What is CI/CD Security?
What is CI/CD Security?
CI/CD security refers to the practices, tools, and policies that safeguard the Continuous Integration and Continuous Deployment (CI/CD) pipeline. As organizations automate software delivery, these pipelines become a key target for attackers. CI/CD security ensures that code, infrastructure, secrets, and build environments remain protected throughout every stage of the DevOps lifecycle.
CI/CD vs. Traditional Software Delivery
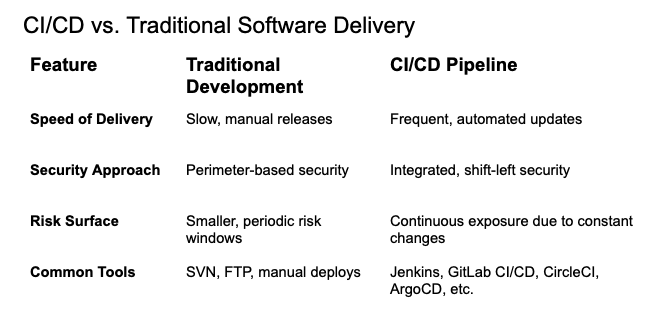
Unlike traditional workflows, CI/CD pipelines must be continuously secured as they automatically build, test, and deploy applications multiple times a day.
Why CI/CD Security Matters
- Attackers target pipelines: They often exploit misconfigured tools, leaked credentials, or poisoned dependencies.
- Privilege misuse is common: Build systems often have broad permissions, making them prime lateral movement targets.
- Secrets and tokens are vulnerable: Hardcoded credentials in code or environment files can be exfiltrated.
- Supply chain risk is growing: CI/CD pipelines integrate open-source packages, registries, and third-party services.
With CI/CD, the pace of delivery is an asset, but without security controls, it also becomes a liability.
Core Pillars of CI/CD Security
- Code Security (Shift Left)
- Static and dynamic code analysis (SAST/DAST)
- Pre-commit hooks and branch protections
- Secret scanning and linting
- Build Pipeline Security
- Harden build servers and runners (Jenkins agents, GitHub Actions, etc.)
- Run builds in isolated environments
- Validate and sign all artifacts
- Dependency and Supply Chain Protection
- Use verified and pinned dependencies
- Monitor for vulnerable packages (via SCA tools)
- Scan container images pre-deployment
- Infrastructure as Code (IaC) Security
- Scan Terraform, CloudFormation, or Kubernetes manifests
- Enforce policies before deployment (e.g., using OPA or Sentinel)
- Secrets and Credential Management
- Use vaults and dynamic secrets (e.g., HashiCorp Vault, AWS Secrets Manager)
- Avoid hardcoding credentials into code or CI configs
- Access and Auditing
- Enforce least-privilege access to CI/CD tools
- Log and monitor all pipeline activity
- Apply role-based access controls (RBAC)
Industry Standards & Best Practices
- OWASP Top 10 for CI/CD: Highlights key risks like insecure code, exposed secrets, and dependency misuse.
- SLSA (Supply-chain Levels for Software Artifacts): A Google-backed framework for securing build pipelines.
- NIST 800‑204C: Security strategies for microservices-based CI/CD pipelines.
- DevSecOps principles: Embeds security checks into every stage of development and delivery.
Common CI/CD Security Threats
- Poisoned artifacts: Malicious packages or containers injected into the pipeline.
- Credential theft: Leaked or hardcoded secrets used to access cloud resources.
- Pipeline takeover: Attackers hijack build agents or CI tools to deploy malware.
- Environment drift: Unsecured, misaligned environments between staging and production.
- Shadow CI/CD: Unofficial or rogue pipelines that bypass security policies.
How to Secure Your CI/CD Pipeline
- Integrate security early: Make it part of every merge, build, and deploy.
- Automate scanning: Test code, containers, and IaC continuously.
- Manage secrets properly: Rotate them regularly and store them in secure vaults.
- Monitor access: Track changes, deployments, and sensitive actions.
- Use secure tools: Keep your CI tools updated and hardened.
- Sign and verify artifacts: Ensure build integrity before shipping to production.
FAQs
1. How is CI/CD security different from traditional AppSec?
Traditional AppSec focuses on the application itself. CI/CD security encompasses the entire delivery pipeline, from code commit to deployment.
2. Do CI/CD tools come with built-in security?
Most include basic access control and logs, but it’s your responsibility to layer in proper secrets management, scanning, and access controls.
3. What’s the role of DevSecOps here?
DevSecOps ensures that security becomes a shared responsibility — automated, continuous, and built into every CI/CD stage.
How Illumio Helps Secure Your CI/CD Pipeline
Illumio brings powerful segmentation and visibility capabilities to CI/CD environments by containing the lateral movement risks that often arise during automated builds, deployments, and integrations. As organizations adopt DevOps at scale, their pipelines become increasingly interconnected and vulnerable to compromise.
Illumio Segmentation ensures that if a CI/CD system is breached, whether through a compromised build server, developer endpoint, or exposed secret, the attacker’s ability to move laterally across environments is blocked.
Final Thoughts
CI/CD security ensures that speed doesn’t come at the cost of safety. By embedding security into the heart of the software delivery pipeline — from initial code to final deployment — teams can move fast without opening the door to breaches, lateral movement, or supply chain compromise.
.png)