Zero Trust: The imperative for modern security realities
Illumio turns Zero Trust from principle into practice with visibility, simplified segmentation, and control across hybrid, multi cloud environments.
.avif)


.svg)
Why Zero Trust?
Zero Trust starts with an “assume breach” mindset. In a world where detection and response alone aren’t enough — containment has become essential. Build least-privilege access and continuous control to stop threats from spreading across your hybrid, multi cloud environment.
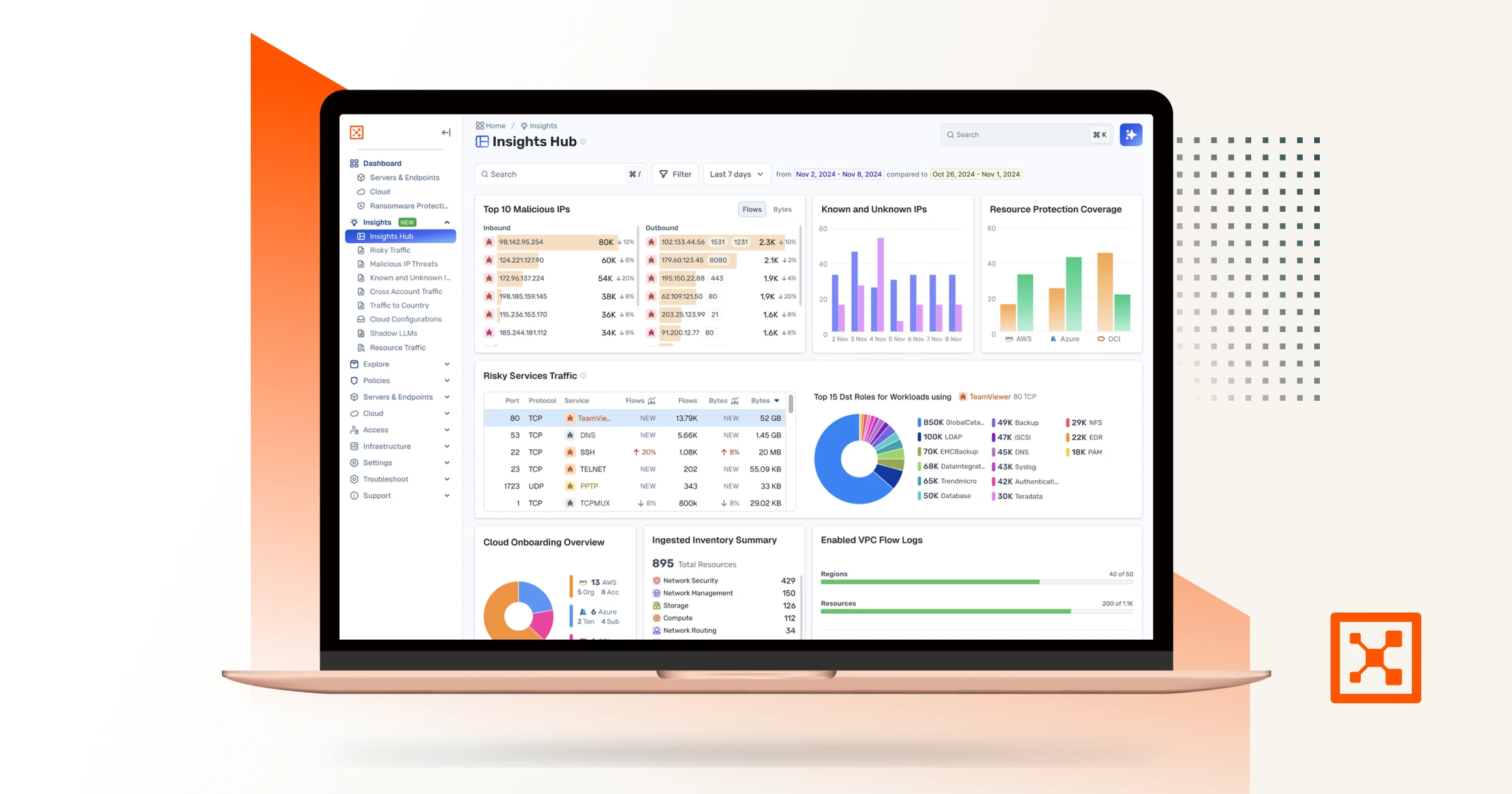
Gain visibility and context into every interaction across your hybrid, multi cloud to uncover risks and detect threats.
Limit communication to only what’s necessary and prevent threats from spreading laterally.
Apply consistent policies and adapt as your environment evolves.
Anticipate threats before they strike and respond with confidence when they do.

Breaches are inevitable. Disasters are optional.
Starting with the understanding that breaches can — and will — happen changes everything. With Illumio, transform uncertainty into cyber resilience and ensure your organization keeps running, no matter what happens.
Understand relationships and communications to map exposure risk of systems and data.
Identify the right security posture and secure applications through least privilege policies.
Ensure Zero Trust security posture adapts to changes in your environment to maintain the least privilege state.

Zero Trust simplified with Illumio Insights and Illumio Segmentation
Learn how Illumio delivers visibility, simplified segmentation, and breach containment to stop ransomware and lateral movement at scale.
.avif)
With Illumio, we are doing Zero Trust very efficiently, effectively and inexpensively. And now that I have all the endpoints covered, I couldn’t be happier.
Hartwig