Zero Trust in action.
Why AI is both a risk and an opportunity
No federal cybersecurity conversation today is complete without talking about AI.
AI brings a double-edged challenge:
- On one hand, AI can help federal defenders surface threats faster. At Illumio, we’re using AI to analyze traffic patterns, identify risky connections, and uncover “shadow” AI activity, such as large language models (LLMs) running without approval or oversight.
- On the other hand, AI itself has to be protected. It’s just another critical application, one that could expose sensitive data if not properly contained.
That’s why I advise agencies to ringfence their AI models. By applying AI-powered segmentation, you can limit what data your AI systems can access, ensure they only analyze approved datasets, and prevent them from becoming an unintentional data leak.
Shadow IT has always been a problem. Now we have shadow LLMs, and they’re just as risky. Zero Trust and segmentation are how you keep both in check.
Make sure you’re using the CISA Zero Trust Maturity Model correctly
Many agencies measure their progress using the CISA Zero Trust Maturity Model. It’s a helpful framework, but it’s easy to misunderstand.
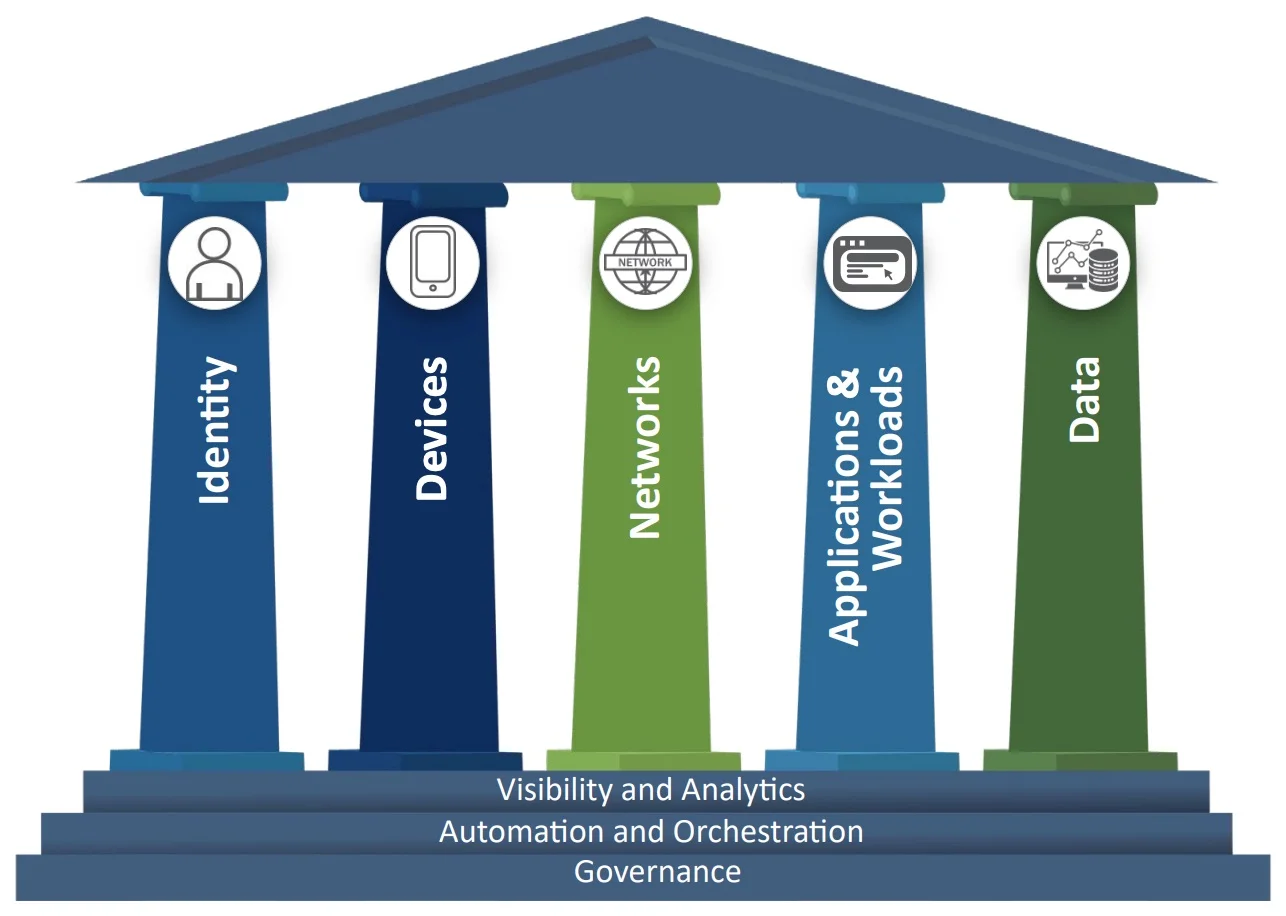
I’ve seen too many organizations approach it like a checklist: “Let’s finish identity, then move to devices, then networks.”
That’s not how Zero Trust works.
You can’t think of it as sequential checklist where you can mark off pillar one, then pillar two, and so on. You have to work across all pillars simultaneously.
Think back to your school report card. Your final grade wasn’t about getting 100% in one class and a zero in another. It was the average of everything. Your Zero Trust journey is the same.
Focus on balance and progress across all areas, not perfection in one. The agencies that understand that are the ones that build true resilience, not just compliance.
The federal government’s urgency to do more with less
If there’s one thing decades in federal cybersecurity have taught me, it’s that uncertainty isn’t going away. You can be certain that budgets will tighten, staff will fluctuate, and threats will evolve.
But Zero Trust helps you do more with less — not by cutting corners but by making your network architecture smarter. Zero Trust ensures you can:
- Automate manual processes so your people can focus on more critical work
- Build containment so a single breach doesn’t become a crisis
- Deliver visibility so you can prove your defenses are working to auditors
- Maintain security and continuity even when the world around you isn’t stable
Federal agencies don’t have the luxury of waiting for perfect conditions. The adversaries aren’t waiting for your next budget cycle or hiring round.
Zero Trust gives you the control, confidence, and resilience to keep protecting critical data no matter what’s happening in Washington.
Ready to turn Zero Trust from strategy to action? Experience Illumio Segmentation free to see how simple it is to contain breaches, automate enforcement, and prove compliance — all from one platform.
.webp)
.webp)





