Compliance
Stay compliant with Illumio’s cybersecurity solutions, simplifying regulatory adherence and ensuring protection against breaches.
.svg)
Related blog posts
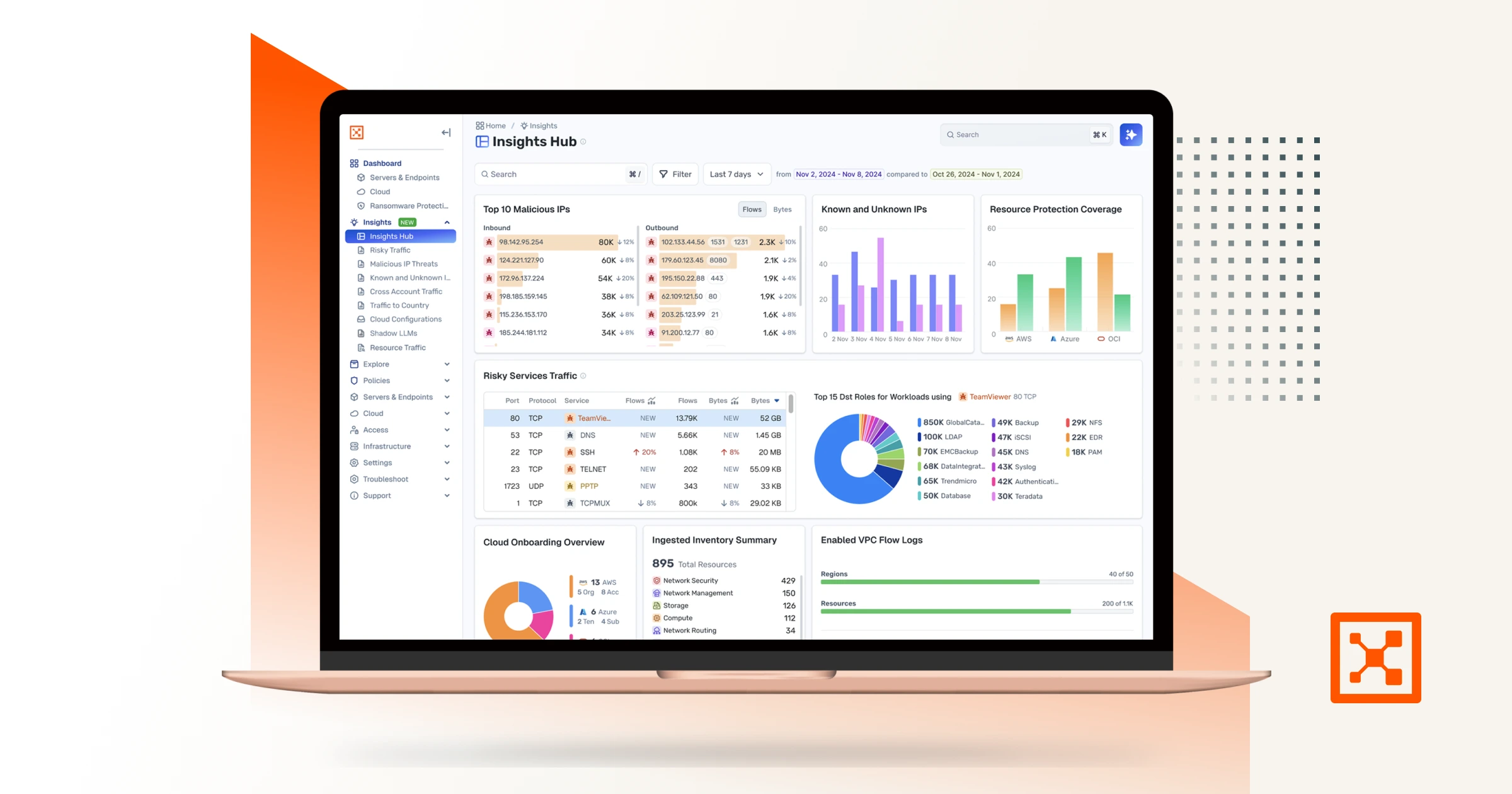
How Cloud Detection and Response with Illumio Insights Helps You Stay Compliant
Learn how cloud detection and response with Illumio Insights helps meet GDPR, HIPAA, PCI DSS, and DORA compliance with better visibility and faster response.
%20(1).webp)
Go Beyond the Audit: Achieve Continuous Compliance with Illumio + ServiceNow
Learn how risk-based microsegmentation with Illumio and ServiceNow strengthens cyber resilience and enables real-time, continuous compliance.
.webp)
Two Breaches, One Bank: Lessons from The ICBC Cyber Crisis
Discover critical lessons from the ICBC cyber crisis, where two major breaches — ransomware in the U.S. and a data theft in London — revealed systemic vulnerabilities in global banking.

How Illumio’s ISO 27001 Certification Strengthens Your Supply Chain Security
Learn what Illumio's ISO 27001 and ISO 27701 certifications mean for our customers' cyber resilience and supply chain security.

BT and Illumio: Simplifying DORA Compliance
Learn how to boost cyber resilience, manage ICT risks, and prepare your financial institution for the January 2025 DORA compliance deadline.

Preparing for DORA: Insights from 2 Cybersecurity Compliance Experts
Get insights from Tristan Morgan, managing director of cybersecurity at BT, and Mark Hendry, digital services partner at Evelyn Partners, on navigating DORA compliance.

How to Achieve DORA Compliance With Illumio
Learn the three tools available in the Illumio Zero Trust Segmentation (ZTS) Platform that will help you build DORA compliance.

The EU's NIS2 and DORA Security Directives: What You Need to Know
Learn the 3 ways Illumio Zero Trust Segmentation can help achieve NIS2 and DORA compliance.

5 Reasons Your Auditor Will Love Microsegmentation
Auditors perform an important task for any information security team. Outside perspective gives the whole organization a chance to question stated and unstated assumptions around how things work and should work, and how the organization is secured.

How Cathay Pacific Fast-Tracked Segmentation and Compliance Success with Illumio
Tune into this video with Kerry Peirse on how Cathay Pacific implemented micro-segmentation in less than 3 months. Stop lateral movement, meet compliance demands.

Understanding EU Compliance Mandates: Telecommunications-5G and Beyond
In part 5 of this series, we explore the expanded attack surface 5G brings, along with the telecom compliance mandates that are rapidly evolving.

Understanding EU Compliance Mandates: GDPR, Cyber Essentials
GDPR primarily focuses on data protection, data handling, and privacy concerns for EU citizens’ Personally Identifiable Information (PII).
Related resources








Illumio + Netskope for DORA Compliance
Meet key DORA requirements with the Illumio plugin for Threat Exchange, part of the Netskope Cloud Exchange.
.webp)







Strategies for DORA Compliance: The Key Role of Microsegmentation
The EU finance sector deadline is January 2025. Is your organization prepared?








Le gouvernement met en œuvre Zero Trust pour un avenir plus sûr
Webinaire du panel d'experts de FedInsider sur Zero Trust








Compliance With Gulf States Data Protection Laws
Illumio Zero Trust Segmentation helps organizations safeguard sensitive data and comply with new data protection rules in Gulf states.








Mapping Illumio to NIST SP 800-207 Zero Trust Architecture
See how Illumio Core and Illumio Edge components map to the NIST Zero Trust Architecture core logical components.








PCI Segmentation TCO: Hardware Firewalls vs. Illumio Core
Get a comparison of the total cost of ownership between hardware firewalls and Illumio Core to support PCI segmentation.
Assume Breach.
Minimize Impact.
Increase Resilience.
Ready to learn more about Zero Trust Segmentation?