Where breaches meet their end
Contain threats and strengthen your security posture with the world’s first and leading breach containment platform.


Stay secure, stay confident
Visualize communication and traffic across workloads, devices, and the internet. Real-time observability powered by Insights Agent — your automated AI teammate for fast risk detection and smarter response.

With every change, automatically set granular segmentation policies to control unnecessary and unwanted communications.

Proactively protect high-value assets or reactively isolate compromised systems during an active attack to stop the spread of a breach.

The Illumio difference
The only platform built for breach containment. Illumio delivers the visibility and precision needed to contain breaches at scale. Turn lateral movement into a dead end with real-time observability, instant control, and unified protection across every environment.
Illumio runs on a unified platform, easily deployed and managed through a centralized console.
Built for the cloud, Illumio offers unmatched scalability, adapting seamlessly across environments to meet your evolving needs.
Illumio provides real-time observability, with the agility to scale effortlessly, ensuring operational efficiency without compromise.
The Illumio advantage
Simplifying and accelerating risk identification, assessment, and containment
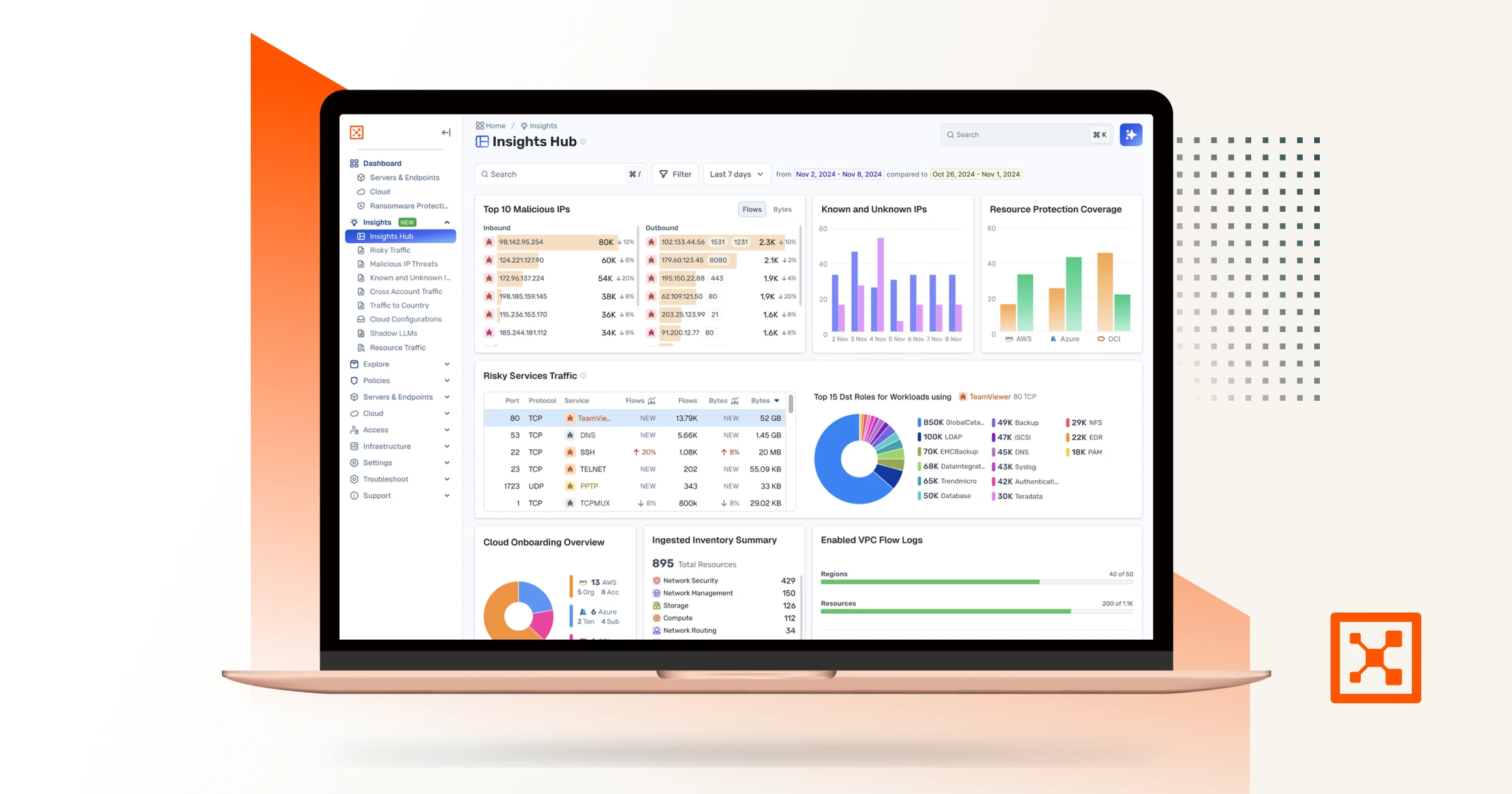
An AI security graph built for the way attackers think
Our AI security graph mirrors how attackers exploit modern environments, mapping every connection to reveal risks, monitor behavior, and enforce policies at scale. It’s powered by AI and enriched with third-party data for deep, real-time observability.
Illumio Insights
Identify lateral movement, detect attacks, and stop breaches instantly at cloud scale. Now with Insights Agent, your AI teammate for role-based threat detection and response. Prioritize and stop critical threats with context-rich analysis, deep observability, and one-click containment.
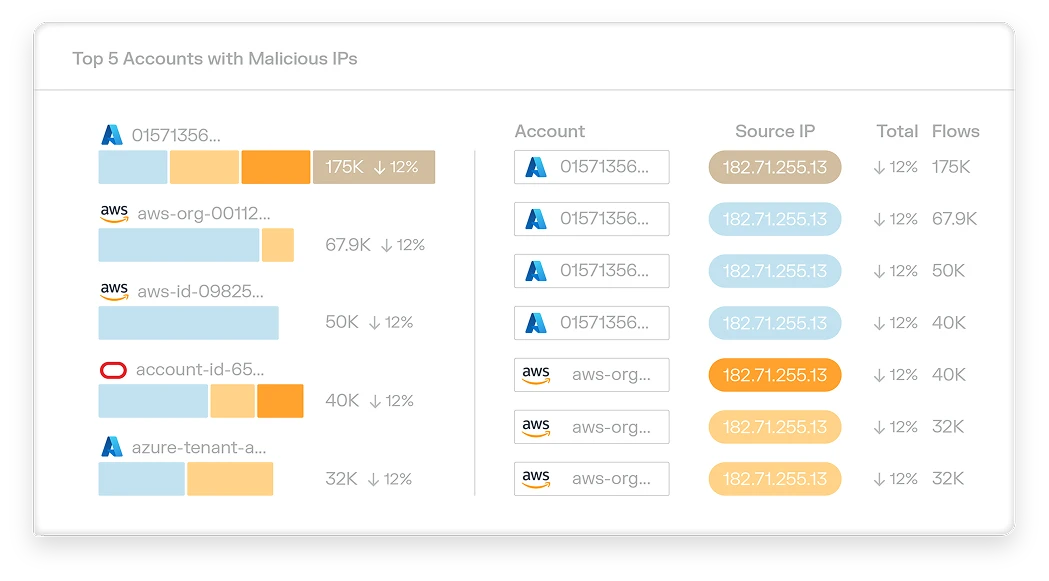
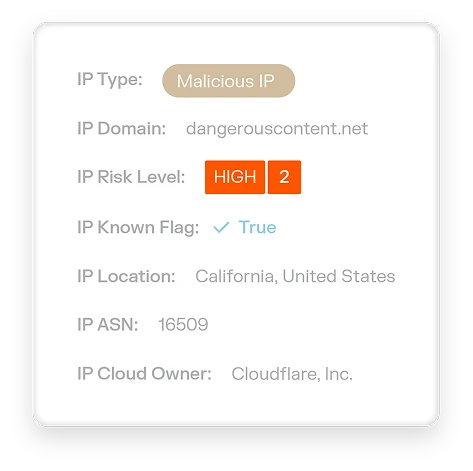


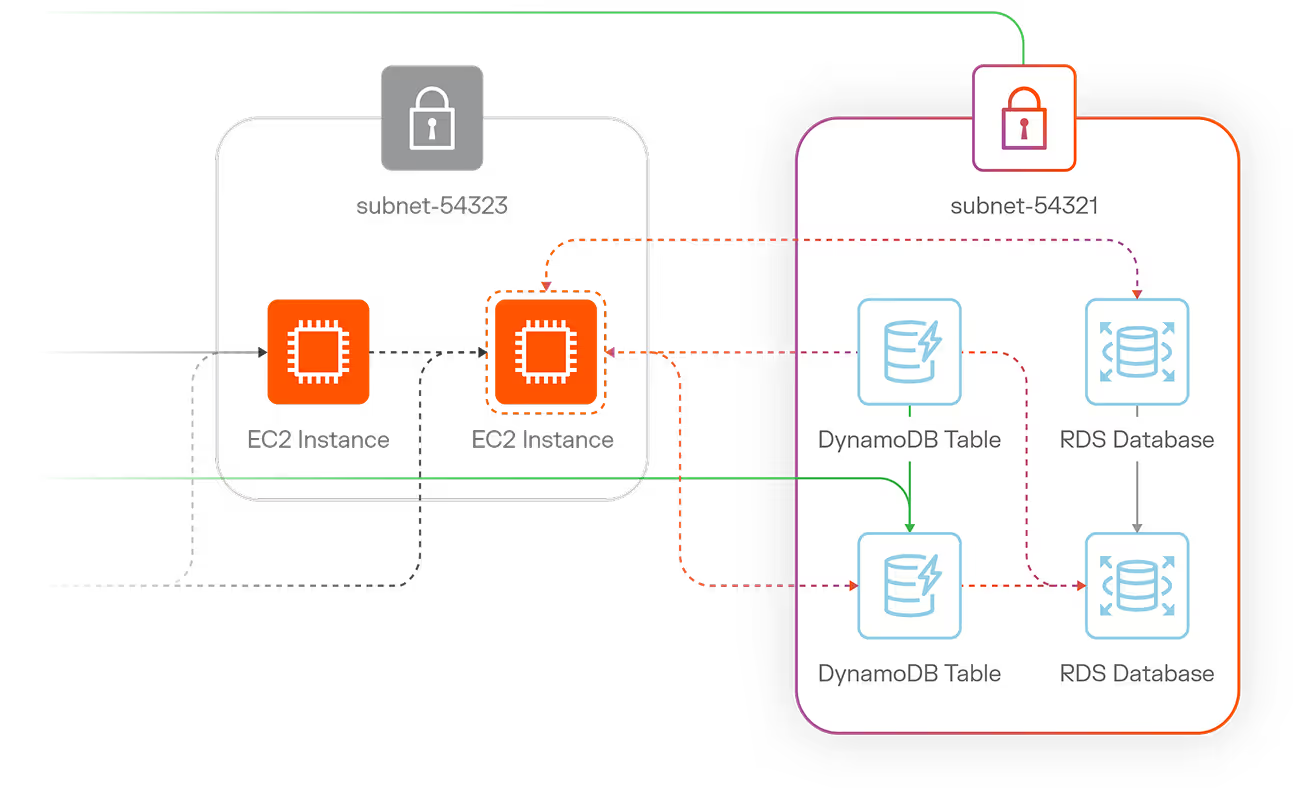
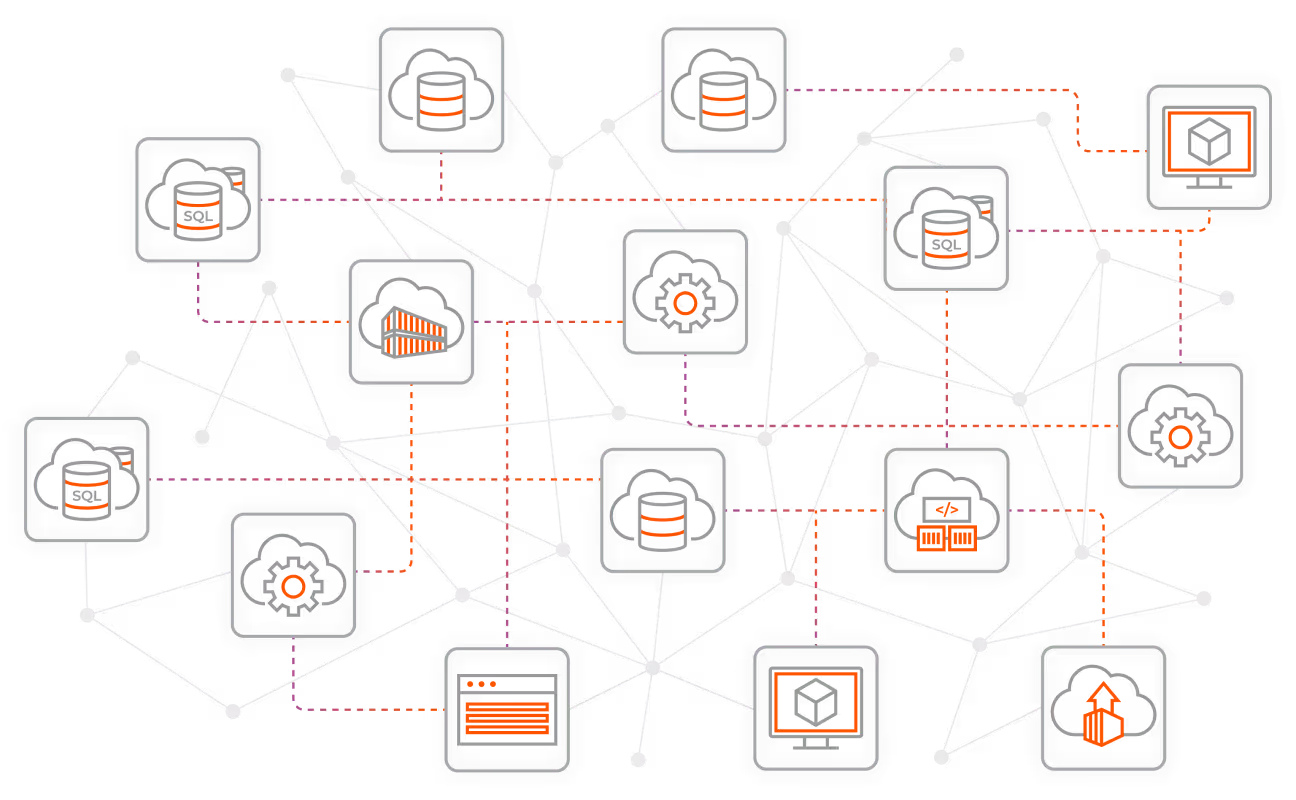
Illumio Segmentation
Stop breaches and ransomware. Visualize communication between workloads and devices and create segmentation policies that allow only trusted interactions across all environments — endpoints, servers, cloud, and containers.

Proven, scalable security for the modern enterprise
Deployed across organizations of all sizes and industries globally, Illumio delivers unmatched performance and security at any scale.
average savings in downtime among early adopters of microsegmentation
Illumio stopped ransomware in 10 minutes versus 2.5 hours with an EDR tool alone
composite return, per the Forrester Total Economic Impact™ study of Illumio

How eBay segmented 3,000 servers and never broke an app with Illumio