Prove It or Lose It: Why CISOs Must Bring Data to the Boardroom
The CISO’s Playbook is an ongoing series featuring strategic insight from the industry’s top cybersecurity executives. This post features Bryan Liebert, Field CISO at World Wide Technology (WWT).
The role of the CISO is changing fast.
Boards want proof. Insurers want data. Charisma, gut instinct, and experience aren't enough anymore.
It’s time for CISOs to pair their wisdom and experience with science and cold, hard facts. They need to demonstrate how security decisions mitigate risk, safeguard revenue, and align with business goals using real data.
The good news is that you’re not in it alone. World Wide Technology (WWT) Field CISO Bryan Liebert says that getting data on your network’s security and risk level is possible.
Proof over politics: the CISO’s new reality
When Liebert recently built his new house, he was surprised by changes to the home inspection process.
“In the past, inspectors relied on their experience, gut instinct, and construction knowledge to sign off on new builds,” he explained.
But that’s not how it works anymore.
“Today’s inspectors might still know the construction is done right,” he said, “but they want a letter from an engineer to prove it.” Engineering letters give inspectors the documentation and data they need to back up their decision to give the home a passing grade.
That change stuck with Bryan. As a former CISO and current CISO advisor, he sees the same transformation happening in cybersecurity. Gut instinct and years of experience aren’t enough.
Boards and insurers aren’t just asking for opinions — they want the CISO’s wisdom, experience, and leadership to be augmented by a framework substantiating their recommendations' . They want their own engineering letter.
Bryan is helping WWT’s customers lead the charge with a data-driven approach that lets organizations bridge the boardroom, insurance providers, and business goals.
He’s working alongside partners like Illumio to help CISOs move from cyber storytellers to decision scientists.
Why cybersecurity needs a scientific makeover
From Bryan’s perspective, the CISO’s job has become as much about the CISO's ability to influence decision-makers as it is about protection.
“Their spending too much time firefighting and trying to convince decision-makers to invest in their strategies,” he said. “Without defensible models measuring their enterprise risk, they often have to rely on their charisma to gain board support for security expenditures.”
Bryan believes this approach is no longer sustainable.
That’s why he’s so passionate about a different path: Factor Analysis of Information Risk (FAIR). It’s a quantitative risk management framework pioneered by the FAIR Institute that translates information risk into measurable, and repeatable terms.
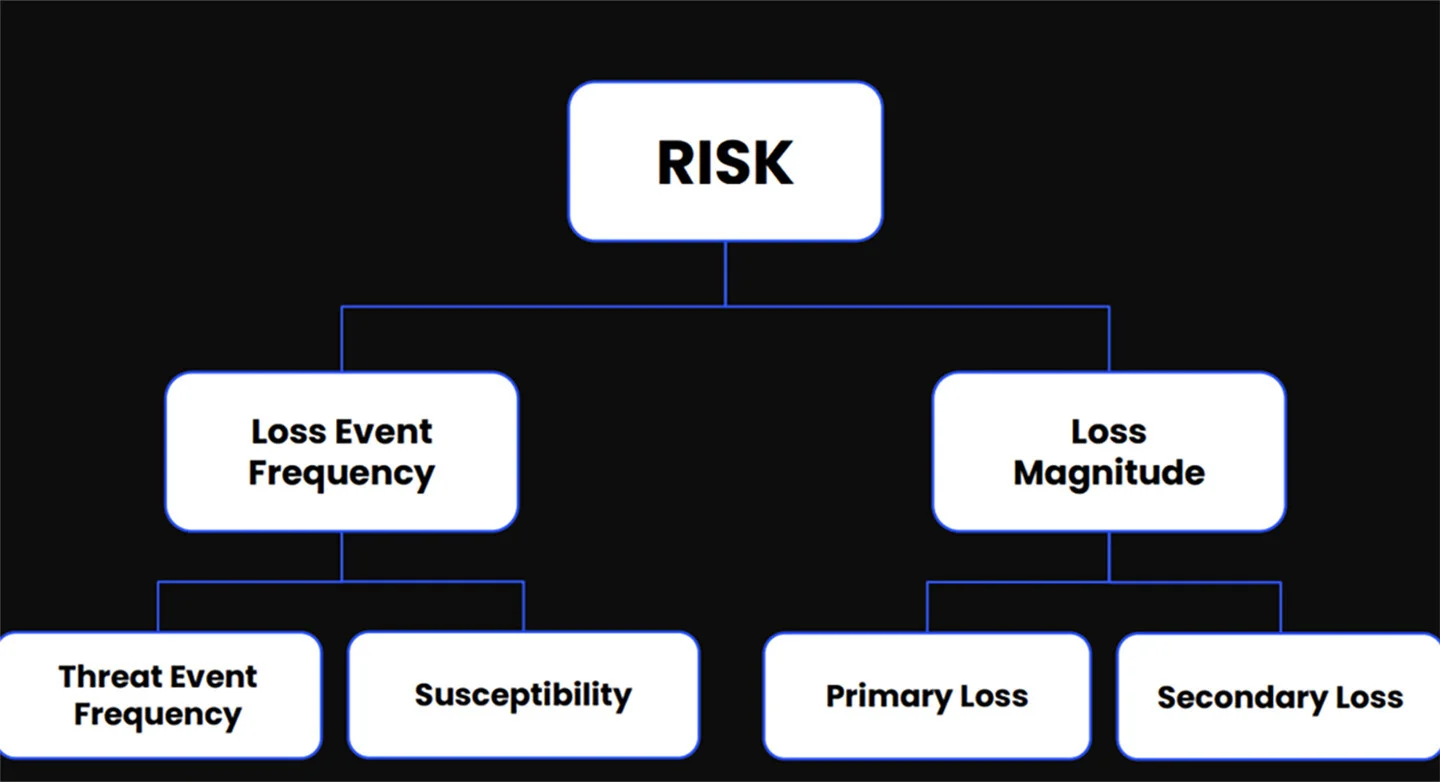
“It gives you a scientific way to calculate the traditional likelihood and impact of risk,” Bryan explained. “In fact, cyber insurers are now using it to assess coverage.”
The goal of FAIR is to empower CISOs to enter a boardroom with confidence and outline a strategy that is based on this model.
From “just trust me” to “here’s the math”
Bryan believes the modern CISO needs a decision engine — a way to translate technical security goals into business objectives that boards understand.
That means turning cybersecurity into something that can be measured, prioritized, and optimized, just like any other part of the business.
“Boards don’t care about the technical stuff,” Bryan said. “They care about risk to the business. If you can show them a ‘what-if’ analysis that says, ‘If this system is compromised, here’s the financial impact,’ you’re speaking their language.”
It’s not just about initial buy-in. Bryan wants CISOs to return with measurable statistics that demonstrate how their security investments significantly reduced risks related to profitable business objectives.
“This is the engineering letter moment,” Bryan said. “You don’t just say you have reduced risk. You show them the math.”
Boards don’t care about the technical stuff. They care about risk to the business. If you can show them a ‘what-if’ analysis that says, ‘If this system is compromised, here’s the financial impact,’ you’re speaking their language.
How cyber insurance is changing the game
Cyber insurance also plays a role in this new shift. In the past, it might’ve been simply a checkbox, but it’s now reshaping how CISOs prove value.
“When cyber insurance first showed up, no one had an open model to quantify risk,” Bryan said. “Now, they’re asking for real proof. And if you can give them a defensible formula, you can get discounts — real money on the table.”
That kind of incentive is exactly what CISOs need to push their programs forward.
“You’re not just asking for budget anymore,” Bryan said. “You’re showing that your security posture is provably able to protect the company's business objectives. That’s the kind of ROI boards care about.”
The CISO as a translator, not just a technologist
One of the biggest challenges Bryan sees today is that most cyber programs are still talking past the business instead of aligning with it.
That’s a problem, especially in sectors like higher education or healthcare where the board’s primary goal isn’t cybersecurity but instead research, student success, or patient care.
Cybersecurity is a necessary part of corporate responsibility, but irrelevant to universities without students or hospitals without patients.
“Your job is to demonstrate the role cybersecurity plays in protecting and maintaining uptime for systems that contribute to student success and happy patients,” Bryan explained. “You want them to return and recommend your services because they felt like their privacy was protected and they were safe, secure, and had a good experience with all systems they encountered.”
That’s where vendors like Illumio — and partners like WWT — come in.
How Illumio and WWT help make risk real
For Bryan, the power of partnerships comes down to one thing: proof.
“We bring organizations to WWT’s Advanced Technology Center (ATC) and show them side by side: here’s what the tech does, and here’s how the formula reduces risk,” Bryan said. “Our AI Proving Ground lets them see it in action with the latest AI advancements that are now being incorporated into virtually all cybersecurity products and strategies.”
Bryan also noted that cybersecurity vendors like Illumio are taking security math seriously. With tools like Illumio Insights, they’re helping security teams see, understand, and prioritize risk based on data — not guesswork.
With partners like WWT and Illumio, CISOs have the tools and resources they need to demonstrate value, prioritize risk, and support every decision with data.
Want to see what data Illumio Insights can uncover in your network? Start your free trial today.
.png)
.webp)