Armis
Protect IT and OT networks from breaches

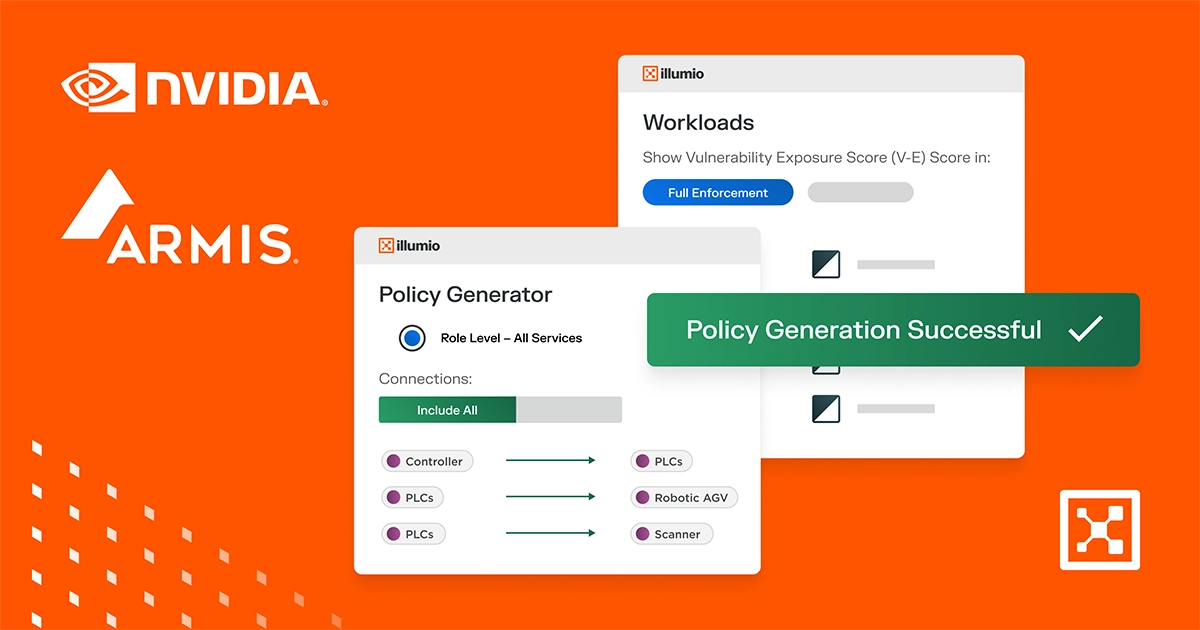
Gain unprecedented visibility and protection of IoT/OT environments
Integrate Armis’ best-in-class asset intelligence with Illumio’s leading Breach Containment Platform to deliver complete visibility and protection across the most complex IoT/OT environments.

Unprecedented Visibility
Discover, categorize, and map IoT, OT, and IT systems, communications, and risks in a single view, regardless of location (clouds, data centers, retail stores, bank branches).

Limit Exposure
Identify and ring-fence high-value systems to protect them from the spread of breaches. Zero Trust Security means only verified communications are allowed, preventing malware movement.

Effective Threat Response
Build an automated incident response system to apply extra restrictions should an attack be detected.
Already an Illumio partner?
Partner login
.webp)