Security Breach
Many of us have experienced it at one time or another – we go to log into an online account only to discover that we’ve been hacked. We’ve lost access, and there’s a good chance that at least some of our sensitive, personal data is now in unknown hands. But data theft doesn’t just happen to individuals; often, businesses and other organizations are the victims of corporate security breaches.
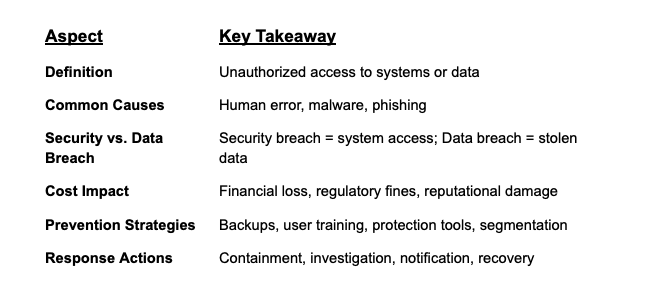
A security breach occurs when an attacker bypasses an organization’s security controls to gain unauthorized access to systems and data. Let's look closer at the types of security breaches and why they happen.
Individual vs. Corporate Breaches
- Individuals may discover they’ve been hacked when they’re locked out of accounts or notice unusual activity, often a sign of personal data exposure.
- Organizations face breaches that target sensitive assets such as credit card data, Social Security numbers, health records and medical information, or internal financial documents.
Why Breaches Happen
1. Human Error
Misconfigurations, unsecured devices, or accidentally shared files can create openings for attackers. A 2019 Shred-it report, based on an Ipsos survey, found that 47% of C-suite executives attributed data breaches to human error or accidental loss by an employee.
2. Malware
Phishing emails, malicious downloads, or fake apps can deliver malware designed to steal login credentials, spy on users, or encrypt data for ransom.
Security Breach vs. Data Breach
- A security breach refers to unauthorized access to IT systems or networks.
- A data breach refers to the theft or exposure of actual sensitive information, often as a result of a security breach.
Costs of a Security Breach
- Direct costs: Incident investigation, containment, regulatory fines, and system recovery.
- Indirect costs: Downtime, brand reputation damage, and customer or user churn.
How to Prevent a Security Breach
Take proactive steps to reduce the likelihood and impact of a breach:
- Employee Training
Educate employees about phishing, password hygiene, and safe data practices. - Regular Backups
Maintain secure backups to protect against data loss from breaches or ransomware. - Email and Endpoint Protection
Deploy tools that detect phishing attempts, scan attachments, and block malware. - Network Segmentation
Use Zero Trust principles and microsegmentation to limit lateral movement in the event of a breach.
Responding to a Security Breach
If a breach occurs, quick response is critical. Steps include:
- Isolate affected systems or networks.
- Conduct a forensic investigation to determine the scope.
- Notify impacted parties in compliance with laws.
- Remediate vulnerabilities and restore from clean backups.
Why It Matters
Security breaches are more than technical glitches: they're business risks with legal, financial, and reputational consequences. Organizations must adopt a proactive, breach-ready security posture that emphasizes containment, resilience, and response preparedness.
With segmentation from Illumio, organizations can limit the impact of breaches by containing attacks before they spread, strengthening security from the inside out.
.png)

.webp)
.webp)
.webp)
.webp)


%2520(1).webp)







