Dive deeper into Illumio Zero Trust Segmentation with think pieces, Illumineer profiles, instructional guides, and more
.svg)
Illumio Products
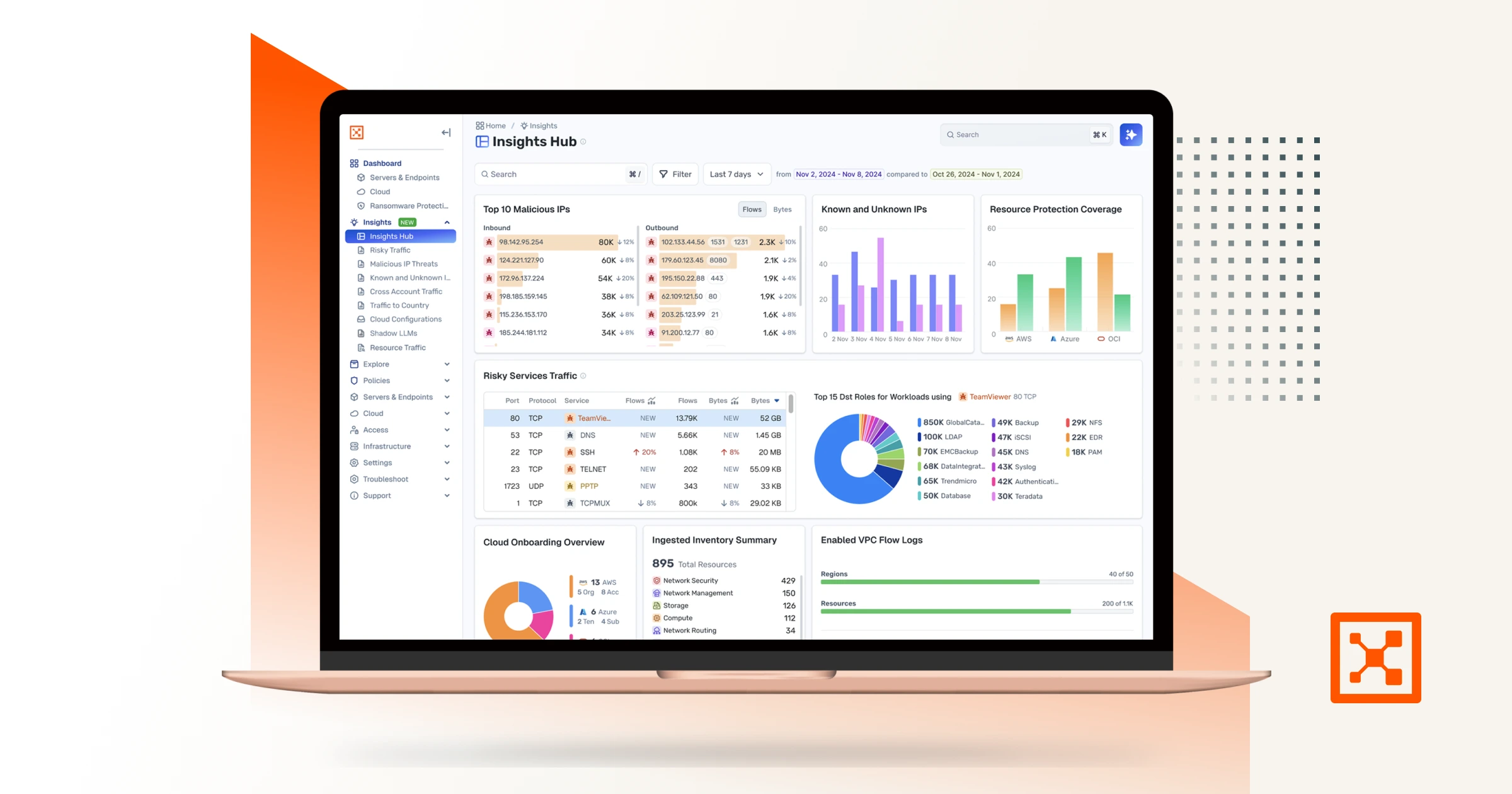
3 Ways to Get the Most Out of Your Illumio Insights Free Trial
Maximize your Illumio Insights free trial with three practical steps to expose lateral movement, visualize hybrid cloud traffic, and accelerate breach containment.

Cloud Detection and Response (CDR) Is Evolving. Here’s Where Illumio Insights Fits.
See where cloud detection and response hits limits and how Illumio Insights improves real-time detection and lateral movement containment.

Illumio Is a 2026 Gartner Peer Insights Customers’ Choice for Network Security Microsegmentation
Learn why customers recognize Illumio as a 2026 Gartner Peer Insights Customers’ Choice for microsegmentation and breach containment.

How Cloud Detection and Response with Illumio Insights Helps You Stay Compliant
Learn how cloud detection and response with Illumio Insights helps meet GDPR, HIPAA, PCI DSS, and DORA compliance with better visibility and faster response.
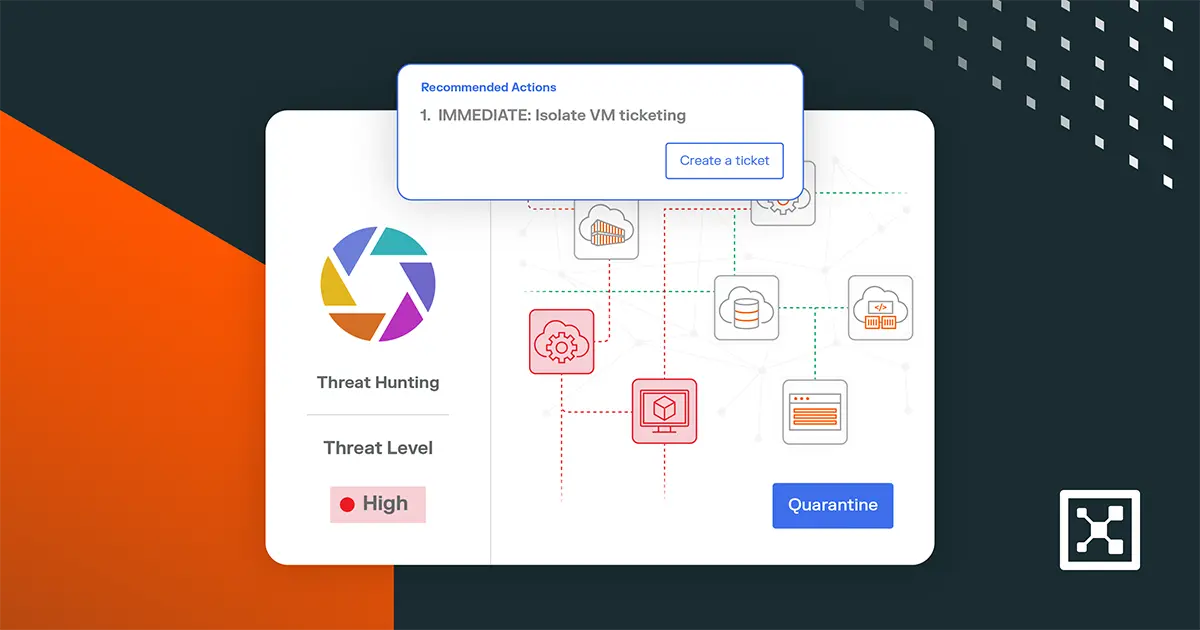
Meet Insights Agent: Your AI Teammate for Threat Detection and Response
Discover how Illumio Insights Agent uses AI to detect, investigate, and contain threats faster with persona-based insights, one-click response, and ticketing.
.webp)
10 Reasons Why Illumio Is the Fastest Way to Build Breach Containment
Learn 10 ways Illumio delivers lightning-fast breach containment with instant visibility and one-click threat isolation.

Illumio for Microsoft Sentinel: Unified, Graph-Powered Security at Cloud Scale
Discover how Illumio for Microsoft Sentinel delivers unified, graph-powered breach containment and AI-driven detection across the Microsoft cloud ecosystem.

Stop Chasing Shadows: Smarter Threat Hunting with Illumio Insights
See how Illumio Insights gives threat hunters real context, faster investigations, and one-click breach containment.

Detect and Contain Lateral Movement in the Cloud with Illumio Insights
Learn how Illumio Insights detects and contains lateral movement in the cloud, stops attackers in real time, and strengthens your security posture.

Illumio Agentless Container Security Expands to AKS, GKE, and OpenShift OVN
Learn how Illumio’s agentless container security now protects AKS, GKE, and OpenShift OVN, delivering fast, frictionless Kubernetes protection.
.webp)
How to Contain Breaches and Regain Control in Your Multi-Cloud Environment
Learn how Illumio delivers visibility and breach containment across cloud platforms, helping you stop lateral movement and secure hybrid, multi-cloud environments.

AI-Powered Cloud Observability: A Deeper Look at Illumio Insights with CPO Mario Espinoza
Discover how Illumio Insights uses AI-powered cloud observability to detect and contain cyber threats in real time.
Assume Breach.
Minimize Impact.
Increase Resilience.
Ready to learn more about Zero Trust Segmentation?