.png)

6 Steps to Implementing a Zero Trust Model
Learn key best practices to building stronger Zero Trust security to protect against ransomware and other cyberattacks.
An "all or nothing" approach to Zero Trust is a tall task. What if you took a more incremental, agile approach that allows your organization to make realistic steps toward achieving Zero Trust?
Download this ebook to learn:
- The six steps to pragmatically build your Zero Trust security program using a repeatable process.
- How security controls like microsegmentation can help tackle focus areas such as workload protection.
- What capabilities are essential to implement and maintain least-privilege access efficiently.
Highlights
Key benefits
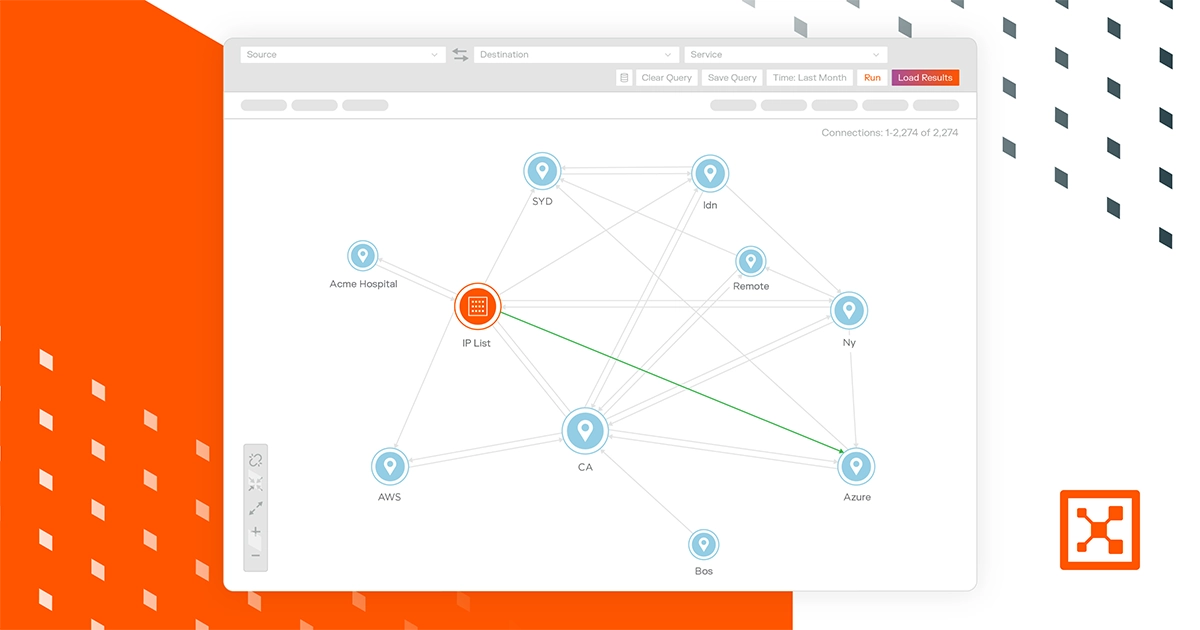
Asset preview






Assume Breach.
Minimize Impact.
Increase Resilience.
Ready to learn more about Zero Trust Segmentation?