Cyber Resilience
Boost your cyber resilience with Illumio's solutions to reduce the attack surface and recover quickly from security threats.
.svg)
Related blog posts

How Illumio Complements Your Firewalls
Learn why firewalls can’t stop lateral movement in hybrid multi-cloud environments and how Illumio helps contain breaches before they spread.
.webp)
Top Cybersecurity News Stories from February 2026
Explore February 2026 cybersecurity news on breach containment, ICS defense, Illumio integrations with FireMon and Armis, and CRN industry recognition.
%20(1).webp)
Why Security Fundamentals Are the Most Overlooked Part of Adopting a Zero Trust Strategy
Explore why security fundamentals are the most overlooked part of Zero Trust and how getting the basics right determines whether breaches spiral or stay contained.

Illumiverse Labs: Get Hands-On With Breach Containment in Our Live Virtual Experience Events
Experience breach containment in action with Illumiverse Labs, hands-on virtual sessions where practitioners can see and stop lateral movement in real time.
%20(1).webp)
Why OpenClaw (Formerly Known as Clawdbot) Is a Wake-Up Call for AI Agent Security
Discover why OpenClaw exposed the risks of AI agents, turning them into insider threats, and why visibility and segmentation are essential for security.

Digital Escalation Dominance: Why Cyber Success Means Staying Operational
Discover why cyber success now means staying operational under attack and how digital escalation dominance helps organizations preserve continuity and control.
.webp)
Why Detection Fails Without Containment (And How Security Graphs Can Help Fix It)
Learn why detection still leads to breaches and how containment grounded in an AI security graph prevents lateral movement.

French Security Teams Detect Breaches Just Fine. So Why Are They Still Facing Downtime?
Learn why lateral movement still causes downtime in France, despite strong detection, rising budgets, and modern cloud security tools.
.webp)
Cybersecurity Predictions 2026: Expert Insights on the Trends Shaping the Year Ahead
Explore cybersecurity predictions for 2026, including AI threats, supply chain risk, Zero Trust adoption, resilience, and board-level accountability.
.webp)
Top Cybersecurity News Stories From December 2025
Get the top December 2025 cybersecurity news, including London councils' supply chain breaches, Zero Trust hurdles, AI security gaps, and expert guidance on resilience.

What Are You Waiting For? Delaying Cyber Modernization Is Putting You at Risk
Learn why former U.S. federal CIO Tony Scott says delaying cyber modernization is a leadership failure and how to act before a breach forces your hand.
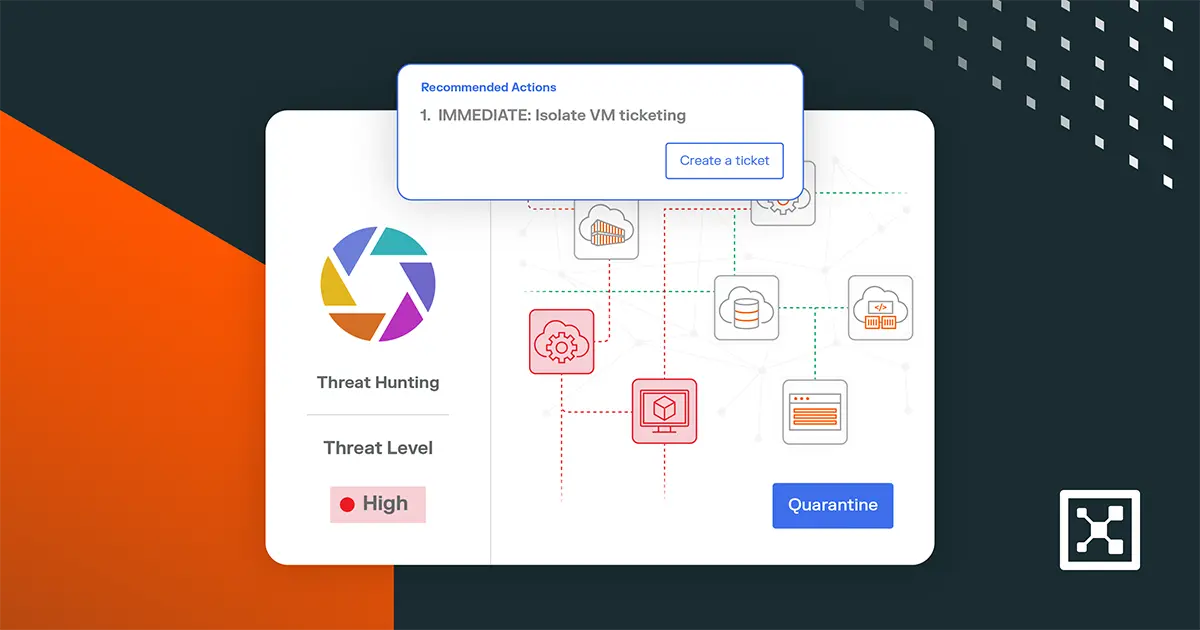
Meet Insights Agent: Your AI Teammate for Threat Detection and Response
Discover how Illumio Insights Agent uses AI to detect, investigate, and contain threats faster with persona-based insights, one-click response, and ticketing.
Related resources
.webp)







The Illumio Breach Containment Platform
Detect, assess, and stop lateral movement across your hybrid environment with a single platform.
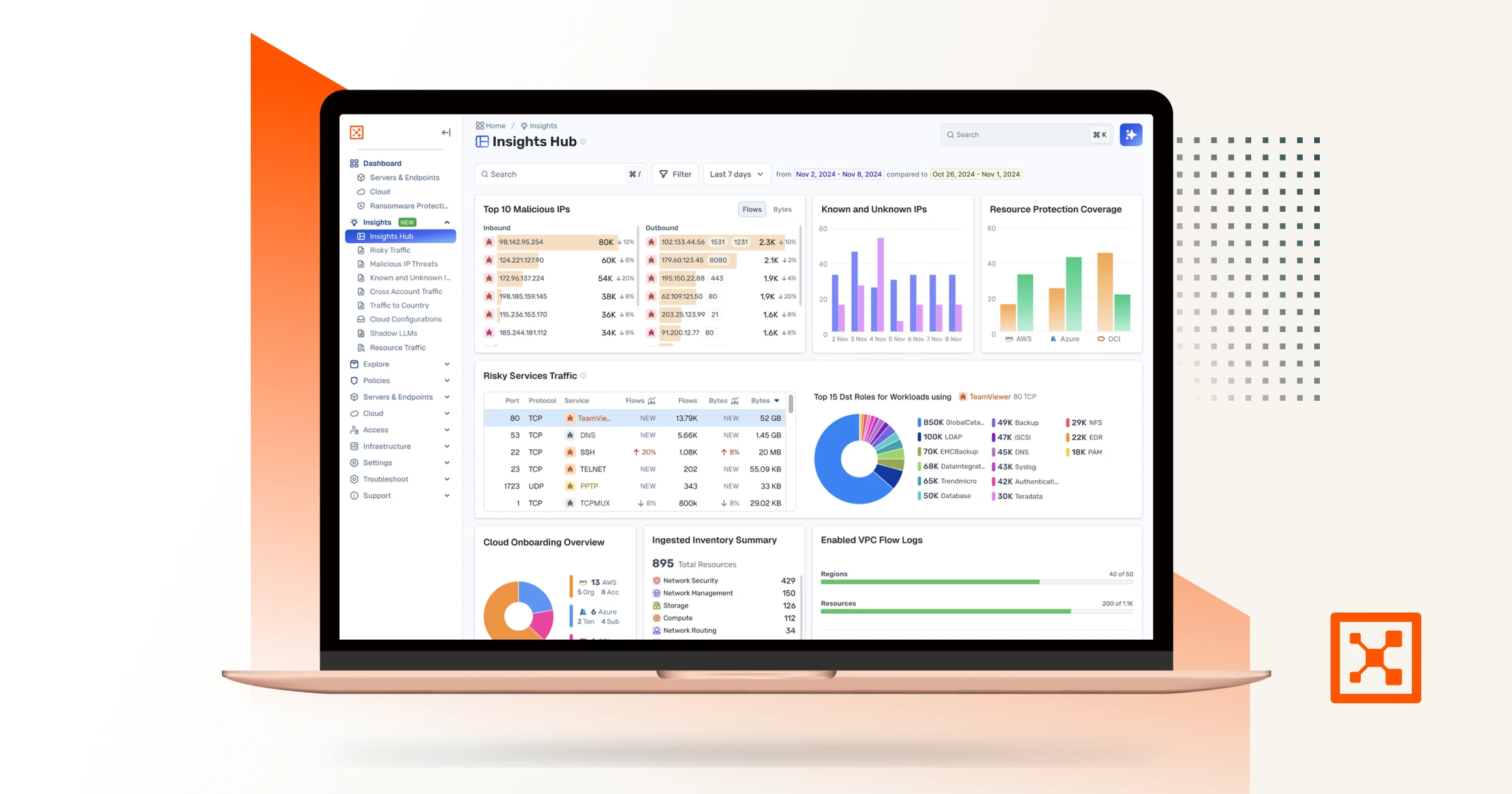







Illumio Insights
Learn about hybrid multi-cloud detection and responsesolution built on an AI-powered security graph







Getting Started with Security Graphs: A Roadmap to Resilience
How security graphs can help you detect threats faster, strengthen Zero Trust, and make better risk decisions








Illumio Insights Explainer Video
DiscoverAI-powered hybrid cloud detection and response (CDR) that identifies lateral movementrisks, detects attacks, and contains instantly across your hybrid multi-cloud –with Discover how Insights identifies lateral








The Big Book of Breaches
The year’s most devastating attacks, how they happened, and what you can do about them
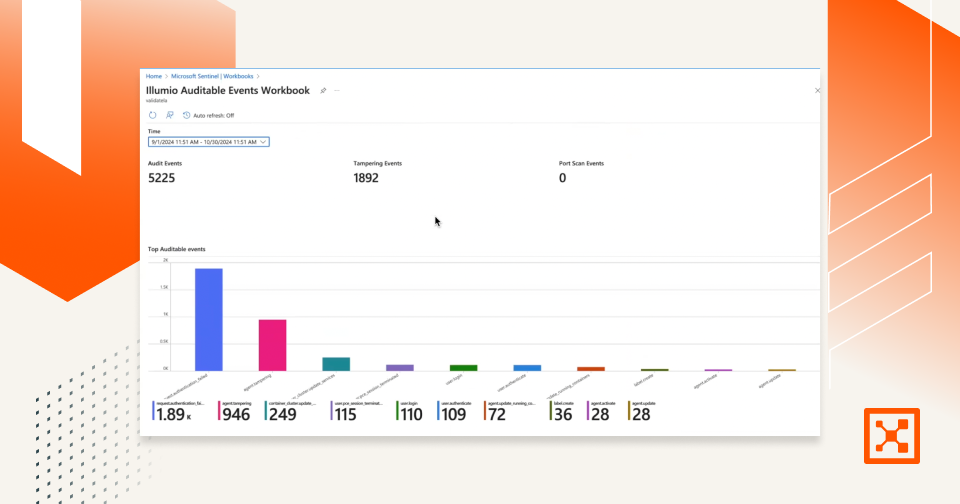







Illumio Sentinel Integration Demo
Watch how Illumio's integration with Microsoft Sentinel streamlines SecOps, strengthens compliance, and accelerates cyber incident response.








The Cloud Resilience Playbook
Learn how to combat, contain, and conquer breaches in the cloud with microsegmentation.
Assume Breach.
Minimize Impact.
Increase Resilience.
Ready to learn more about Zero Trust Segmentation?