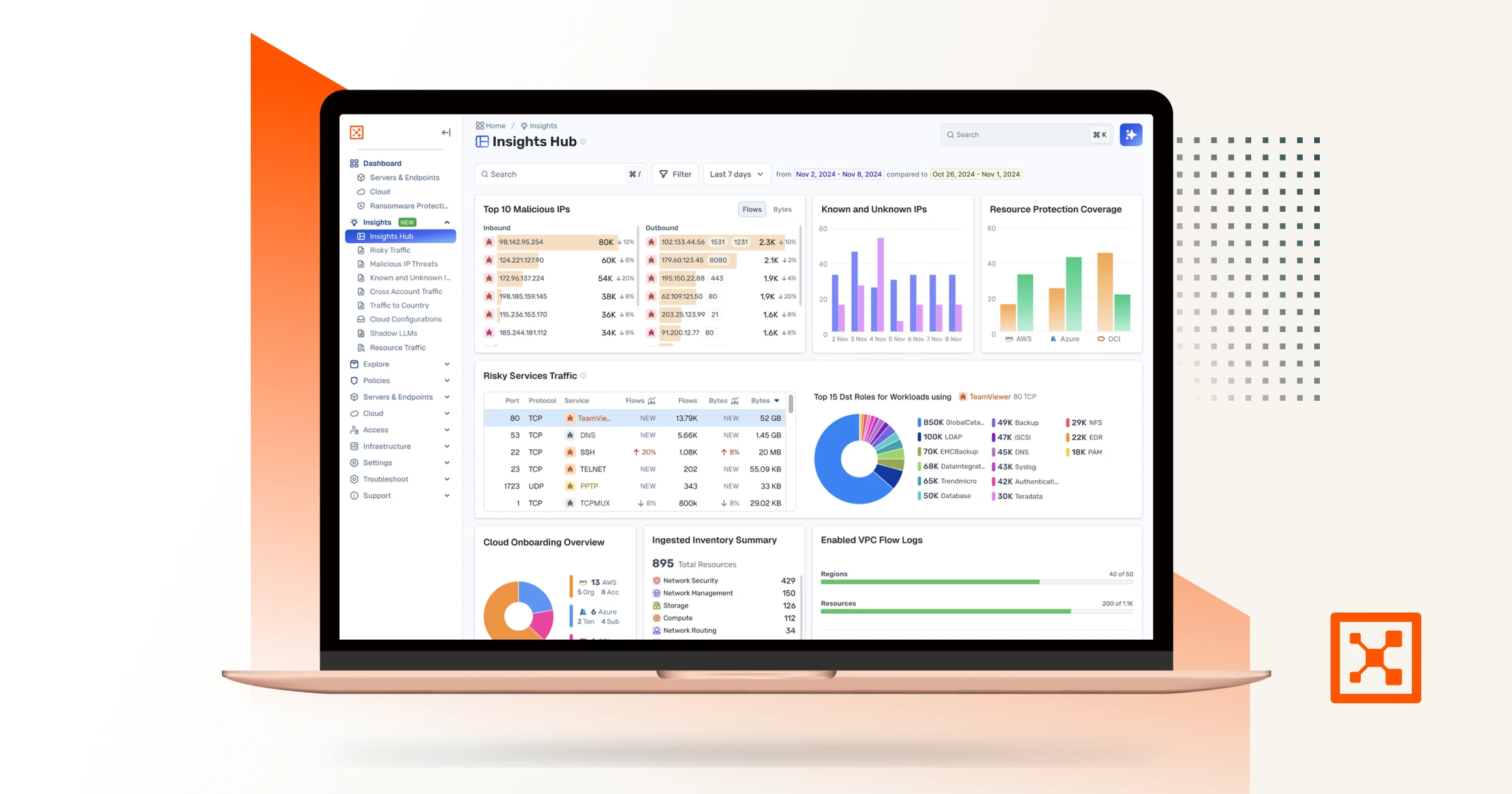
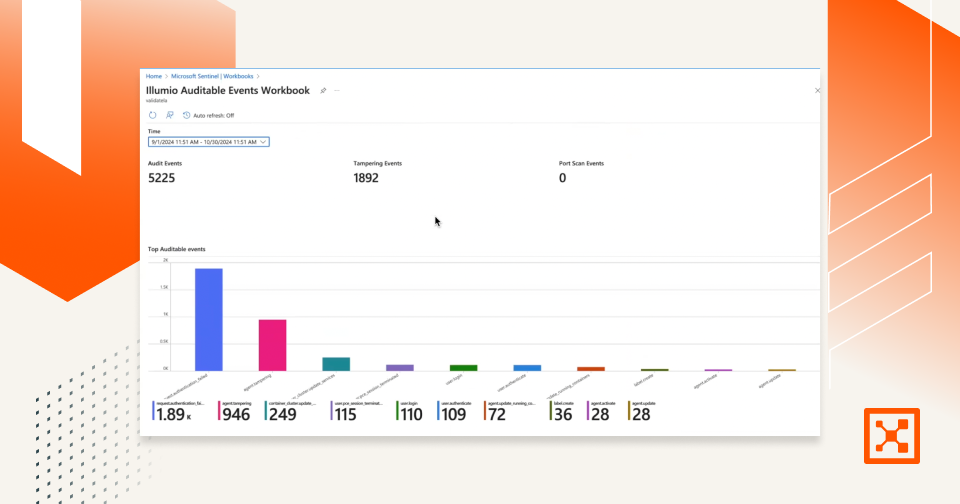
DevSecOps: A Complete Guide for Organizations
Cyber threats are evolving at a rapid pace and organizations need more technical, modern approaches in every phase of their development cycle. Read our complete breakdown of this approach and enable your team to deliver secure software faster and more efficiently.
What is DevSecOps?
DevSecOps stands for Development, Security, and Operations and is a cultural and technical approach that integrates security practices within the DevOps process. In an era where software development is the backbone of innovation, integrating security into every phase of the development lifecycle is no longer optional — it's imperative. DevSecOps, an evolution of DevOps, embodies this integration, ensuring that security is a shared responsibility across development, security, and operations teams.
The stakes are high: according to IBM's 2024 Cost of a Data Breach Report, the average cost of a data breach reached $4.45 million, underscoring the financial implications of security lapses. Moreover, with the rapid adoption of Continuous Integration/Continuous Deployment (CI/CD) pipelines, organizations must ensure that security keeps pace with development speed.
This comprehensive guide delves into the essence of DevSecOps, its significance, benefits, implementation strategies, real-world applications, challenges, best practices, and frequently asked questions.
Evolution from DevOps to DevSecOps
DevOps revolutionized software development by fostering collaboration between development and operations teams, emphasizing automation, and enabling rapid delivery. However, security was often an afterthought, leading to vulnerabilities and breaches.
DevSecOps emerged to address this gap, integrating security into the DevOps workflow. By adopting a "shift-left" approach, security considerations are introduced early in the development process, allowing for the identification and mitigation of vulnerabilities before they escalate.
Why DevSecOps Matters
Rising Threat Landscape
Cyber threats are evolving rapidly, with attackers exploiting vulnerabilities in software supply chains, open-source components, and CI/CD pipelines. High-profile incidents like the Log4j vulnerability have highlighted the need for proactive security measures throughout the SDLC.
Legacy Security vs. Agile Development
Traditional security models, characterized by siloed teams and manual processes, are ill-suited for the agile, fast-paced world of modern software development. DevSecOps bridges this gap by embedding security into agile workflows, ensuring that security keeps pace with development speed.
Cost of Late-Stage Security Fixes
Addressing security issues late in the development cycle is costly and time-consuming. The earlier a vulnerability is detected, the cheaper and easier it is to fix. DevSecOps enables early detection, reducing remediation costs and minimizing the risk of breaches.
Compliance Pressure
Regulatory frameworks like GDPR, HIPAA, SOC 2, and PCI-DSS mandate stringent security controls. DevSecOps facilitates compliance by integrating security checks and audits into the development process, ensuring continuous adherence to regulatory requirements.
Key Benefits of DevSecOps for Organizations
- Improved Security Posture: Continuous security integration reduces vulnerabilities and enhances overall security.
- Faster Time to Market: Automated security testing accelerates development cycles without compromising security.
- Better Collaboration Between Teams: Shared responsibility fosters collaboration among development, security, and operations teams.
- Early Vulnerability Detection and Remediation: Identifying issues early reduces remediation costs and prevents breaches.
- Cost Savings Over the Software Lifecycle: Proactive security measures reduce the financial impact of vulnerabilities and breaches.
- Improved Compliance and Governance: Integrated security controls facilitate continuous compliance with regulatory standards.
Core Principles and Practices of DevSecOps
Shift Left
Integrate security early in the development process to identify and address vulnerabilities before they escalate.
Security Automation in CI/CD
Automate security testing within CI/CD pipelines to ensure continuous security validation without hindering development speed.
Infrastructure as Code (IaC) Security
Implement security controls in IaC to prevent misconfigurations and enforce compliance.
Continuous Threat Monitoring and Response
Monitor applications and infrastructure continuously to detect and respond to threats in real-time.
Policy as Code and Governance
Define and enforce security policies programmatically to ensure consistent compliance across environments.
Secure Coding Practices and Developer Enablement
Educate developers on secure coding practices and provide tools to identify and remediate vulnerabilities during development.
How to Implement DevSecOps in Your Organization
Step-by-Step Roadmap
- Conduct a DevSecOps Readiness Assessment: Evaluate current processes, tools, and culture to identify gaps.
- Build a Cross-Functional Team: Assemble a team comprising developers, security professionals, and operations personnel.
- Identify High-Priority Workflows: Focus on critical applications and services to pilot DevSecOps practices.
- Choose and Integrate Tools: Select tools that support security automation, IaC, and policy enforcement.
- Set KPIs and Success Metrics: Define measurable goals to track progress and effectiveness.
- Adopt the Security Champions Model: Empower developers to take ownership of security within their teams.
- Pilot and Scale: Start with a pilot project, gather feedback, and gradually scale DevSecOps practices across the organization.
DevSecOps in Practice: Real-World Use Cases
Implementing DevSecOps isn’t just theory — it’s actively transforming how organizations operate across industries.
Financial Services
Financial institutions face constant threats from cybercriminals and intense regulatory scrutiny.
DevSecOps in Action:
- Continuous scanning of source code and containers for vulnerabilities
- Automated compliance checks (e.g., SOX, PCI-DSS)
- Microsegmentation to isolate critical workloads
Outcome: Reduced mean time to detect (MTTD) and respond (MTTR) to threats, enabling faster audits and lower compliance risks.
Healthcare
With sensitive patient data at stake, healthcare apps must adhere to HIPAA while delivering modern, user-friendly digital services.
DevSecOps in Action:
- Embed static application security testing (SAST) and dynamic analysis (DAST) in CI/CD
- Use of Infrastructure as Code (IaC) tools secured with policy-as-code guardrails
- Segmentation to protect Electronic Health Records (EHRs)
Outcome: Enhanced data security and faster release cycles for patient-facing applications.
eCommerce
Security is paramount for protecting customer credentials, financial data, and ensuring business continuity.
DevSecOps in Action:
- API security testing integrated into release pipelines
- Runtime application self-protection (RASP)
- Third-party software component monitoring
Outcome: Minimized risk of cart abandonment due to breaches and more secure digital shopping experiences.
SaaS & Cloud Providers
Multi-tenant architectures demand airtight boundaries and consistent policy enforcement.
DevSecOps in Action:
- Continuous integration of cloud security posture management (CSPM)
- Microsegmentation using tools like Illumio Segmentation to control east-west traffic
- Zero Trust enforcement across services
Outcome: Increased customer trust and scalable, secure service delivery.
Common DevSecOps Challenges and How to Overcome Them
Transitioning to DevSecOps isn't without hurdles. Here’s how to tackle the most common roadblocks:
1. Organizational Silos and Resistance to Change
- Solution: Build a unified team culture. Use cross-functional squads and shared KPIs.
2. Tool Fatigue and Integration Complexity
- Solution: Consolidate tools into fewer, integrated platforms that support DevSecOps natively (e.g., GitHub Advanced Security, Jenkins plugins, etc.).
3. Developer Pushback and Alert Fatigue
- Solution: Prioritize actionable alerts. Integrate alerts directly into developer IDEs for context-aware remediation.
4. Managing False Positives
- Solution: Continuously tune tools and automate triage processes. Apply risk-based prioritization.
5. Skills Gaps in Secure Coding
- Solution: Offer regular secure coding workshops, implement a Security Champions program, and invest in platforms like Secure Code Warrior.
DevSecOps Best Practices for Long-Term Success
To ensure DevSecOps isn't just a trend but a sustained cultural shift, apply these long-term practices:
- Start Small, Scale Fast: Pilot DevSecOps in one team or project and use learnings to scale.
- Secure Developer Onboarding: Train new developers in security tools and practices from day one.
- Policy-as-Code: Automate enforcement of security policies with tools like Open Policy Agent (OPA).
- Continuous Feedback Loops: Use retrospectives, blameless postmortems, and automated reports to fuel improvement.
- Regular Toolchain Evaluation: DevSecOps tools evolve — review and update your stack every quarter.
DevSecOps at Illumio: A Strategic Business Enabler
At Illumio, we don’t just talk about security — we live it. By leveraging DevSecOps internally and in our product suite, we enable organizations to:
- Embrace Zero Trust: With microsegmentation and visibility, Illumio’s solutions prevent lateral movement even after initial compromise.
- Secure Hybrid Infrastructure: From containers to VMs, Illumio provides consistent policy enforcement across platforms.
- Enhance Resilience: With proactive segmentation and dynamic policy updates, even breaches like Log4j have limited blast radius.
DevSecOps Frequently Asked Questions (FAQs)
1. What’s the difference between DevSecOps and traditional AppSec?
Traditional AppSec is often tacked onto the end of development. DevSecOps weaves security throughout the SDLC, automating testing and empowering developers.
2. How long does it take to implement DevSecOps?
It depends on your starting point. A basic implementation in one team can take 3–6 months, while full enterprise adoption might take a year or more.
3. Do I need to rebuild my CI/CD pipeline to adopt DevSecOps?
Not necessarily. Most DevSecOps tools integrate with popular pipelines like Jenkins, GitLab, GitHub Actions, and Azure DevOps.
4. Can small teams implement DevSecOps effectively?
Absolutely. With the right tools and cultural mindset, small teams can be highly agile and secure by design.
5. How do you handle open-source security in DevSecOps?
Use Software Composition Analysis (SCA) tools to scan dependencies and get notified of vulnerable packages.
6. Is DevSecOps only for cloud-native environments?
No. DevSecOps benefits on-premises, hybrid, and cloud-native environments by bringing automation and collaboration to any SDLC.
7. What are Security Champions and why are they important?
Security Champions are developers with security training who advocate for best practices within teams. They bridge gaps and accelerate adoption.
8. How can I measure the success of DevSecOps?
Track metrics like vulnerability remediation time, number of security incidents, code coverage in security tests, and deployment frequency.
9. Do security tools slow down development?
Not when configured properly. In fact, automation reduces bottlenecks and increases developer confidence in releases.
10. What role does microsegmentation play in DevSecOps?
Microsegmentation, like Illumio offers, limits the lateral movement of attackers, enhancing runtime security and enforcing least privilege.
Conclusion
DevSecOps isn’t a one-size-fits-all framework — it’s a cultural and technical transformation. It brings security to the forefront of innovation, allowing teams to deliver fast, reliable, and resilient software.
.png)

.webp)
%20(1).webp)
.webp)