Vulnerability Management in Cybersecurity: A Complete Guide for Organizations
Vulnerability management can exist in software, hardware, network configurations, or third-party dependencies. Discover why this continuous process can make the difference between a secure enterprise and a catastrophic breach in our complete guide.
Introduction
In today's digital landscape, organizations face an ever-evolving array of cyber threats. From sophisticated ransomware attacks to zero-day vulnerabilities, the need for robust cybersecurity measures has never been more critical. At the heart of these measures lies vulnerability management, a proactive approach to identifying, assessing, and mitigating security weaknesses before they can be exploited.
What is Vulnerability Management?
Vulnerability management is a continuous, proactive, and often automated process that identifies, evaluates, treats, and reports on security vulnerabilities in systems and software. Unlike one-time assessments, it is an ongoing cycle that ensures organizations stay ahead of potential threats.
This process is integral to an organization's overall security strategy, aiming to reduce the attack surface and prevent potential breaches. By systematically identifying and addressing vulnerabilities, organizations can maintain the integrity, confidentiality, and availability of their systems and data.
Key Components of Vulnerability Management
- Discovery: Identifying all assets within the organization's environment, including hardware, software, and network components. This comprehensive inventory is crucial for understanding the scope of potential vulnerabilities.
- Assessment: Evaluating identified assets for known vulnerabilities using tools like vulnerability scanners. This step involves analyzing the severity and potential impact of each vulnerability.
- Prioritization: Determining which vulnerabilities to address first based on risk factors such as exploitability, potential impact, and the criticality of affected assets. This risk-based approach ensures efficient allocation of resources.
- Remediation: Applying fixes or mitigations to eliminate or reduce vulnerabilities. This may involve patching software, reconfiguring systems, or implementing compensating controls.
- Reporting: Documenting findings and actions taken to address vulnerabilities. Reporting provides visibility into the organization's security posture and supports compliance efforts.
It's essential to distinguish between vulnerability management and vulnerability assessment. While assessments are periodic evaluations that provide a snapshot of vulnerabilities at a given time, vulnerability management is a continuous, comprehensive strategy that encompasses the entire lifecycle of vulnerability identification and mitigation.
Why is Vulnerability Management Important?
Implementing a robust vulnerability management program offers numerous benefits that are critical to an organization's cybersecurity posture and overall operational success.
1. Risk Reduction
By proactively identifying and addressing vulnerabilities, organizations can minimize their attack surface, making it more difficult for threat actors to exploit weaknesses. This proactive approach significantly reduces the likelihood of successful cyberattacks.
2. Compliance
Many regulatory frameworks and industry standards, such as GDPR, HIPAA, and PCI DSS, mandate regular vulnerability assessments and timely remediation. A structured vulnerability management program ensures adherence to these requirements, avoiding potential legal and financial penalties.
3. Operational Continuity
Unaddressed vulnerabilities can lead to system outages, data breaches, and other disruptions. By managing vulnerabilities effectively, organizations maintain the integrity and availability of their systems, ensuring uninterrupted business operations.
4. Cost Savings
The cost of a data breach can be substantial, encompassing not only immediate financial losses but also long-term reputational damage. Investing in vulnerability management helps prevent such incidents, resulting in significant cost savings over time.
5. Enhanced Security Posture
A comprehensive vulnerability management program contributes to a stronger overall security posture. It enables organizations to stay ahead of emerging threats, adapt to evolving attack vectors, and build resilience against potential cyber incidents.
By proactively addressing vulnerabilities, organizations can safeguard their assets, reputation, and bottom line, ensuring long-term success in an increasingly complex cybersecurity landscape.
The Vulnerability Management Lifecycle
An effective vulnerability management program follows a structured lifecycle:
1. Asset Discovery and Inventory
Maintaining an up-to-date inventory of all assets is crucial. Automated tools can assist in identifying hardware, software, and network components, ensuring comprehensive coverage.
2. Vulnerability Scanning and Identification
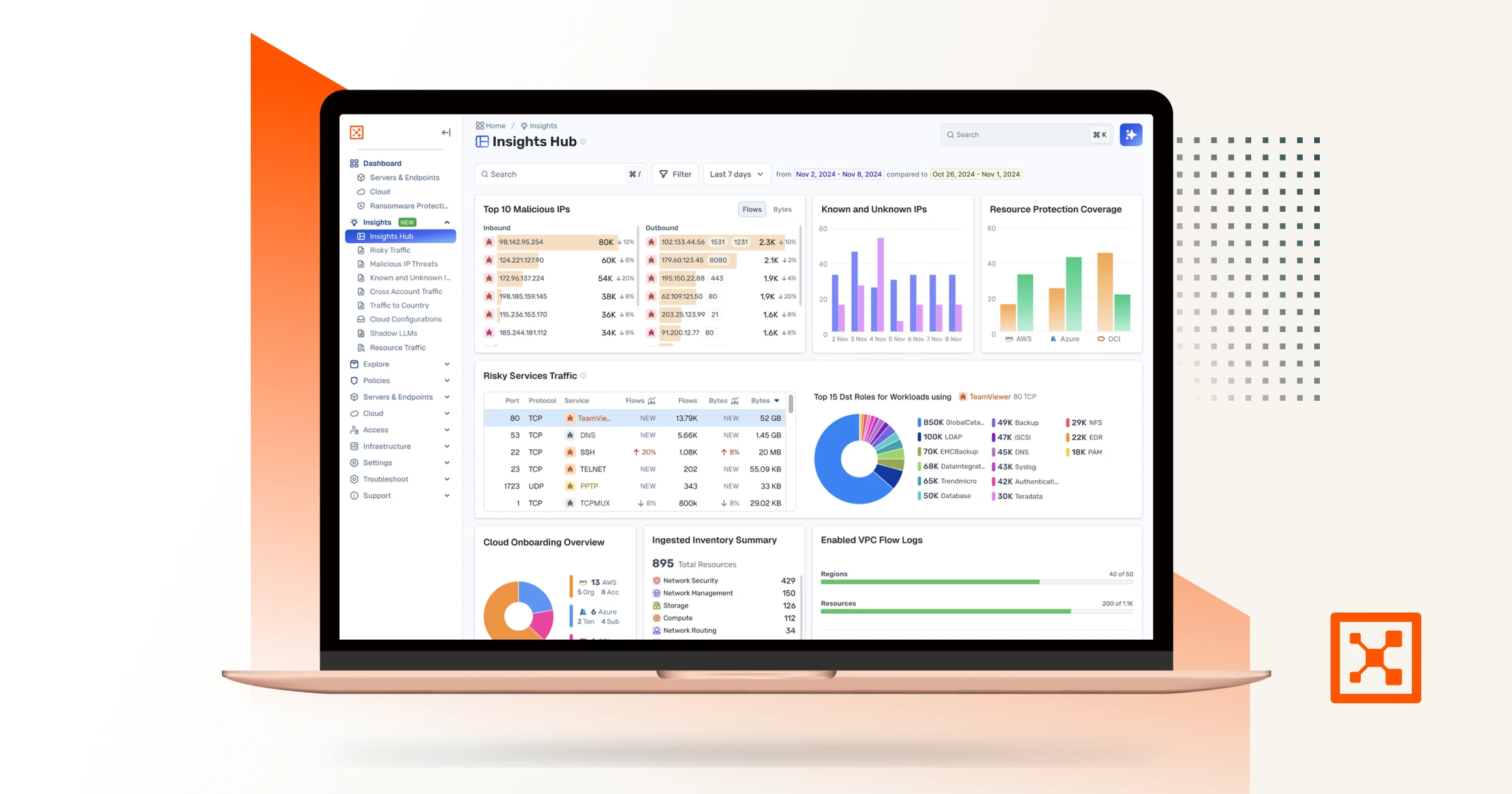
Utilize scanners to detect vulnerabilities. Integrating these tools with Illumio's real-time maps enhances visibility and context.
3. Risk Assessment and Prioritization
Leverage CVSS scores and business context to evaluate risks. Illumio's Vulnerability Exposure Score (VES) provides contextual prioritization, focusing on vulnerabilities that pose the greatest threat.
4. Remediation and Mitigation
Apply patches and updates promptly. When immediate remediation isn't possible, implement compensating controls like micro-segmentation to contain potential threats.
5. Verification and Monitoring
Continuously monitor systems to ensure vulnerabilities are addressed effectively. Illumio's tools facilitate ongoing assessment and validation.
6. Reporting and Compliance
Document actions taken and generate reports for stakeholders and auditors, demonstrating compliance and informing future strategies.
Challenges in Vulnerability Management
In today's rapidly evolving digital landscape, organizations face numerous challenges in effectively managing vulnerabilities. Understanding these obstacles is crucial for developing a robust vulnerability management strategy.
1. Volume of Vulnerabilities
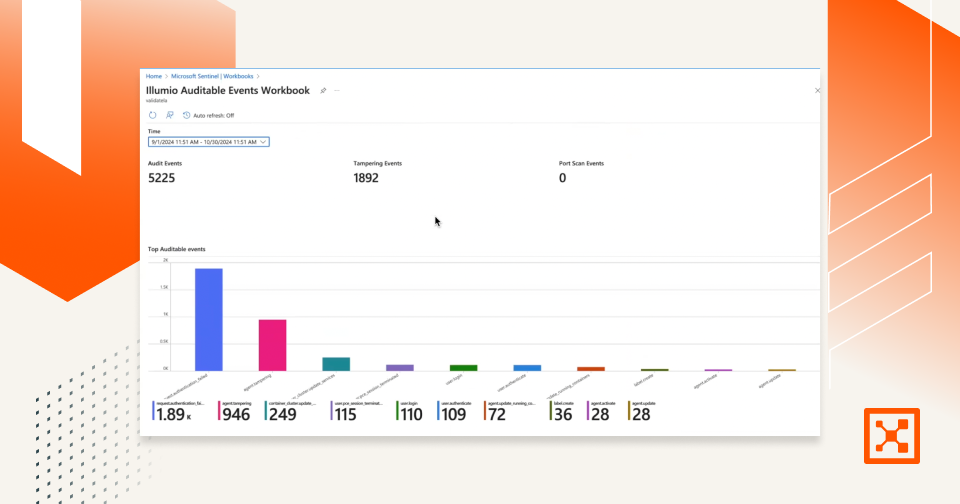
The sheer number of vulnerabilities discovered daily can be overwhelming. According to an IBM study, organizations with over 1,000 employees identify an average of 779,935 vulnerabilities during scans, with approximately 28% remaining unmitigated over six months . This volume makes it challenging to prioritize and address each vulnerability promptly.
Illumio's Solution: Illumio's Vulnerability Maps provide a visual representation of vulnerabilities in the context of application dependencies, helping organizations focus on the most critical issues first.
2. Resource Constraints
Many organizations operate with limited cybersecurity personnel and budgets, making it difficult to address all identified vulnerabilities. This scarcity of resources can lead to delays in patching and remediation efforts.
Illumio's Solution: By integrating with existing vulnerability scanners and providing contextual risk assessments, Illumio enables security teams to prioritize remediation efforts effectively, optimizing the use of available resources.
3. Complex Environments
Modern IT infrastructures often encompass hybrid and multi-cloud environments, along with a mix of legacy systems and modern applications. This complexity can hinder comprehensive vulnerability assessments and remediation efforts.
Illumio's Solution: Illumio's platform offers real-time visibility across diverse environments, facilitating consistent vulnerability management practices regardless of infrastructure complexity.
4. Delayed Patching
Timely patching is essential to mitigate vulnerabilities, yet organizations often face challenges in deploying patches promptly. Factors such as potential downtime, compatibility issues, and coordination among teams can contribute to delays .
Illumio's Solution: Illumio's breach containment and microsegmentation allows organizations to implement compensating controls, reducing the risk associated with delayed patching by limiting the potential spread of threats.
5. Siloed Operations
In many enterprises, security operations are fragmented across different teams and tools, leading to disjointed visibility and response efforts. This siloed approach can result in critical vulnerabilities being overlooked or inadequately addressed.
Illumio's Solution: By providing a unified platform that integrates with various security tools, Illumio fosters collaboration among teams, ensuring a cohesive approach to vulnerability management.
Illumio's Approach to Vulnerability Management
Illumio offers a unique perspective on vulnerability management, focusing on real-time visibility and breach containment and microsegmentation.
Breach Containment and Microsegmentation
By controlling communication between workloads, breach containment and microsegmentation limits the spread of breaches and enhances overall security.
Vulnerability Maps
Illumio's Vulnerability Maps combine data from scanners with application dependency maps, providing insights into potential attack paths and exposure.
Vulnerability Exposure Score (VES)
VES calculates risk based on severity and exposure, enabling organizations to prioritize remediation efforts effectively.
Integration with Third-Party Tools
Seamless integration with platforms ensures comprehensive coverage and streamlined workflows.
Implementing an Effective Vulnerability Management Program
Establishing a robust vulnerability management program is crucial for organizations aiming to proactively identify, assess, and remediate security vulnerabilities. The following structured approach outlines key steps and best practices to build and maintain an effective program.
1. Develop Comprehensive Policies and Procedures
Begin by formulating clear, well-documented policies that define the scope, objectives, and processes of your vulnerability management program. These policies should outline:
- Roles and Responsibilities: Assign specific tasks to IT, security teams, and other stakeholders.
- Assessment Frequency: Determine how often vulnerability scans and assessments will occur.
- Remediation Timelines: Set deadlines for addressing identified vulnerabilities based on their severity.
- Exception Handling: Establish procedures for managing vulnerabilities that cannot be immediately remediated.
Having structured policies ensures consistency, accountability, and compliance with regulatory requirements.
2. Foster Cross-Functional Collaboration
Effective vulnerability management requires collaboration across various departments:
- Executive Leadership: Provides strategic direction and allocates necessary resources.
- IT and Security Teams: Conduct assessments, implement remediations, and monitor systems.
- Development Teams: Address vulnerabilities in applications and codebases.
- Compliance Officers: Ensure adherence to industry standards and regulations.
Regular communication and coordination among these groups facilitate timely and effective vulnerability mitigation.
3. Implement Continuous Improvement Processes
Vulnerability management is an ongoing process that should evolve with emerging threats and organizational changes. To ensure continuous improvement:
- Regular Reviews: Periodically assess the effectiveness of your vulnerability management strategies.
- Feedback Loops: Incorporate lessons learned from past incidents to refine processes.
- Stay Informed: Keep abreast of new vulnerabilities, threat landscapes, and best practices.
Continuous improvement enhances the resilience and adaptability of your security posture.
4. Invest in Training and Awareness Programs
Human error remains a significant factor in security breaches. Educating employees about cybersecurity best practices is essential:
- Security Awareness Training: Conduct regular sessions to inform staff about common threats like phishing and social engineering.
- Role-Specific Training: Provide targeted training for teams directly involved in vulnerability management.
- Policy Familiarization: Ensure all employees understand the organization's security policies and their responsibilities.
A well-informed workforce acts as a crucial line of defense against potential security incidents.
Real-World Use Cases
Case Study: Overland Footwear
- Challenge: Securing a network with numerous third-party devices.
- Solution: Implemented Illumio's breach containment and microsegmentation.
- Outcome: Achieved enhanced visibility and reduced vulnerability risks.
Case Study: Large Insurance Company
- Challenge: Managing thousands of exploitable vulnerabilities.
- Solution: Utilized Illumio's vulnerability maps and segmentation.
- Outcome: Reduced vulnerabilities from 5,000 to 9 across critical applications.
Best Practices for Vulnerability Management
- Regular Scanning: Schedule frequent scans to identify new vulnerabilities.
- Prioritize Based on Risk: Focus on vulnerabilities that pose the greatest threat.
- Implement Compensating Controls: Use microsegmentation when patches aren't immediately available.
- Maintain Comprehensive Documentation: Keep detailed records of vulnerabilities and remediation efforts.
- Stay Informed: Keep up-to-date with the latest threats and vulnerability disclosures.
Conclusion
Effective vulnerability management is essential for protecting organizations against cyber threats. By understanding the vulnerability management lifecycle, addressing challenges, and implementing best practices, organizations can enhance their security posture. Illumio's innovative solutions, including breach containment, microsegmentation, and Vulnerability Maps, provide the tools necessary to manage vulnerabilities proactively and efficiently.
Frequently Asked Questions (FAQs)
1. What is vulnerability management?
Vulnerability management is the continuous process of identifying, assessing, and mitigating security vulnerabilities in systems and software.
2. Why is vulnerability management important?
It reduces the risk of cyberattacks, ensures compliance with regulations, maintains operational continuity, and saves costs associated with data breaches.
3. How does Illumio enhance vulnerability management?
Illumio offers real-time visibility, breach containment, microsegmentation, and Vulnerability Maps to identify and mitigate vulnerabilities effectively.
4. What is the Vulnerability Exposure Score (VES)?
VES is a metric provided by Illumio that calculates risk based on severity and exposure, helping prioritize remediation efforts.
5. How often should vulnerability scans be conducted?
Regular scans, such as weekly or monthly, are recommended, with more frequent scans for critical systems.
6. What challenges are associated with vulnerability management?
Challenges include managing a high volume of vulnerabilities, resource constraints, complex environments, and delayed patching.
7. What is breach containment and microsegmentation?
It's a security approach that limits the spread of breaches by controlling communication between workloads.
8. How do vulnerability maps work?
They combine data from scanners with application dependency maps to visualize potential attack paths and exposure.
9. Can Illumio integrate with existing vulnerability scanners?
Yes, Illumio seamlessly integrates with vulnerability scanner platforms.
10. What are best practices for vulnerability management?
Regular scanning, risk-based prioritization, implementing compensating controls, maintaining documentation, and staying informed about new threats.
.png)
%20(1).webp)

%20(1).webp)
.webp)