Stop Chasing Shadows: Smarter Threat Hunting with Illumio Insights
Attackers today move fast. And with the help of AI, they’re stealthier than ever.
Traditional detection tools often flood analysts with alerts. Without the right context, it’s like chasing shadows.
That’s where threat hunting comes in: proactively searching for signs of compromise before attackers can spread across your environment.
Illumio Insights takes this a step further. By giving deep visibility into workload-to-workload and workload-to-internet traffic, it helps defenders see what other tools miss.
Instead of chasing false positives, Insights helps threat hunters quickly zero in on the real attack paths and contain breaches before they can spread to critical resources.
The challenges of modern threat hunting
While attackers grow more sophisticated, defenders are still relying on outdated assumptions — like the idea that perimeter visibility is enough.
In a world of hybrid infrastructure and ever-expanding cloud workloads, traditional approaches are falling short.
So what’s getting in the way? These common pain points make effective threat hunting harder than it should be:
- East-west blind spots: most tools focus on north-south perimeter traffic, leaving lateral movement in the dark.
- Hybrid, multi-cloud complexity: the mix of Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), Oracle Cloud Infrastructure (OCI), and on-premises workloads can make correlation hard.
- Alert fatigue: too many signals with not enough prioritization leave teams drowning in alerts.
- Slow investigations: data silos force endless pivots between tools, slowing down response.
These challenges don’t just slow down investigations. They create dangerous blind spots that adversaries are all too ready to exploit.
To outpace modern threats, security teams need smarter visibility, tighter integration, and faster ways to pinpoint and contain lateral movement.
How Illumio Insights simplifies threat hunting
Illumio Insights ingests flow logs from AWS, Azure, GCP, OCI, on-premises environments, firewalls, VPNs, and more. It maps every connection, accepted or denied, in one place using an AI security graph.
As a threat hunter, the Insights hub allows you to see all threats to your environment, whether it’s malicious IPs talking to any resources on the network, external data transfers, or high-risk services within the environment.
Here’s an example:
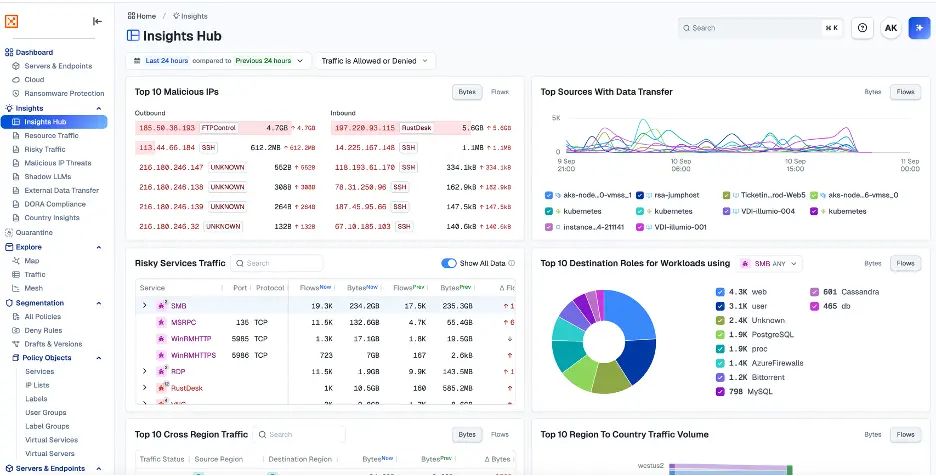
From the dashboard, hunters can quickly spot anomalies. For example, a sudden spike in Rustdesk traffic from a malicious IP stands out.
By examining the connection details, we see continuous Rustdesk traffic between the malicious IP and an internal virtual machine (VM).
This pattern isn’t just a one-off probe. It indicates the attacker has established an active remote session inside the environment.
.webp)
Rustdesk itself isn’t inherently bad, but when a known malicious IP connects through it, alarm bells ring. With a few clicks, the threat hunter can trace the attacker’s path:
- The attacker first maps out the environment, scanning and probing until they discover a wide range of resources. This includes critical PaaS services that many organizations rely on daily.
- During this exploration, they uncover and gain access to a key vault, which stores the sensitive credentials and secrets that protect the environment’s most valuable assets.
- Armed with these stolen keys, the attacker systematically moves toward the mission-critical systems, such as databases full of customer records, high-value storage accounts, and caching layers that support core applications.
- With control over these assets, the attacker sets up a pathway to exfiltrate sensitive data out of the environment. They funnel it into an external storage account under their control, all while attempting to stay under the radar.
.webp)
At this point, the hunter can do more than just see the attack — they can stop it in its tracks with one-click quarantine from Illumio Insights. This feature allows threat hunters to instantly isolate the compromised workload which prevents it from communicating with the rest of the environment or with external destinations.
What makes this powerful is the speed. There’s no need to jump into separate firewall consoles or wait for manual changes. Containment is immediate.
And because Illumio provides controlled access to quarantined systems, administrators and security operations center (SOC) teams can still log in to investigate, gather forensics, and remediate, without risking further spread.
In other words, threat hunters can both visualize the attack path and contain it in real time.

Forensics doesn’t stop at quarantine. With historical flow data, hunters can ask:
- When did this workload first talk to the malicious IP?
- How much data was transferred?
- Do other workloads show the same suspicious behavior?
This context speeds up investigations, sharpens prioritization, and strengthens response.
Illumio Insights: move from reactive to proactive defense
Threat hunting isn’t just about catching bad actors. It’s also about reducing risk and stopping lateral movement before it spreads.
With Illumio Insights, security teams move from siloed alerts to contextual attack path visibility. That means:
- Faster investigations with all data in one place.
- Smarter prioritization based on real attack paths.
- Stronger response through integrated quarantine.
- Scalability across hybrid and multi-cloud environments.
Instead of drowning in noise, defenders get actionable intelligence and a crucial step ahead of attackers.
Try Illumio Insights 14-day free trial today.


.webp)


