Vulnerability maps
Combine data from your vulnerability scanner with Illumio's real-time application dependency map to measure and reduce risk exposure


Reduce vulnerability exposure with Illumio
Outdated services and missing patches are notorious for inviting cyber threats in. Organizations are adopting Illumio Zero Trust Segmentation (ZTS) and its vulnerability mapping capabilities to reduce vulnerability exposure and stop the spread of inevitable breaches.
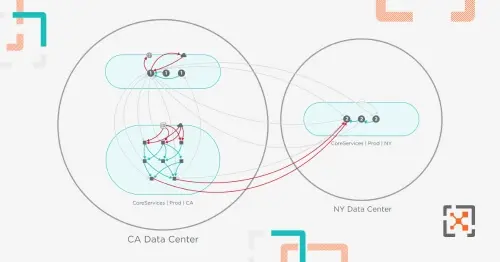
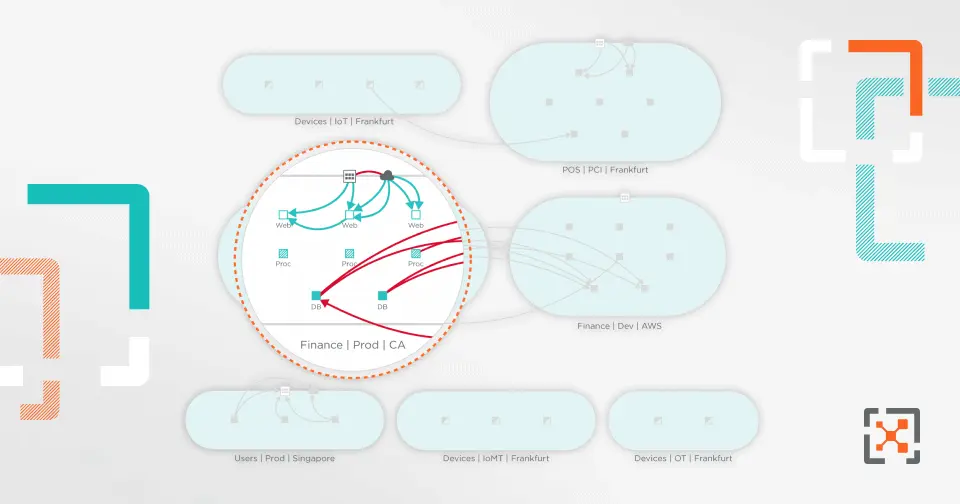
Vulnerability maps from Illumio integrate data from third-party scanners like Qualys, Rapid7, and Tenable with a real-time application dependency map to visualize, quantify, and minimize risk from vulnerabilities across your environment.
Rapidly tackle patch and vulnerability management
Gain a quick understanding of the level of risk in your application.
Use vulnerability mapping insights to prioritize patching decisions.
Apply segmentation policies as a compensating control if patching is not viable.
Know your attack surface with a Vulnerability Exposure Score
Vulnerability management solutions typically use the industry-standard Common Vulnerability Scoring System (CVSS) scores. While valuable, these scores do not take into account a workload’s connectivity relative to other workloads in your environment.
Vulnerability maps combine CVSS scoring with information on how many workloads can potentially connect with a vulnerable workload to calculate a Vulnerability Exposure Score (VES). Security and IT operations teams can better prioritize mitigation strategies based on exposure scores — implementing Zero Trust Segmentation to mitigate risk if patching is not an option.


Model policies and alert when a potential exploit is in process
Illumio Core also allows you to model and test segmentation as a compensating control, ensuring you do not break your applications. If traffic connects to a port with a known vulnerability, a traffic alert informs the security operations center (SOC) of the violation, including the vulnerability and severity context.