Role-Based Access Control (RBAC): A Complete Guide for Organizations
Role-Based Access Control (RBAC) is a foundational security model that restricts system access to authorized users based on their roles within an organization. Read more about RBAC in our complete guide and use our tips to enhance your organization's security and stay compliant with regulatory standards.
What is Role-Based Access Control?
RBAC is a method of regulating access to computer or network resources based on the roles of individual users within an enterprise. In RBAC, permissions are not assigned directly to users but are instead assigned to roles, and users are assigned to these roles.
This approach streamlines the management of user permissions and ensures that individuals have access only to the information and resources necessary for their job functions.
Why RBAC is Important
Risk Reduction: By enforcing the principle of least privilege, RBAC minimizes the potential for insider threats and accidental data exposure.
Compliance: RBAC supports compliance with various regulations such as GDPR, HIPAA, SOX, and ISO/IEC 27001 by providing clear access controls and audit trails.
Scalability: RBAC simplifies the management of permissions in large organizations by grouping users into roles, making it easier to manage access as the organization grows.
Operational Efficiency: Automating access control through RBAC reduces the administrative burden on IT departments and ensures consistent enforcement of security policies.
Key Benefits of Implementing RBAC
- Enhanced Security Posture: Limits access to sensitive information, reducing the risk of data breaches.
- Improved Audit and Compliance Tracking: Provides clear records of who has access to what, facilitating audits.
- Easier Onboarding/Offboarding: Simplifies the process of granting and revoking access as employees join or leave the organization.
- Least Privilege Enforcement: Ensures users have only the access necessary for their roles.
- Role Consistency Across Business Units: Standardizes access controls across different departments.
- Support for Zero Trust Architectures: Integrates with Zero Trust models by enforcing strict access controls.
Core Components of an RBAC System
- Roles: Defined based on job functions (e.g., Admin, Editor, Viewer).
- Permissions: Specific actions allowed (e.g., read, write, delete).
- Users: Individuals assigned to roles.
- Sessions: Temporary associations between users and roles.
- Constraints: Rules such as separation of duties and time-based access.
RBAC vs. ABAC vs. PBAC
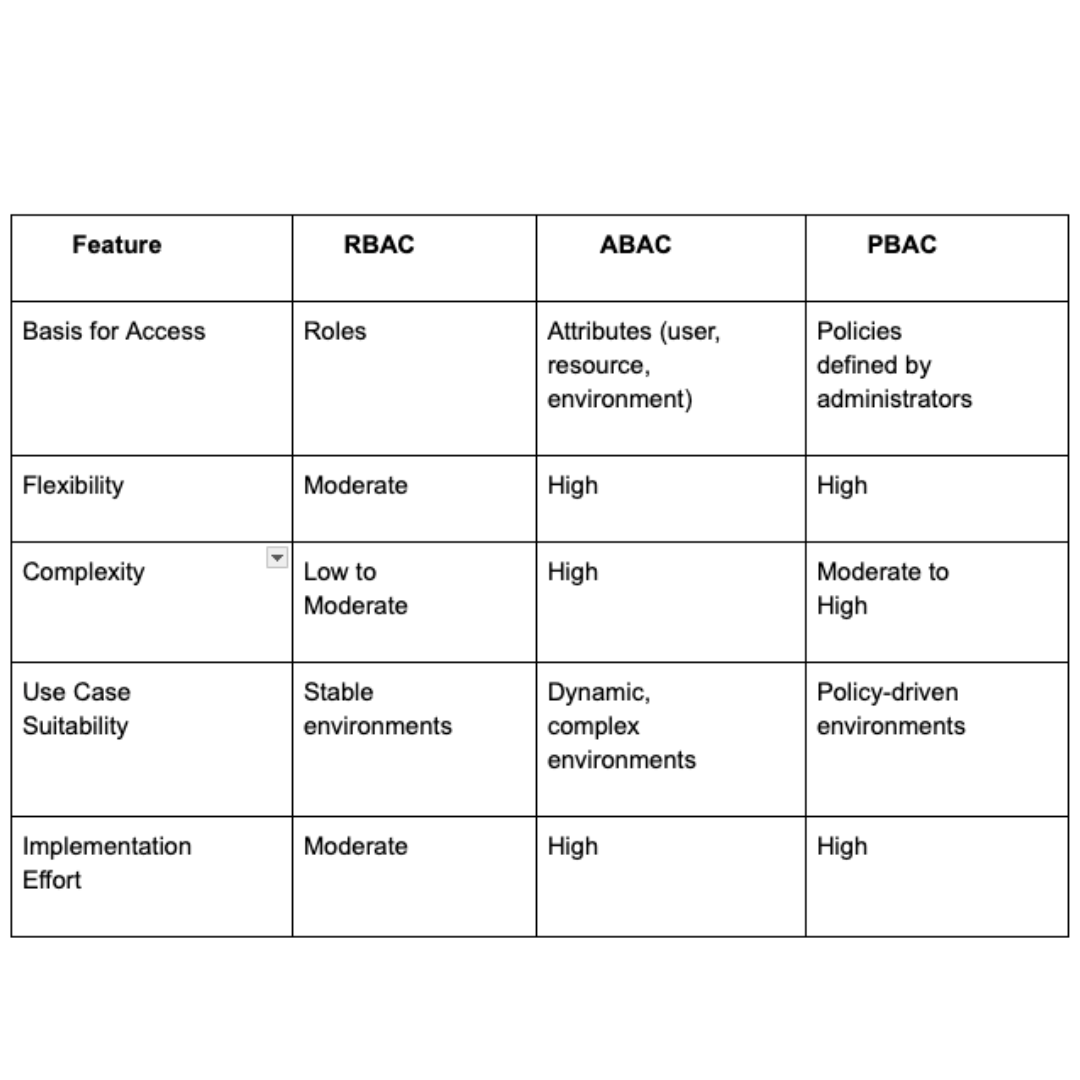
Step by Step Process
- Define Roles Clearly: Identify job functions and associated responsibilities.
- Identify Resources and Permissions: Determine what resources need protection and what actions are permissible.
- Assign Users to Roles: Map users to appropriate roles based on their job functions.
- Establish Policies and Rules: Set rules for role assignments and access permissions.
- Test and Simulate Access Controls: Ensure that the RBAC model works as intended.
- Monitor and Refine: Continuously monitor access and make necessary adjustments.
Best Practices:
- Conduct a Role Engineering Workshop: Engage stakeholders to define roles and permissions.
- Avoid “Role Explosion”: Keep the number of roles manageable to prevent complexity.
- Keep a Changelog of Access Rules: Maintain records of changes for auditing purposes.
Managing RBAC Over Time
- Periodic Access Reviews and Certifications: Regularly review roles and permissions to ensure they are up-to-date.
- Automating User Provisioning/Deprovisioning: Use automation tools to manage user access efficiently.
- Logging and Auditing: Implement logging to track access and changes.
- Integration with Identity and Access Management (IAM) Systems: Enhance RBAC by integrating with IAM solutions.
- Delegated Administration and Governance: Allow departments to manage their own roles within a centralized framework.
Real-World Use Cases
- Healthcare: Managing patient data access under HIPAA regulations.
- Finance: Enforcing SOX compliance for account access.
- Retail: Differentiating access between store-level, regional, and corporate users.
- Government: Controlling access based on clearance levels.
- Education: Managing access for admin, faculty, students, and guests.
RBAC in SaaS and Cloud Environments:
- Multi-tenant Cloud Apps: Ensuring tenant isolation and appropriate access.
- DevOps and Infrastructure as Code (IaC): Managing access to infrastructure components.
- Zero Trust Implementations: Enforcing strict access controls in a Zero Trust model.
RBAC Challenges and How to Overcome Them
- Role Bloat and Overlap: Regularly review and consolidate roles to prevent redundancy.
- Managing Exceptions: Implement exception handling processes for unique access needs.
- Onboarding Complexity: Simplify onboarding by tying user access to predefined roles, not individuals. Automate the provisioning of roles based on job title or department to reduce manual intervention and speed up new employee productivity.
- Legacy System Integration: Many older systems weren’t built with role-based access control in mind. To bridge the gap, consider using integration middleware or implementing RBAC at the network level with microsegmentation technologies — Illumio’s platform excels here by enabling granular policy enforcement without overhauling legacy applications.
- Employee Resistance to Change: Resistance typically stems from confusion or a perceived loss of access. Educate employees about the benefits of RBAC — especially its role in protecting sensitive data — and involve them in the role definition process to increase buy-in.
- Lack of Documentation: Maintain clear, centralized documentation of roles, associated permissions, and rationale. This ensures transparency, eases audits, and simplifies troubleshooting when access issues arise.
Future of RBAC
The traditional model of role-based access control is evolving rapidly in response to cloud-first architectures, remote work, and the rise of dynamic workloads. Here’s a look at what’s ahead:
AI-Assisted Role Mining and Recommendation
AI and machine learning are transforming RBAC by analyzing user behavior to identify patterns and recommend optimal role definitions. This can help reduce role sprawl and uncover hidden over-permissioned users — vital for enforcing the principle of least privilege.
Dynamic RBAC with Context-Aware Permissions
Future RBAC systems will factor in real-time context — like location, device health, or time of access — to dynamically adjust permissions. This bridges the gap between static RBAC and ABAC, enhancing both security and usability.
RBAC Within Zero Trust Frameworks
In Zero Trust architectures, identity is the new perimeter. RBAC plays a crucial role in enforcing least-privilege access policies based on user roles, device posture, and network segmentation. Illumio’s platform is purpose-built to enforce such policies at scale across hybrid environments.
Integration with Modern IAM Platforms and Cloud-Native Tools
RBAC is becoming a foundational feature within modern identity platforms such as Okta, Azure AD, and AWS IAM. Enterprises are adopting cloud-native tools that integrate seamlessly with CI/CD pipelines, DevOps tooling, and microservices, ensuring that RBAC remains relevant in dynamic environments.
Role-Based Access Control (RBAC) in Action: Insights from Illumio
Insight: Automate and Simplify with Illumio
In Illumio’s guide to policy automation, they highlight how automating policy generation based on roles and labels streamlines security management. This reduces human error, enforces consistent controls, and helps organizations avoid “policy overload” — a common challenge in distributed systems.
Positive Impact for Network Security Teams
- Reduces manual intervention and complexity.
- Prevents lateral movement in hybrid and multi-cloud networks.
- Enhances visibility into application and user flows.
- Accelerates compliance with standards like PCI-DSS, HIPAA, and NIST 800-53.
Role-Based Access Control FAQs
1. What’s the difference between RBAC and ABAC?
RBAC is based on predefined roles assigned to users. ABAC (Attribute-Based Access Control) uses attributes like department, time of day, or device type to make access decisions. ABAC is more dynamic, but also more complex to manage.
2. Can RBAC be used in cloud environments?
Absolutely. Most cloud providers (AWS, Azure, GCP) support RBAC natively for managing user and service access. RBAC is essential for securing Infrastructure-as-a-Service (IaaS), SaaS, and Platform-as-a-Service (PaaS) resources.
3. Is RBAC suitable for small businesses?
Yes. Even small teams benefit from RBAC by reducing chaos and ensuring that employees have access only to what they need. Start with basic roles and scale as the organization grows.
4. How often should access reviews be conducted?
At minimum, quarterly. Many organizations also conduct them during employee offboarding or when roles change. Automated tools can help trigger and document these reviews.
6. What is a role-based access control example?
In a healthcare setting, nurses might have access to patient vitals but not billing information, while admins can access both.
7. Can RBAC support Zero Trust architectures?
Yes. RBAC enforces least-privilege access, a core pillar of Zero Trust. Illumio’s segmentation tools integrate RBAC with network-level enforcement.
8. What are common pitfalls when implementing RBAC?
Role explosion, poor documentation, and lack of periodic reviews. Avoid this by starting small, maintaining governance, and automating wherever possible.
9. How is RBAC different from DAC and MAC?
DAC (Discretionary Access Control) lets data owners grant access. MAC (Mandatory Access Control) is enforced by policy administrators. RBAC strikes a balance — centralized, yet flexible.
10. Can RBAC manage access to APIs and microservices?
Yes. With proper IAM integration, RBAC can manage access at the service and resource level, especially when combined with service meshes or gateways.
Conclusion
Role-Based Access Control isn’t just a checkbox on your compliance list — it’s a strategic enabler of operational efficiency, regulatory alignment, and robust security.
RBAC helps organizations achieve Zero Trust access control, reduce insider risk, and prepare for the complexities of multi-cloud, hybrid, and remote-first ecosystems.
Now’s the time to take stock of your access control model. Whether you’re a startup or a global enterprise, the benefits of RBAC — when done right — are too significant to ignore.
.png)

.webp)
.webp)
.webp)
.webp)




%2520(1).webp)





