Illumio Solutions
Zero Trust Segmentation is the fundamental building block of any security strategy


Zero Trust Segmentation is the fundamental building block of any security strategy
Being able to map all of your connections and apply a least privilege model to control the flow of traffic drastically improves your security posture.
It’s relevant to the success of key strategic cyber initiatives, enables a multitude of common use cases and is foundational to achieving the security goals across a range of industries.
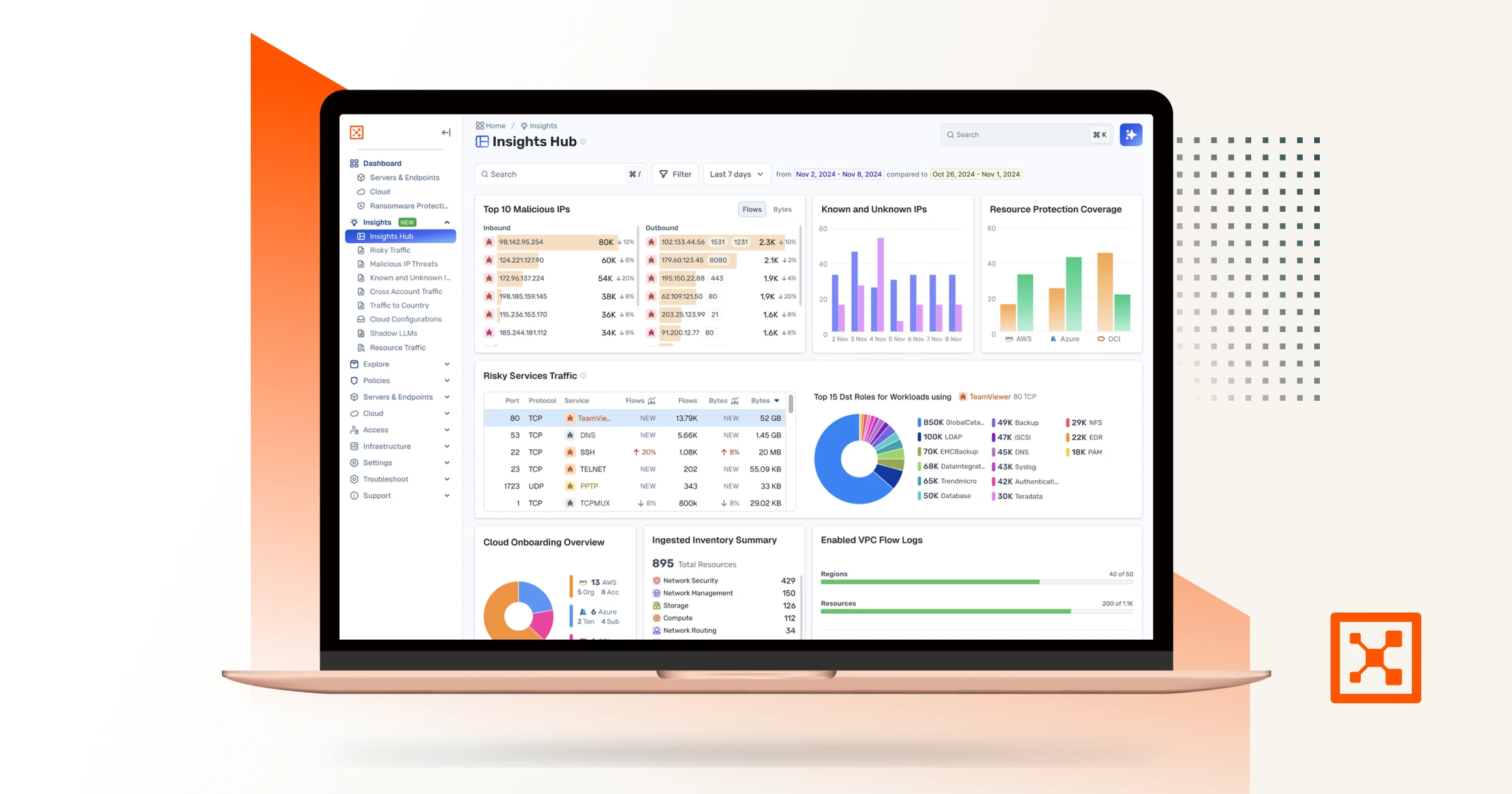
See how Illumio supports essential cyber programs
See how Illumio supports essential cyber programs
Asset Mapping & Visibility
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
IT/OT Convergence
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Protection Strategies
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Ransomware
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.
Adapting to your needs
Accommodate your project methodologies, such as traditional waterfall, agile, hybrid, or predictive models, aligned to deliver your desired results.

.svg)
Every industry benefits from Zero Trust Segmentation
Microsoft deploys Illumio across its entire corporate IT environment