How Illumio + Armis Secure Modern OT Environments

Organizations have spent decades investing in cybersecurity defenses.
So why do 58% of organizations hit by a cyberattack in the last year still report having to halt operations.
And why do these attacks result in 40% of organizations losing a significant amount of revenue and 35% experiencing brand damage?
For operational technology (OT) teams, in particular, these stats are existential threats.
For decades, factories, utilities, and critical infrastructure relied on air-gapped networks and perimeter security. But with digital transformation driving IT/OT convergence, those strategies no longer hold.
Legacy industrial systems now coexist with cloud platforms, IoT sensors, and virtualized gateways. The result is an attack surface that’s blown wide open.
The Illumio and Armis joint solution can help you bridge the security gap.
The Zero Trust mandate for OT security
Securing modern OT systems isn’t easy. Today's security teams are forced to:
- Migrate from air-gapped to hybrid environments
- Introduce containerized gateways and SASE architectures
- Manage IaaS and PaaS integrations
But this modernization often outpaces security investment, creating a dangerous “security transformation deficit.”
The old Purdue Model worked when industrial systems were isolated.

But in a world of containerized gateways, hybrid environments, and virtualized OT, static perimeters fall apart. The Purdue Model has since been updated to reflect modern complexity.
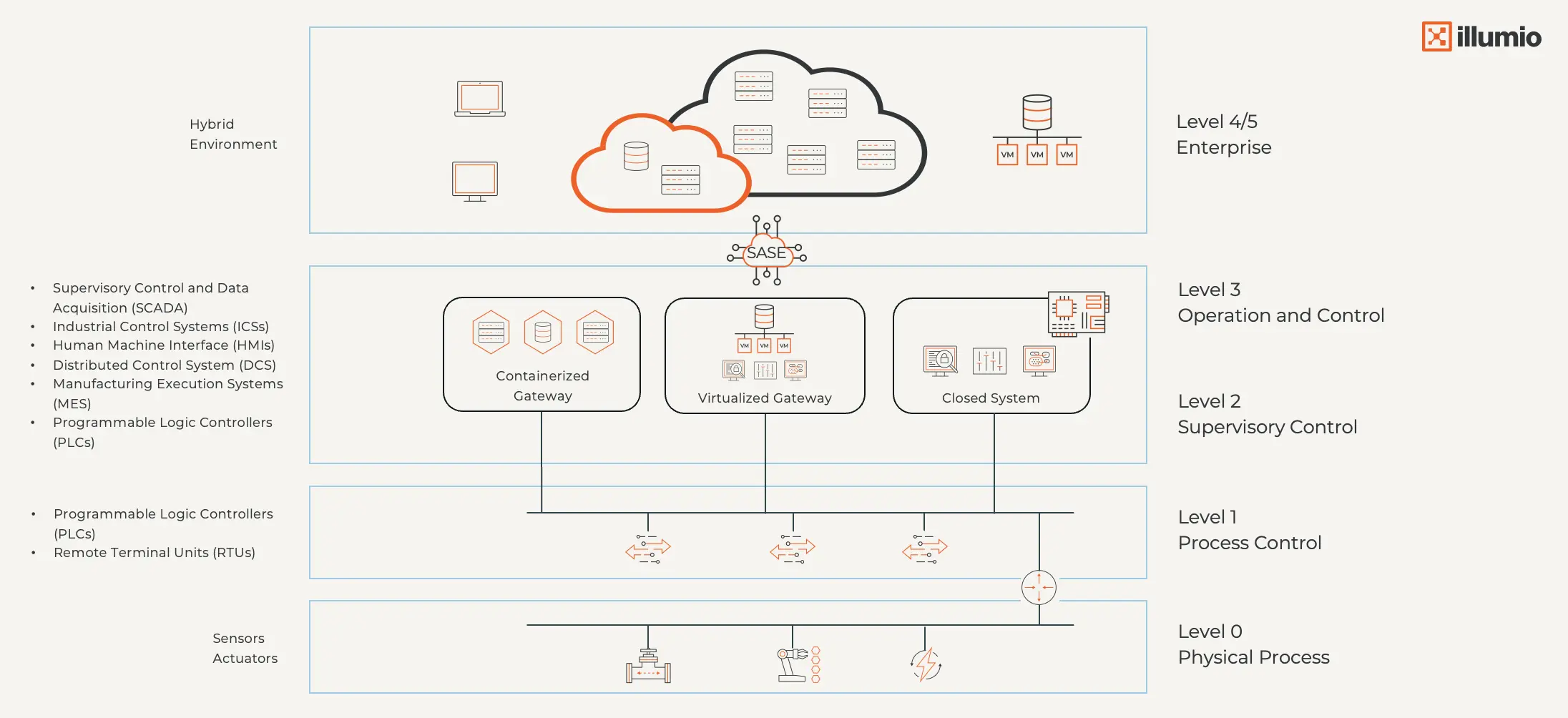
A Zero Trust strategy for OT environments is the only way forward. It continuously validates every user, device, and workload, limits access to only what’s necessary, and automatically adapts policies as environments and risks change.
Illumio + Armis: a practical path to Zero Trust in OT
Armis and Illumio are redefining what Zero Trust looks like in complex industrial environments.
Together, they combine deep asset visibility with real-time segmentation and enforcement without disrupting operations.
Armis: see and understand your IT, OT, and IoT
Armis delivers deep visibility across IT, OT, and IoT.
Its passive monitoring uncovers device type and role, network behavior and communication patterns, placement within the Purdue Model, and risk and vulnerability context.
That intelligence is the foundation for segmentation and protection.
Armis passively monitors every connected device across IT, OT, and IoT, offering unmatched visibility into:
- Device type and role
- Network behavior and communication patterns
- Layer placement within the Purdue Model
- Risk and vulnerability context
This context is essential for segmenting and protecting critical OT assets.
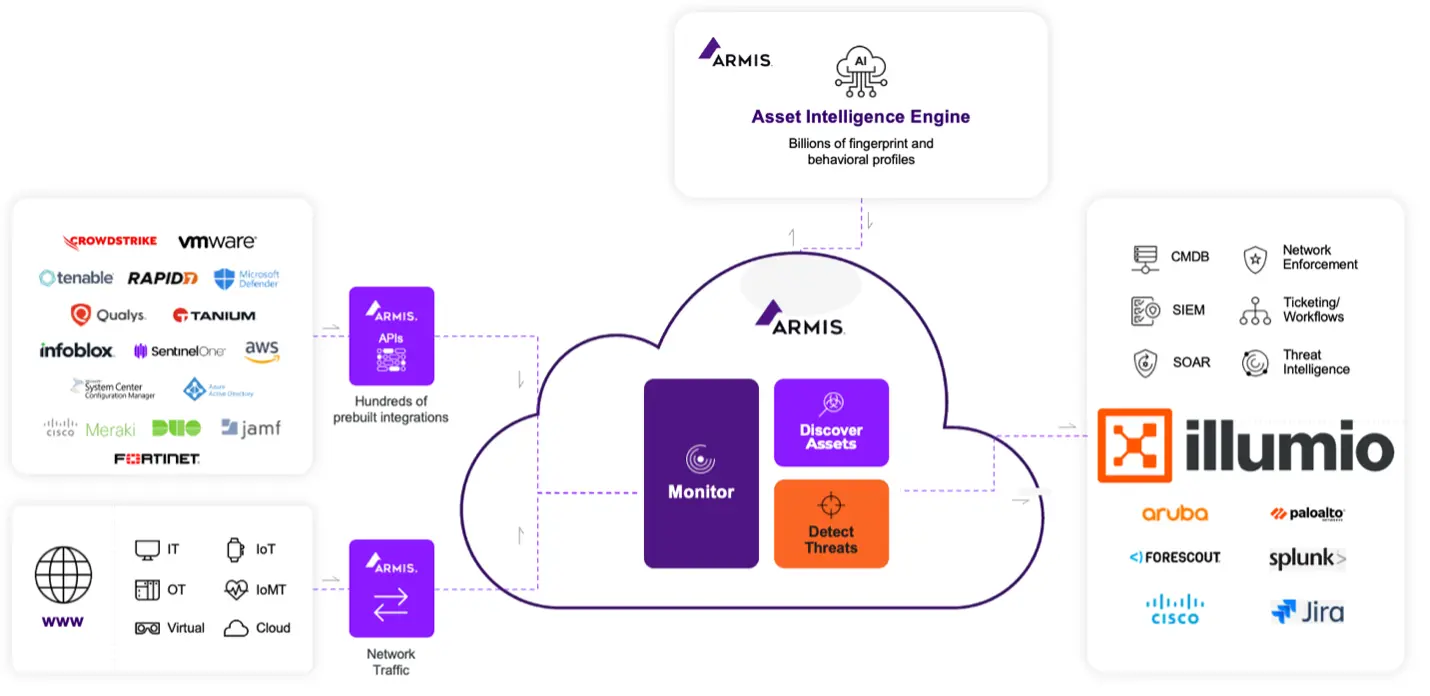
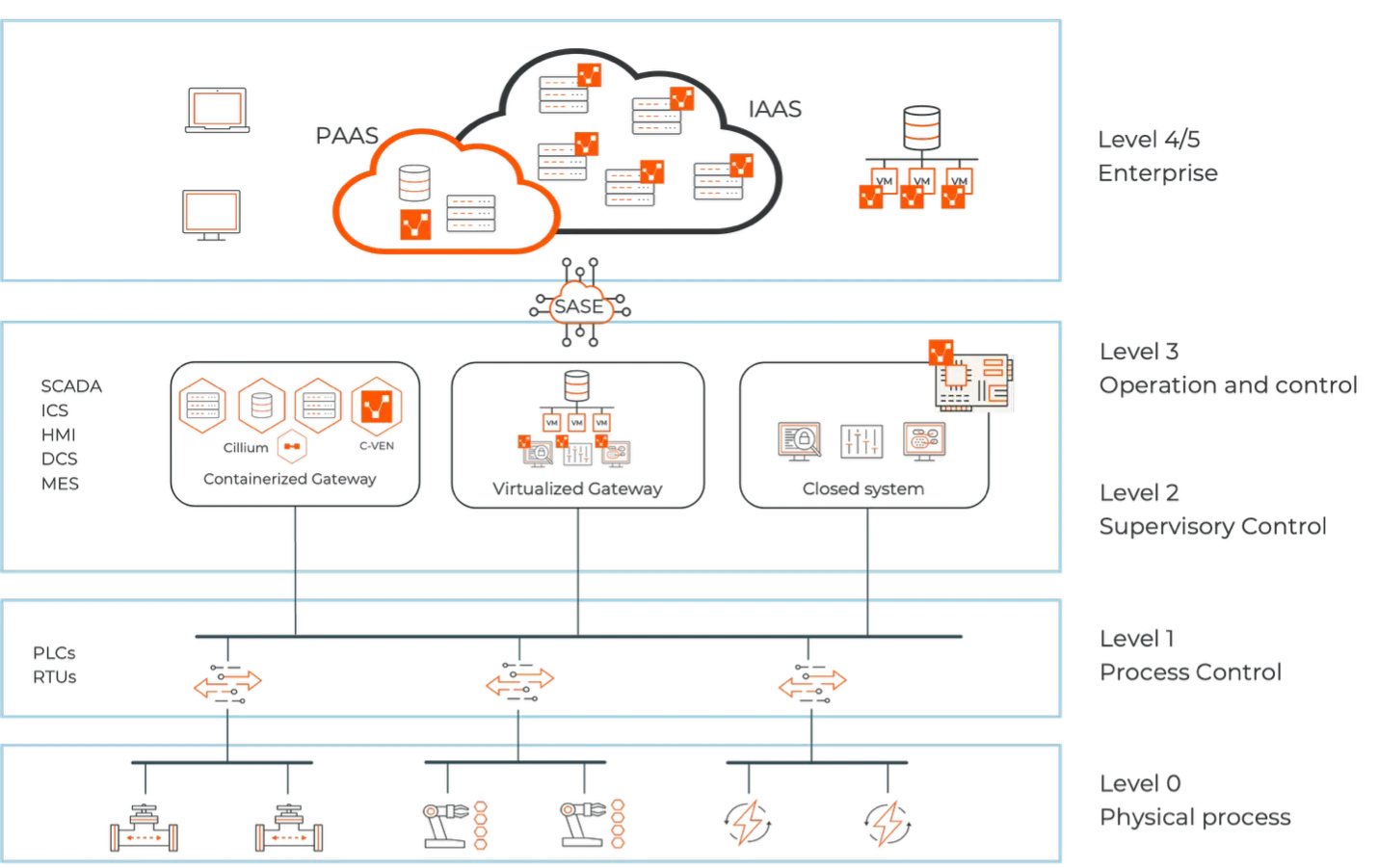
Illumio: enforce segmentation without the risk
Illumio takes the insights from Armis and applies adaptive, risk-informed segmentation policies.
This includes:
- Segmentation with the Purdue Model in mind: Lock down traffic between SCADA, DCS, MES, and ERP so every system only talks to what it should.
- Dynamic response to threats: When Armis spots something suspicious, Illumio reacts instantly, cutting access or isolating devices before threats spread.
- Agentless control: Protect fragile ICS and PLC devices without touching them. The Illumio VEN/NEN architecture enforces policies safely with no agents required.
This approach is safe, easy to scale, and will keep your operations resilient even during an active attack — even in the most tightly regulated environments.
Key benefits of the Illumio + Armis integration
The Illumio and Armis joint solution is built for the day-to-day challenges OT and security teams face.
No disruption to operations
Most security tools slow you down with agents or heavy network changes. But Illumio and Armis take a different approach.
A lightweight architecture protects critical systems without touching fragile devices such as PLCs, RTUs, or SCADA controllers.
Illumio enforces policies through its VEN/NEN model, while Armis delivers passive, agentless visibility, so you see everything and stay secure without adding risk.
Closed-loop defense that adapts in real time
Detection and enforcement can’t work in silos. They feed each other.
When Armis spots something suspicious, like odd protocol activity or a device pinging a public IP, Illumio reacts instantly by locking it down or tightening access. The result is faster responses, less dwell time, and a smaller blast radius without waiting for manual intervention.
Compliance-friendly visibility and audit trails
In highly regulated industries, visibility into your hybrid environments means survival.
The Illumio + Armis integration delivers audit-ready logs, policy simulations, and pre-change checks so teams can make updates with confidence.
Whether you’re aligning with NIST, IEC 62443, or ISO 27001, this joint solution makes compliance clearer, faster, and easier without slowing operations.
Unified security with real business value
Together, Illumio and Armis deliver outcomes that matter most: stronger defenses, smoother audits, and safer modernization.
They stop lateral movement before it spreads, cut ransomware off at the source, and simplify compliance with clear, auditable controls.
And as your OT environment evolves, whether it’s SASE, virtualized gateways, or hybrid cloud, the solution will adapt. This ensures you gain resilience without losing visibility or uptime.
You don’t have to choose between progress and protection. Illumio and Armis let you modernize with confidence, knowing your most vital systems stay consistently secure.
Closing the OT transformation gap
Cyberattacks aren’t slowing down, and OT environments are only getting more complex.
Legacy defenses — air gaps, static perimeters, and siloed tools — simply can’t keep up. Every delay in closing the “security transformation deficit” leaves critical infrastructure exposed to ransomware, downtime, and regulatory risk.
That’s why the Illumio + Armis integration matters now more than ever.
By combining deep asset visibility with real-time segmentation and enforcement, it delivers Zero Trust security that’s production-ready, compliance-friendly, and built for the realities of modern OT.
You can’t wait for the next incident to force change. With Illumio and Armis, you can build resilience today, so your organization can innovate, modernize, and grow without fear of disruption.


.webp)


.webp)

