Breach Containment: A Complete Guide for Organizations
What is Breach Containment?
Breach containment refers to the strategies and actions taken to limit the scope and impact of a cybersecurity incident after it has been detected. Unlike breach detection, which focuses on identifying threats, containment aims to prevent the lateral movement of attackers within the network, thereby protecting critical assets and data.
Effective breach containment is a pivotal phase in the incident response lifecycle, bridging the gap between detection and eradication. It involves isolating affected systems, implementing access controls, and leveraging technologies like microsegmentation to halt the progression of the attack.
Why Breach Containment Is Critical for Organizations
Rising Frequency and Cost of Data Breaches
Cyberattacks are becoming increasingly common and costly. According to IBM's 2024 Cost of a Data Breach Report, the average cost of a data breach reached $4.45 million, marking a significant increase from previous years. The financial implications, coupled with reputational damage, underscore the necessity for robust breach containment strategies.
Dwell Time and Lateral Movement: The Silent Risks
Dwell time — the period between a breach's occurrence and its detection — can extend for months, providing attackers ample opportunity to move laterally within the network. This lateral movement allows them to access sensitive data and systems, amplifying the breach's impact. Containment strategies aim to reduce dwell time and restrict lateral movement, thereby mitigating potential damages.
Regulatory Compliance Implications
Regulations like GDPR, HIPAA, and PCI-DSS mandate stringent data protection measures. Failure to contain breaches promptly can result in hefty fines and legal consequences. Implementing effective containment measures demonstrates compliance and a commitment to data security.
Damage to Reputation and Trust
Beyond financial losses, data breaches erode customer trust and tarnish brand reputation. Swift containment minimizes the breach's visibility and impact, helping organizations maintain stakeholder confidence.
Key Benefits of Effective Breach Containment
- Minimizes Attack Blast Radius: By isolating affected systems, containment prevents the spread of the breach to other parts of the network.
- Reduces Mean Time to Respond (MTTR): Quick containment actions lead to faster resolution of incidents, reducing downtime and associated costs.
- Protects Sensitive Data and Business Continuity: Containment safeguards critical data and ensures that business operations can continue with minimal disruption.
- Enhances Audit Readiness and Compliance Posture: Demonstrating effective containment measures can facilitate compliance audits and regulatory reviews.
- Boosts Stakeholder Confidence: Proactive containment strategies reassure customers, partners, and investors of the organization's commitment to security.
Core Principles of Effective Breach Containment
Segmentation and Microsegmentation
Segmentation involves dividing a network into distinct zones to control traffic flow. Microsegmentation takes this further by creating granular zones down to individual workloads or applications. This approach is essential for implementing a Zero Trust model, ensuring that even if one segment is compromised, the breach cannot easily spread.
Visibility and Real-Time Telemetry
Understanding how applications and systems communicate is vital for detecting anomalies. Real-time telemetry provides insights into network traffic, enabling swift identification and containment of threats.
Automation and Orchestration
Automated responses to detected threats can significantly reduce response times. Orchestration tools coordinate these automated actions across various systems, ensuring a cohesive containment strategy.
Containment Without Business Disruption
Effective containment should not hinder business operations. Strategies must be designed to isolate threats while maintaining the functionality of unaffected systems, ensuring continuity.
Breach Containment Strategy Framework
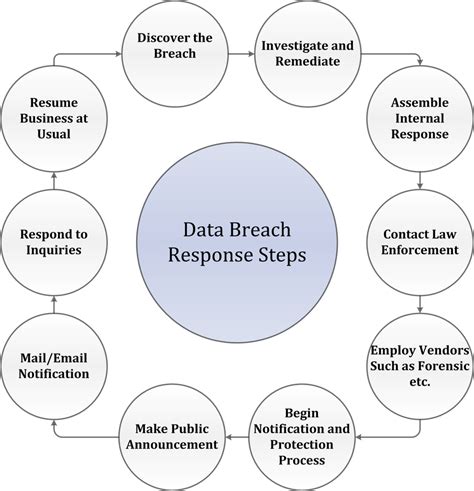
A successful breach containment strategy isn’t something you improvise in the heat of an incident — it must be structured, proactive, and continuously refined. This framework outlines the six essential steps organizations should follow to minimize damage, restore operations quickly, and build long-term cyber resilience.
- Assess: Map the network to identify critical assets and potential vulnerabilities.
- Design: Develop segmentation policies and containment strategies tailored to the organization's infrastructure.
- Implement: Deploy the designed policies and ensure they are enforced across the network.
- Monitor: Continuously observe network traffic and system behaviors to detect anomalies.
- Respond: Upon detecting a breach, execute containment measures promptly to isolate the threat.
- Evolve: Regularly update and refine containment strategies based on lessons learned and emerging threats.
By following this step-by-step containment strategy, organizations can significantly reduce the fallout from cybersecurity incidents. With proper planning and the right technologies in place, teams are better equipped to respond swiftly and adapt to an evolving threat landscape.
Technologies That Enable Breach Containment
Containment is only as strong as the technologies supporting it. Today’s cybersecurity landscape demands a layered, integrated tech stack that enables visibility, control, and rapid response across diverse environments — from on-premises to cloud and everything in between.
- Microsegmentation Platforms: Tools like Illumio provide granular control over network traffic, essential for effective containment.
- Zero Trust Architecture: This security model assumes no implicit trust, requiring verification for every access request, thereby limiting breach propagation.
- EDR/XDR Integrations: Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) tools detect and respond to threats across endpoints and networks.
- Security Orchestration Automation and Response (SOAR) Tools: These platforms automate threat detection and response processes, enhancing efficiency.
- Deception Technologies and Honeypots: By deploying decoy systems, organizations can detect and analyze attacker behaviors without risking actual assets.
When used in concert, these technologies form the backbone of an effective breach containment strategy. By leveraging solutions like Illumio’s microsegmentation and Zero Trust enforcement, organizations can dramatically reduce risk, stop lateral movement, and protect their most valuable digital assets.
How Illumio Helps Organizations Contain Breaches
Illumio's microsegmentation technology offers a proactive approach to breach containment. By visualizing application dependencies and enforcing segmentation policies, Illumio limits the lateral movement of threats within the network.
Our agent-based approach ensures compatibility with various environments, including legacy systems. Integration with existing security ecosystems allows for seamless deployment and operation.
Case Example: "Containment in Seconds, Not Hours"
A global financial institution implemented Illumio's solutions and reduced their breach containment time from hours to mere seconds, significantly minimizing potential damages.
Real-World Use Cases
Ransomware Containment
In a notable incident, a manufacturing company faced a ransomware attack. By utilizing Illumio's microsegmentation, they swiftly isolated affected systems, preventing the spread and ensuring operational continuity.
Insider Threat Containment
A healthcare provider detected unauthorized access by an internal user. Implementing segmentation controls, they restricted the user's access, safeguarding patient data.
Cloud and Hybrid Environment Containment
A tech firm operating in a hybrid cloud environment employed Illumio's solutions to maintain visibility and control across their infrastructure, effectively containing potential breaches.
Operational Technology (OT) Security
An energy sector company integrated Illumio's microsegmentation into their OT systems, enhancing security without disrupting critical operations.
Common Challenges in Breach Containment—and How to Overcome Them
While breach containment is a critical cybersecurity capability, implementing it effectively isn’t without obstacles. Many organizations face technical and cultural roadblocks that hinder their ability to respond swiftly when incidents occur. Below are some of the most common challenges, along with practical solutions to overcome them.
Lack of Network Visibility
One of the most significant hurdles in breach containment is a lack of real-time visibility into how systems and applications interact. Without this insight, security teams are essentially flying blind during an attack, making it difficult to detect anomalies or trace the lateral movement of a threat.
Solution: Implement tools that provide comprehensive insights into network traffic and system interactions. Illumio, for example, offers dynamic application dependency mapping that visualizes communication flows and highlights exposure risks, allowing teams to respond with precision.
Resistance to Operational Disruption
Containment strategies are often viewed as disruptive to daily operations, especially if they involve abruptly isolating systems or shutting down services. This friction between security and operations can delay response times and increase the breach’s impact.
Solution: Design containment strategies with business continuity in mind. Employ technologies like microsegmentation that allow for surgical isolation of affected workloads while allowing unaffected systems to continue running. Communicate the value of containment in minimizing long-term disruption to gain buy-in from business stakeholders..
Integration Challenges with Legacy Systems
Legacy infrastructure often lacks the flexibility to integrate with modern containment tools, leaving security gaps and increasing complexity.
Solution: Choose technologies that are infrastructure-agnostic and compatible with a wide range of environments, including older systems. Illumio’s agent-based model allows for seamless deployment across legacy and modern infrastructure without requiring disruptive architectural changes.
By proactively addressing these challenges, organizations can strengthen their breach containment capabilities and improve their overall cybersecurity posture—turning potential vulnerabilities into points of resilience.
Key Metrics and KPIs for Measuring Containment Success
- Mean Time to Contain (MTTC): The average duration between breach detection and containment.
- Lateral Movement Attempts Blocked: Number of unauthorized access attempts prevented post-containment implementation.
- Systems Impacted Before and After Containment Controls: Comparison to assess the effectiveness of containment measures.
- Policy Coverage vs. Exposure Mapping: Evaluation of the extent to which security policies protect critical assets.
Conclusion
Data breach containment is not just a reactive measure but a proactive strategy essential for modern cybersecurity. By implementing effective containment practices, organizations can protect their assets, maintain compliance, and uphold stakeholder trust.
Illumio's breach containment solutions offer the tools and expertise necessary to navigate the complex cybersecurity landscape with confidence and agility. From enforcing Zero Trust through microsegmentation to accelerating breach isolation with real-time visibility, Illumio empowers development, security operations (DevSecOps), and cybersecurity teams to contain incidents swiftly and prevent business disruption.
When every second counts, Illumio’s platform reduces response time from hours to seconds—helping organizations move from reactive firefighting to proactive cyber resilience. If you’re ready to build a containment-first security strategy, explore Illumio’s solutions for breach containment, critical asset protection, or cloud security to get started today.
Frequently Asked Questions (FAQs)
1. What is breach containment in cybersecurity?
Breach containment is the process of limiting the spread and impact of a cybersecurity incident after it’s detected. It involves isolating compromised systems, enforcing segmentation policies, and stopping lateral movement to protect critical assets.
2. How is breach containment different from breach detection?
Detection focuses on identifying a breach, while containment is about taking action to stop the threat from spreading. Both are part of the broader data breach response process, but containment is the decisive step that reduces damage.
3. What is incident containment in the context of a data breach response plan?
Incident containment is a stage in the incident response lifecycle where affected systems are quarantined, access is restricted, and threats are prevented from moving laterally across the network.
4. What are some common containment strategies for incident response?
Common containment strategies include microsegmentation, enforcing least privilege access, network isolation, using SOAR tools, and deploying honeypots or decoys to detect lateral movement attempts.
5. How long should it take to contain a data breach?
Ideally, breach containment should occur within minutes to hours. The faster the Mean Time to Contain (MTTC), the less impact the breach has. Tools like Illumio can reduce containment time to seconds.
6. Can breach containment be achieved in cloud and hybrid environments?
Yes. Solutions and tools such as Illumio’s Cloud Security Solutions let like Illumio CloudSecure, organizations extend containment strategies across hybrid and multi-cloud environments, maintaining visibility and control.
7. Why is microsegmentation important for breach containment?
Microsegmentation allows security teams to create granular, enforceable boundaries around workloads. This stops lateral movement and limits the blast radius of an attack, even if the initial breach goes undetected.
8. How does breach containment help with regulatory compliance?
Effective containment supports compliance with regulations like GDPR, HIPAA, and PCI-DSS by demonstrating due diligence, reducing exposure of sensitive data, and ensuring timely incident response.
9. What tools are best for breach detection and response?
A robust toolkit includes EDR/XDR platforms, SOAR systems, threat intelligence feeds, microsegmentation platforms like Illumio, and visibility tools for real-time telemetry.
10. How does Illumio support DevSecOps teams in breach containment?
Illumio empowers DevSecOps teams with real-time application dependency maps, proactive segmentation policies, and dynamic breach response tools, ensuring security is embedded in development and operations workflows without slowing down innovation.
.png)