Inside the F5 Breach: What It Teaches Us About State-Sponsored Cyberattacks
State-sponsored cyberattacks have expanded far beyond government targets, reaching every sector of the economy.
Once focused mainly on cyber espionage, these operations now include destructive attacks on critical infrastructure. Often, they work alongside cybercrime groups.
These attackers are patient, stealthy, and well-funded. They exploit zero-day vulnerabilities. They move laterally through networks. And worst of all, they can remain undetected for months.
The cybersecurity industry has made major progress in helping security teams defend against these advanced attacks. Yet how many defenders truly know who is active in their estate right now? And how many can see which risky combinations have already been exploited and remain live?
Once attackers gain access, they can spread fast. And perimeter defenses can’t stop all of them.
A recent high-profile breach of security vendor F5 serves as a prime example. It’s a case study in how a single foothold can give attackers access to high-value assets, even inside a mature, well-funded security program.
To understand what makes this breach so instructive — and what it reveals about today’s state-sponsored campaigns — let’s take a closer look. We’ll explore:
- How it unfolded
- What it reveals about modern nation-state attacks
- How Illumio Insights can help detect, contain, and stop them faster
What we know about the F5 breach
The breach, discovered in August 2025, was carried out by the threat actor UNC5221. The group has suspected ties to China and is known for using advanced tactics.
UNC5221 entered F5’s BIG-IP product-development and engineering knowledge environments. The attackers stole BIG-IP source code, details on undisclosed vulnerabilities (non-critical or not remotely exploitable), and a small subset of customer configuration data.
There’s no evidence that the attackers tampered with code. But the stolen vulnerability data could enable future zero-day exploits.
After the breach, F5 launched a response plan. Affected BIG-IP customers got a one-year offer of CrowdStrike Falcon endpoint detection and response (EDR) protection.
How Illumio Insights can help
Monitoring your F5 estate with CrowdStrike is a strong first step. But it won’t show how east–west traffic behaves, reveal risky services across subnets, virtual private clouds (VPCs), and virtual networks (VNets). And it won’t help contain attackers as they move laterally across your network.
Once attackers gain access, they move across workloads, subnets, and virtual networks. The biggest risk lies in east-west traffic. That’s the internal system-to-system communication most defenses overlook.
Here’s why it matters: if you can’t see east-west traffic or understand its context, you can’t control it. And without deep observability and context, attackers can move freely across your environment.
But security graph-driven insights can visualize your entire estate, uncover hidden risks before they’re exploited, and quickly detect malicious behavior to minimize its impact.
Here’s how you can use Illumio Insights to prevent and contain attacks like the F5 breach.
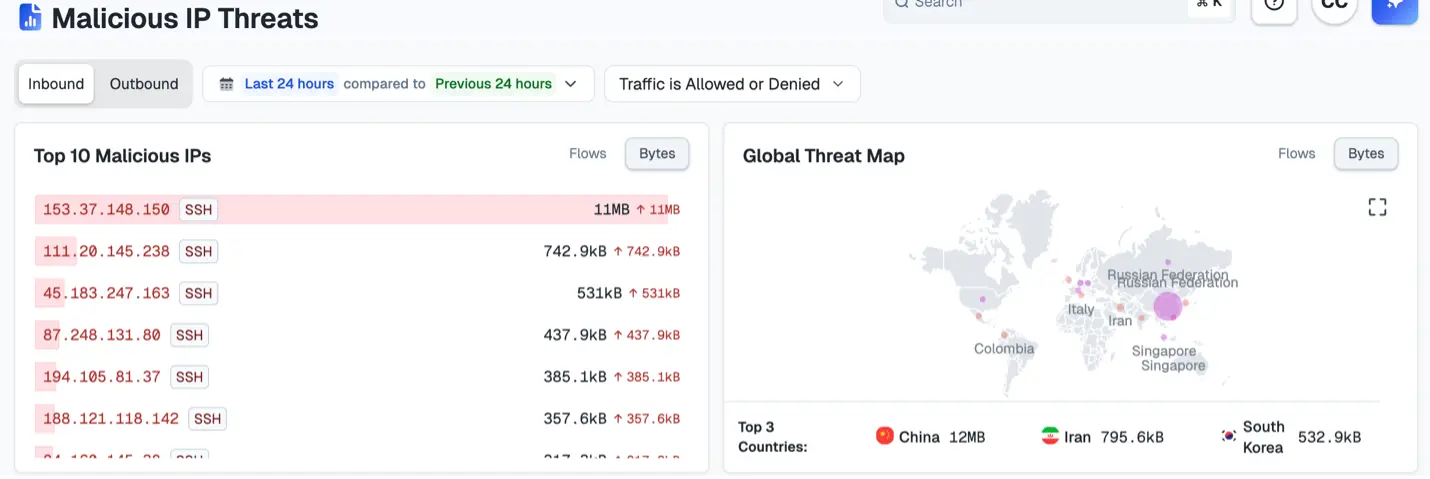
Step 1: Review malicious IP connectivity in the Insights hub
Malicious IP addresses are often the first indicators of compromise. Insights uses threat intelligence to flag known bad actors and suspicious external connections.
Reviewing these helps you:
- Detect early reconnaissance or command-and-control (C2) activity
- Prioritize investigation by threat severity
- Identify workloads that communicate with risky destinations
Together, these insights give you an early warning system. They help you spot potential breaches before they escalate.
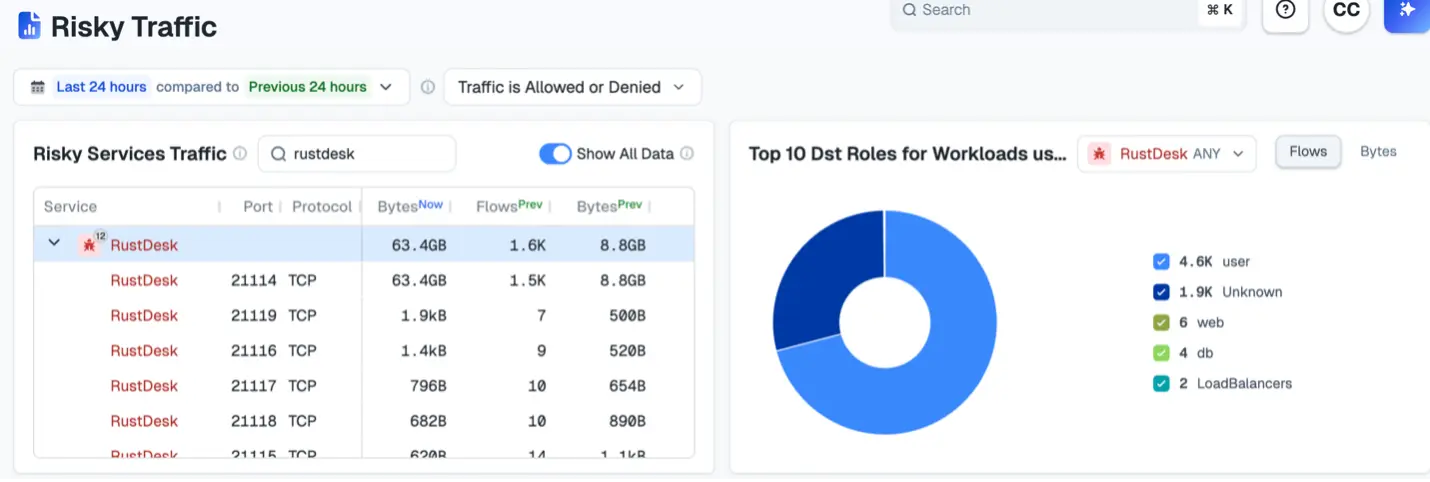
Step 2: Evaluate all risky services in use
Attackers often target remote access tools to move laterally or gain higher privileges. On a regular basis, review how these services are used so you can:
- Spot unauthorized access attempts or unusual login methods.
- Uncover shadow IT or unsafe remote access tools that don't belong in your environment.
- Track changes in usage over time.
Comparing activity over time helps you understand your network’s normal baseline and quickly spot anomalies that might indicate compromise.
For example, a sudden spike in Secure Shell protocol (SSH) connections could signal an issue. The comparison also connects suspicious activity to known incidents or alerts, adding valuable context for investigations.
In the example below, Rustdesk connectivity has spiked in the past 24 hours. This is a clear anomaly worth looking into.
The AI security graph adds crucial context by showing both the traffic and its relationships. That raises key questions. Why is Rustdesk connecting to your user estate? And is that activity legitimate or a sign of compromise?
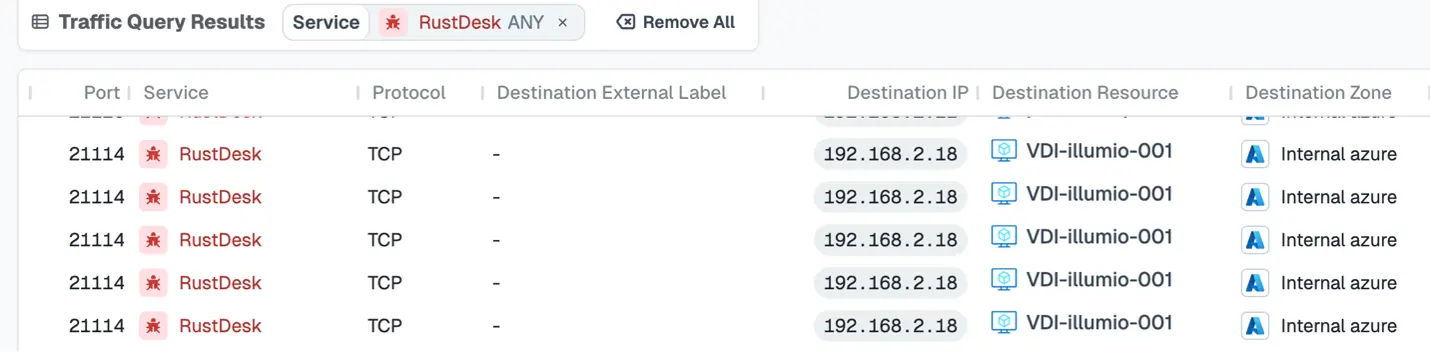
Next, we can narrow down the workload in question here to our virtual desktop infrastructure (VDI) estate: VDI-Illumio-001.
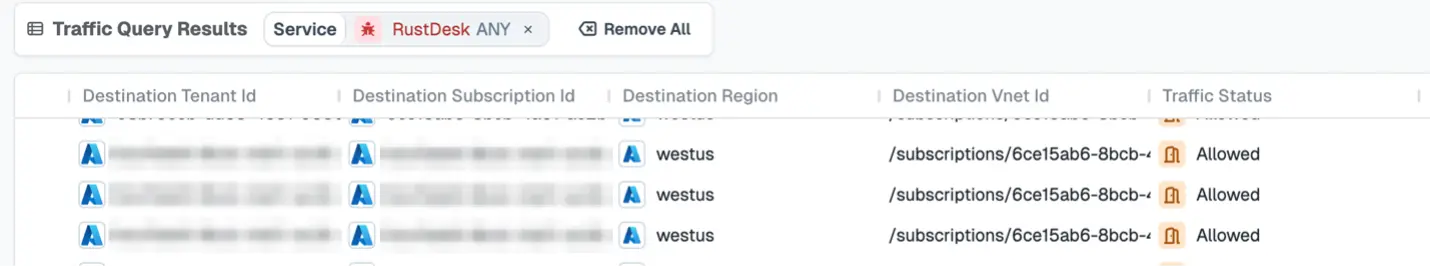
And we can see if the traffic has bypassed any security controls.
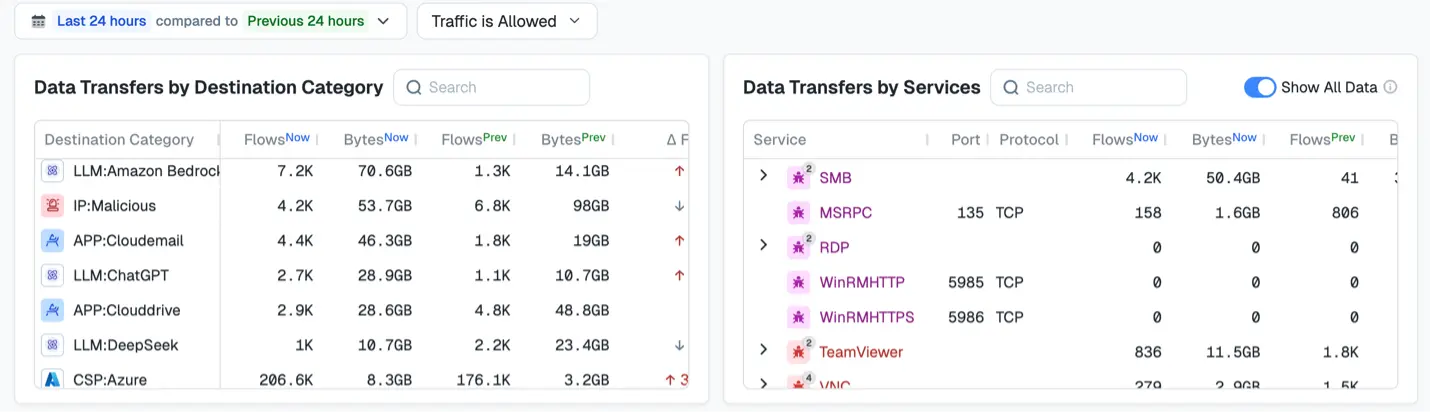
Step 3: Evaluate workload data transfer
Comparing data transfer volumes across different timeframes — such as the last 24 hours compared to the previous 24 — helps spot unusual spikes or patterns. These may indicate data theft or staging for ransomware.
This step helps us in three key ways. First, it creates baselines by determining the normal volume and direction of data flows. It also provides context for transfers to external or untrusted destinations. Finally, it reveals peer-to-peer traffic that might bypass perimeter controls.
By lining up this data with known attack timelines — such as the F5 breach — you can see how the activity unfolded, retrace attacker steps, and quickly focus your investigation. You can track when transfers began and whether they match suspicious logins or risky activity like remote desktop protocol (RDP) or Rustdesk use.
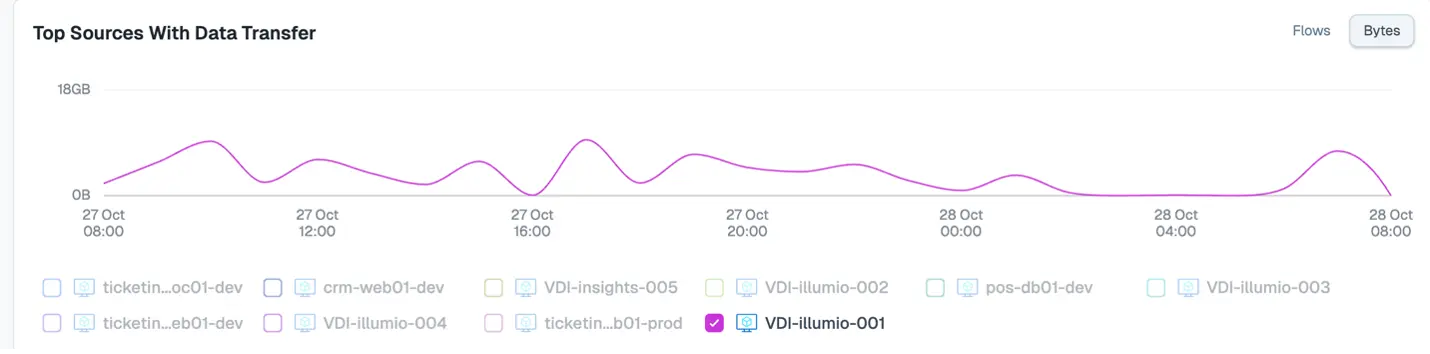
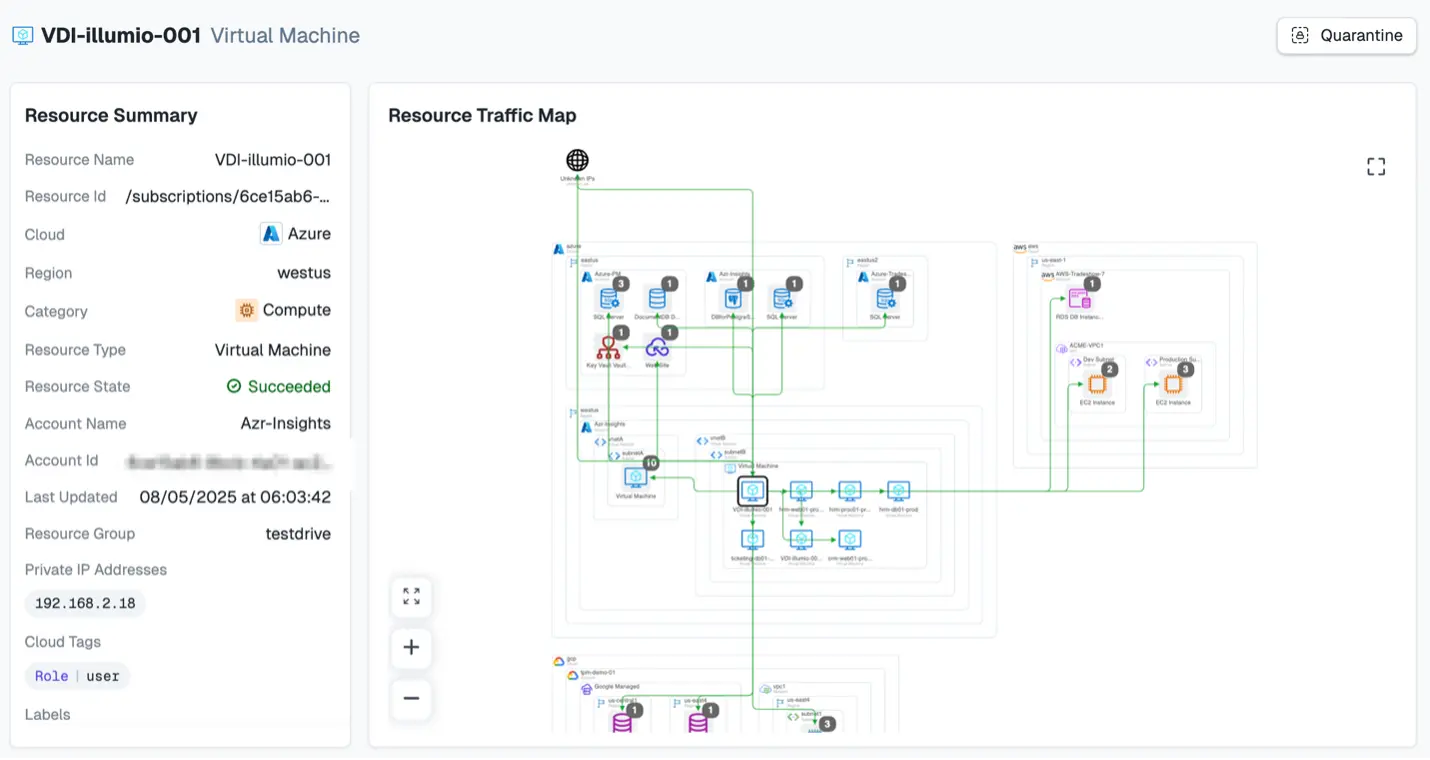
Step 4: Use the resource graph to identify suspicious traffic
East-west traffic is easy to overlook. But it’s critical for detecting lateral movement.
The Insights resource graph helps you:
- Visualize how workloads, VPCs, VNets, and services connect.
- Spot unexpected connections between environments, such as development to production.
- Identify workloads that bypass your segmentation policies.
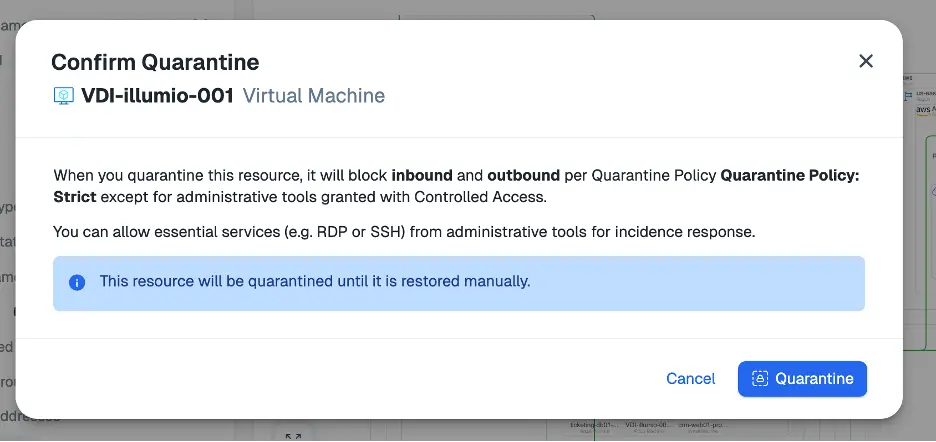
In Insights, we can further investigate our VDI workload that had inbound Rustdesk traffic. Notice the Quarantine button in the top right of the screenshot: you’ll use it in the next step.
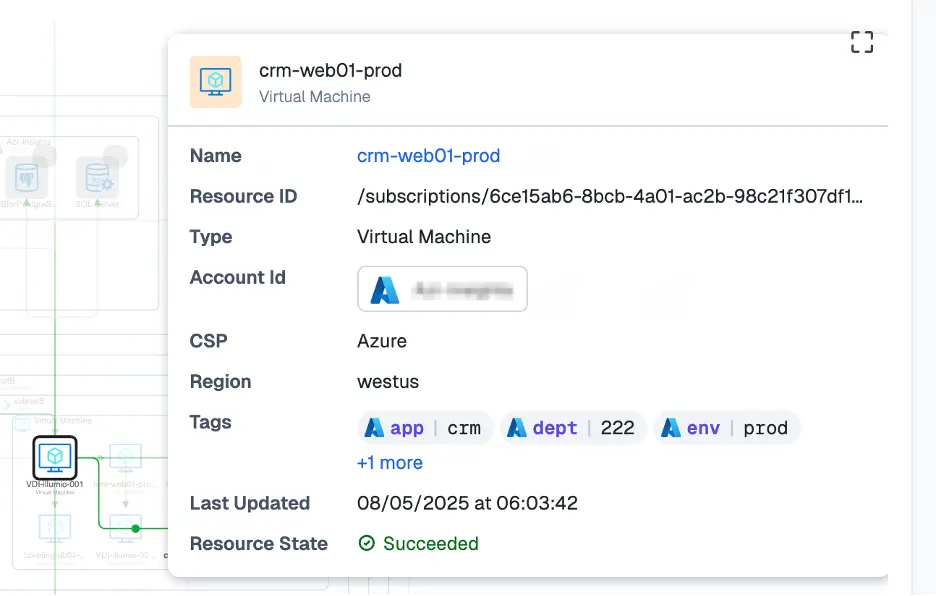
Insights provides the context you need to assess potential impact. Ask yourself: Do we have unauthorized access to the customer relationship management (CRM) system or customer records?
Step 6: Use one-click containment to limit attack spread and support forensic analysis
When you detect suspicious activity — such as a spike in Rustdesk connectivity or unusual east-west traffic — time is critical.
Traditional containment often requires manual firewall changes or complex orchestration that can take hours or even days.
One-click containment — accessible through the Quarantine button — changes that dynamic. It allows security teams to instantly isolate compromised workloads without disrupting the broader environment.
With one-click containment, you can:
- Stop lateral movement instantly. Prevent attackers from pivoting deeper into your environment or accessing sensitive workloads.
- Preserve forensic evidence. Isolation keeps the compromised system intact for investigation while cutting off active threats.
- Reduce the blast radius. Limit the impact to a single workload instead of entire segments or applications.
- Accelerate response. Turn a multi-step, manual process into a single, decisive action.
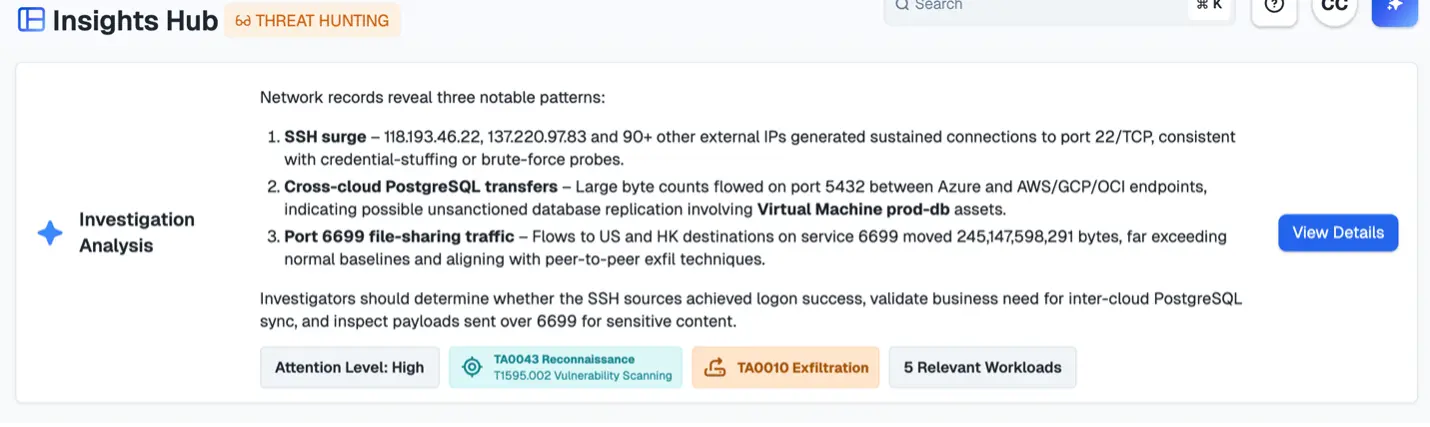
Step 7: Use Insights Agent to review and generate investigation reports
Imagine a digital assistant that speeds up your entire investigation process. The Insights Agent is your fastest path to clarity and breach containment.
Here’s what makes it so powerful:
- Automated investigation. The agent continuously monitors cloud-scale network data and workload communications. Applying an AI security graph, it instantly correlates operations across your infrastructure to uncover threats.
- Context-rich reports. It produces severity-ranked analysis tailored to each role. Threat hunters, responders, and compliance analysts, for instance, each get insights relevant to their work. Every finding is mapped to the MITRE ATT&CK framework for added context.
- Proactive recommendations. Beyond detection, it suggests prioritized containment actions and segmentation policies to reduce risk, guiding you from insight to execution.
- Integrated one-click containment. Detection flows seamlessly into remediation. You can isolate compromised workloads instantly. It integrates natively with Illumio Segmentation, so containment doesn’t depend on host agents.
By using the Insights Agent, your team shifts from reactive triage to proactive resolution. This helps you cut through alert noise, gain actionable clarity, and contain threats before they escalate.
The clock is ticking
The F5 breach shows that anyone can be surprised by stealthy, persistent state-sponsored attackers.
By the time a breach is discovered, attackers may already have stolen sensitive data, mapped your environment, and laid the groundwork for their next move.
Traditional defenses weren’t built for this kind of adversary. Firewalls, endpoint tools, and perimeter-based monitoring can’t keep pace with the speed and subtlety of a state-sponsored campaign.
What defenders need now is deep, continuous visibility. They need to know not just what’s coming in and out of the network, but what’s moving within it.
That’s the power of Insights and the new AI-driven Insights Agent. Together, they give security teams the context, speed, and precision to detect lateral movement early and contain threats fast.
State-sponsored attacks aren’t slowing down. But your response can get faster, smarter, and more controlled. Everyone should be preparing as if the next F5-style breach is already unfolding in their network — because it might be.
Don’t wait for the next breach to expose your blind spots. Experience Illumio Insights free today.
.webp)



.webp)


