.png)

The Illumio Breach Containment Platform
Detect, assess, and stop lateral movement across your hybrid environment with a single platform.
Highlights
Key benefits
Asset preview
Today’s breaches are defined by what happens after attackers get in. Once they’re past the perimeter, modern threats move laterally to compromise sensitive systems. This internal movement — not the initial entry — is what drives operational disruption and catastrophic damage.
Modern environments make this easier. Hybrid and multi-cloud architectures, virtual workloads, IT/OT convergence, and third-party access all increase internal connectivity. Each connection creates another path for attackers to move.
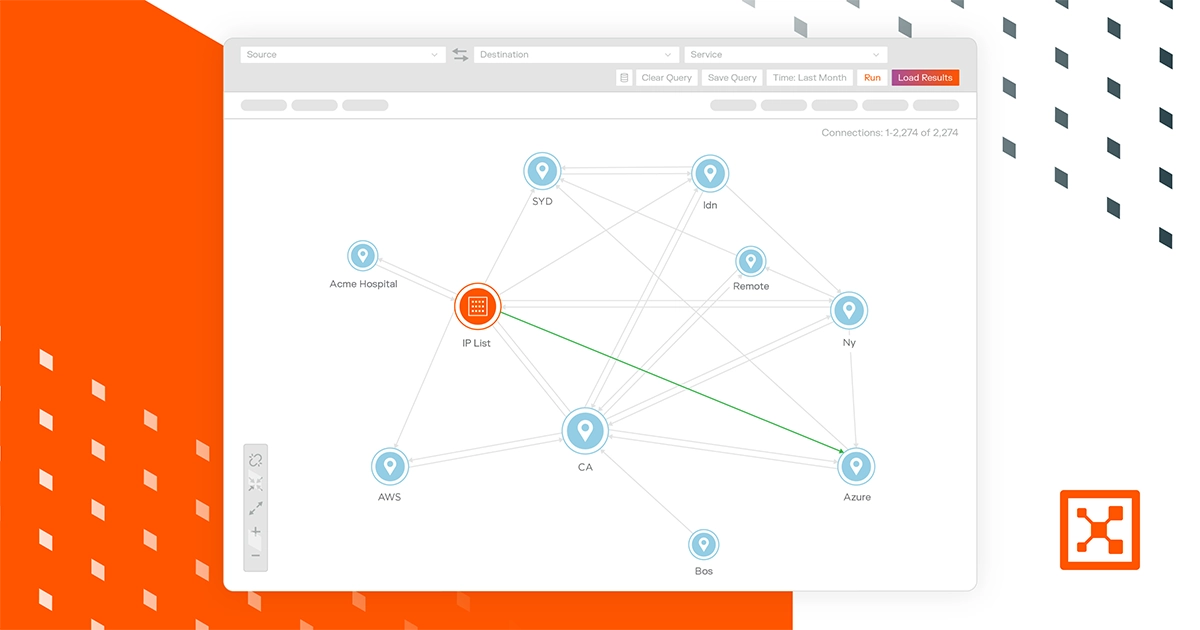
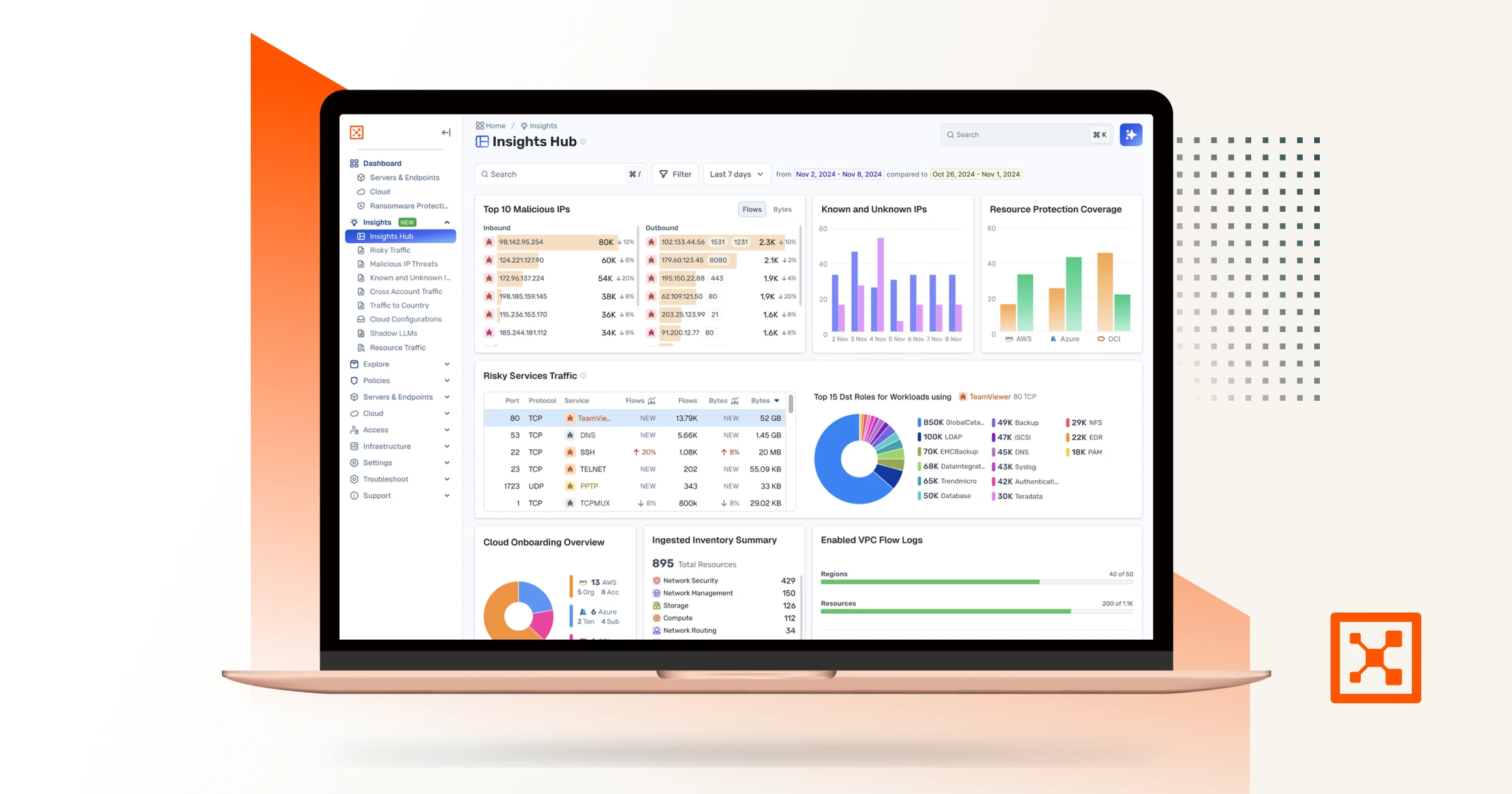
Many security teams lack clear visibility into this internal activity. They can’t easily see traffic flows, system relationships, or where risk concentrates after a breach.
Without this insight, teams struggle to understand exposure across their environment.
At the same time, breach containment has become a business priority. Attackers move faster than teams can respond, and automation increases both speed and impact. Third-party access adds ongoing internal risk that perimeter defenses can’t control.
Executives and regulators now expect proof of security effectiveness. Teams must show how controls reduce the blast radius, support compliance, and protect critical operations.
Yet, security teams are stretched thin and must respond quickly with minimal disruption.
Perimeter-based and detection-only tools fall short once attackers are inside. Organizations need breach containment: continuous visibility and the ability to act before, during, and after a breach.






Assume Breach.
Minimize Impact.
Increase Resilience.
Ready to learn more about Zero Trust Segmentation?


















.webp)
