.png)
Application Dependency Mapping Demo
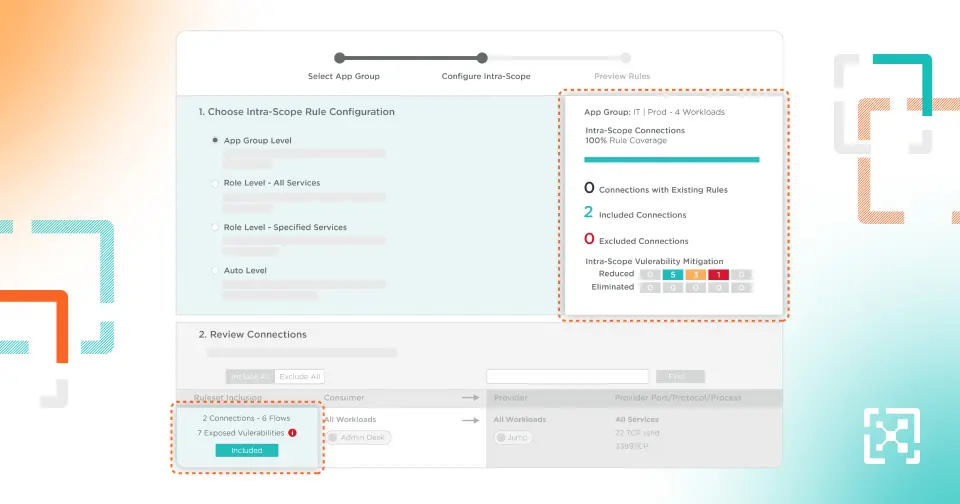
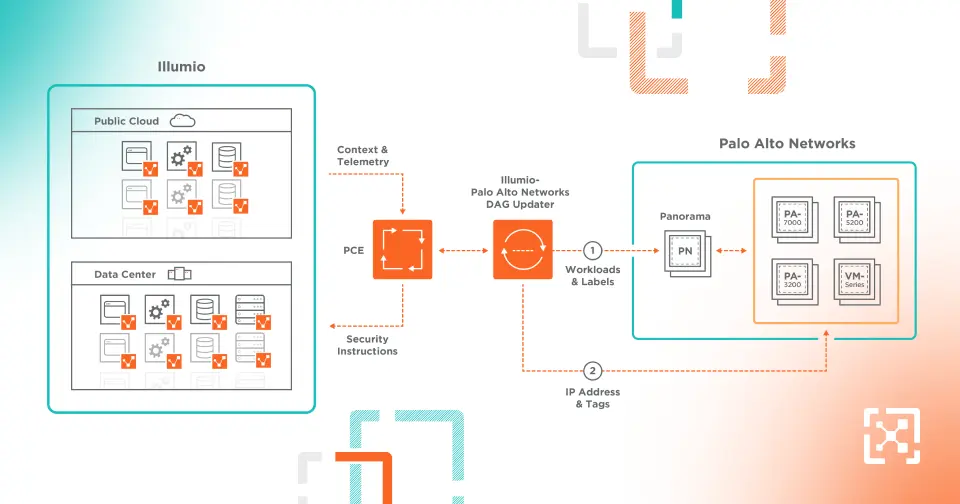
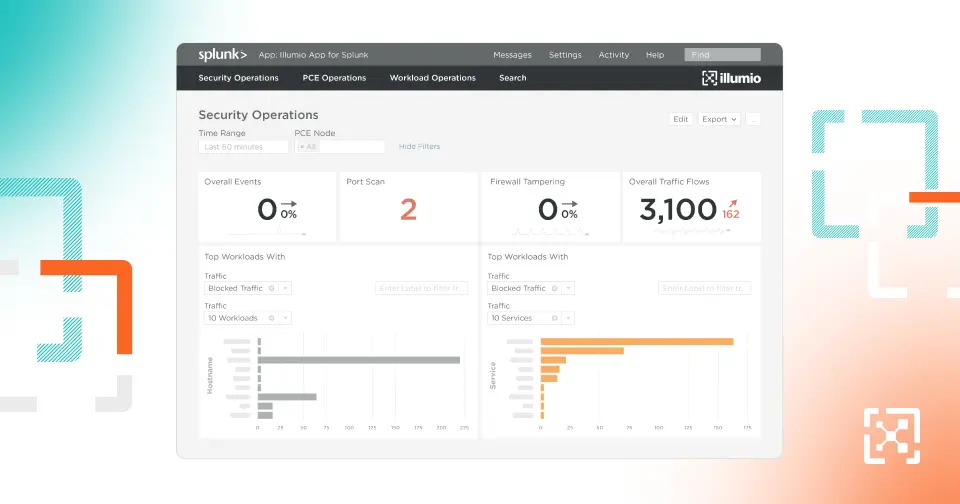
Illumio Core's real-time map provides visibility into application behavior and traffic flows across any data center and cloud.
Key benefits
Asset preview
No items found.

Gartner Hype Cycle for Cloud Security, 2021 – Representative Vendor

Forrester New Wave™ for Microsegmentation – Leader

CRN Partner Program Guide 2022 – Winner

CRN Partner Program Guide 2022 – Winner

Global InfoSec Awards - Publisher’s Choice

CRN Partner Program Guide 2022 – Winner
Assume Breach.
Minimize Impact.
Increase Resilience.
Ready to learn more about Zero Trust Segmentation?